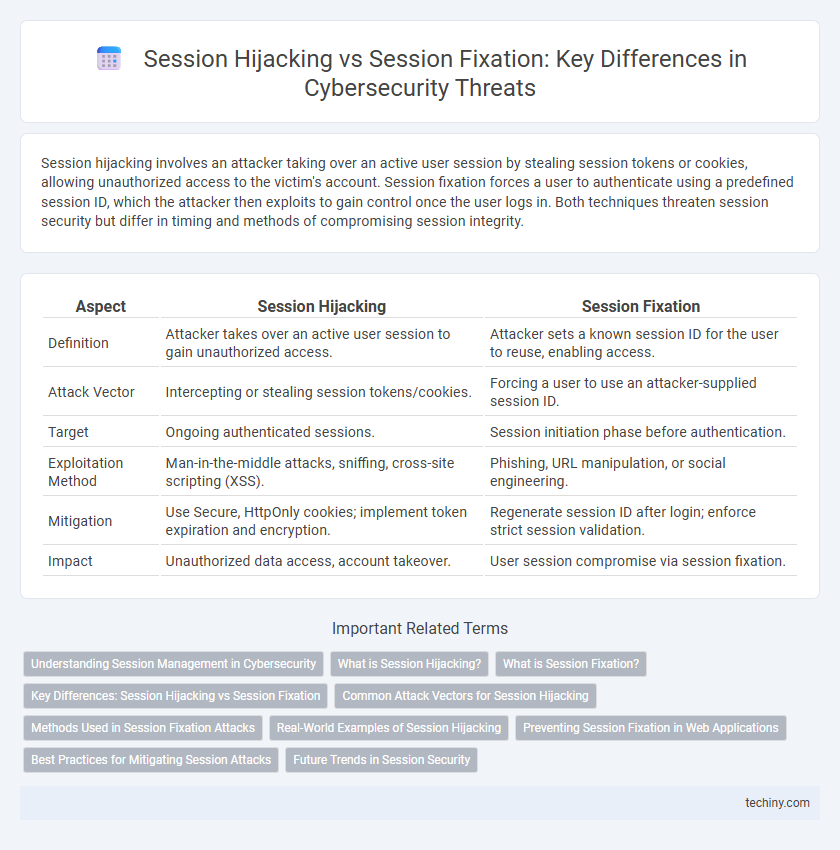
Session hijacking involves an attacker taking over an active user session by stealing session tokens or cookies, allowing unauthorized access to the victim's account. Session fixation forces a user to authenticate using a predefined session ID, which the attacker then exploits to gain control once the user logs in. Both techniques threaten session security but differ in timing and methods of compromising session integrity.
Table of Comparison
| Aspect | Session Hijacking | Session Fixation |
|---|---|---|
| Definition | Attacker takes over an active user session to gain unauthorized access. | Attacker sets a known session ID for the user to reuse, enabling access. |
| Attack Vector | Intercepting or stealing session tokens/cookies. | Forcing a user to use an attacker-supplied session ID. |
| Target | Ongoing authenticated sessions. | Session initiation phase before authentication. |
| Exploitation Method | Man-in-the-middle attacks, sniffing, cross-site scripting (XSS). | Phishing, URL manipulation, or social engineering. |
| Mitigation | Use Secure, HttpOnly cookies; implement token expiration and encryption. | Regenerate session ID after login; enforce strict session validation. |
| Impact | Unauthorized data access, account takeover. | User session compromise via session fixation. |
Understanding Session Management in Cybersecurity
Session Hijacking exploits vulnerabilities to take over an active user session by stealing session tokens, while Session Fixation tricks a user into using a predetermined session ID controlled by an attacker. Effective session management in cybersecurity involves implementing secure cookie attributes, regenerating session IDs after login, and enforcing timeout policies to prevent unauthorized access. Understanding these distinctions helps in designing defenses against common session-based attacks in modern web applications.
What is Session Hijacking?
