Patch management involves the systematic process of identifying, acquiring, testing, and installing software updates to fix security flaws and improve system functionality. Vulnerability management encompasses the broader cycle of discovering, evaluating, prioritizing, and mitigating security weaknesses across an organization's IT environment. Effective cybersecurity demands integrating both patch management and vulnerability management to reduce risk and strengthen overall defense strategies.
Table of Comparison