Session hijacking is a cyberattack where an attacker intercepts or takes over a valid user session to gain unauthorized access to sensitive information or systems. This exploit involves stealing session tokens or session IDs, allowing attackers to impersonate legitimate users without needing their credentials. Effective defense mechanisms include encryption, secure cookie handling, and continuous session monitoring to detect anomalies.
What is Session Fixation?
Session Fixation is a cybersecurity attack where an attacker sets a user's session ID to a known value, allowing them to hijack the valid session after the user logs in. Unlike Session Hijacking, which involves stealing an active session ID, Session Fixation manipulates the session ID before authentication occurs. Protecting against Session Fixation requires regenerating session IDs upon successful login and implementing secure cookie attributes.
Key Differences: Session Hijacking vs Session Fixation
Session Hijacking involves an attacker intercepting or taking over an active user session by stealing session tokens, whereas Session Fixation tricks a user into using a known session ID set by the attacker before login. The key difference lies in control timing; Session Hijacking occurs after a session is established, while Session Fixation involves predefining the session prior to authentication. Both exploit session management vulnerabilities but require distinct attack vectors and mitigation strategies.
Common Attack Vectors for Session Hijacking
Session hijacking commonly exploits vulnerabilities such as unsecured Wi-Fi networks, cross-site scripting (XSS) attacks, and session token theft via malware or phishing schemes. Attackers intercept or predict valid session IDs, enabling unauthorized access to user sessions and sensitive data. Techniques like packet sniffing, man-in-the-middle (MITM) attacks, and cookie poisoning are prevalent vectors facilitating session hijacking breaches.
Methods Used in Session Fixation Attacks
Session fixation attacks involve an attacker setting or manipulating a user's session ID before authentication, exploiting methods such as URL parameter injection, HTTP request header manipulation, and cross-site scripting (XSS) to fixate the session identifier. Attackers often deliver session IDs via phishing emails or malicious links, coercing the victim into authenticating with the predetermined session ID. Proper session management techniques, including regenerating session IDs upon login and using secure cookies, are essential to mitigate these fixation methods.
Real-World Examples of Session Hijacking
Session hijacking involves cybercriminals exploiting valid user sessions to gain unauthorized access, as seen in the 2013 Yahoo data breach where attackers used stolen session cookies to infiltrate accounts without passwords. In contrast, session fixation attacks manipulate a known session ID before user authentication, but do not replicate the stealth seen in hijacking cases like the 2016 United Airlines breach involving intercepted session tokens. Real-world session hijacking often leverages unsecured Wi-Fi or cross-site scripting vulnerabilities, emphasizing the critical need for encrypted connections and robust session management.
Preventing Session Fixation in Web Applications
Preventing session fixation in web applications involves regenerating session IDs after successful authentication to ensure attackers cannot set a valid session ID prior to login. Implementing secure cookie attributes such as HttpOnly and Secure, alongside strict session expiration policies, further protects against session fixation attacks. Using token binding and monitoring for suspicious session activities also enhances defense against malicious session takeover attempts.
Best Practices for Mitigating Session Attacks
Implementing secure cookie attributes like HttpOnly and Secure significantly reduces the risk of session hijacking by preventing unauthorized script access and ensuring cookies are transmitted only over HTTPS. Regularly regenerating session IDs after user authentication mitigates session fixation attacks by invalidating attackers' predefined session identifiers. Utilizing multi-factor authentication and monitoring anomalous session activities further strengthens defenses against session-based cyber threats.
Future Trends in Session Security
Emerging session security trends emphasize advanced machine learning algorithms to detect and prevent session hijacking by analyzing behavioral anomalies in real-time. Blockchain-based authentication mechanisms are gaining traction to counter session fixation attacks by ensuring immutable session tokens and enhancing transparency. The integration of zero-trust architectures further strengthens session security by continuously validating user identity and device posture throughout the session lifecycle.
Session Hijacking vs Session Fixation Infographic
 techiny.com
techiny.com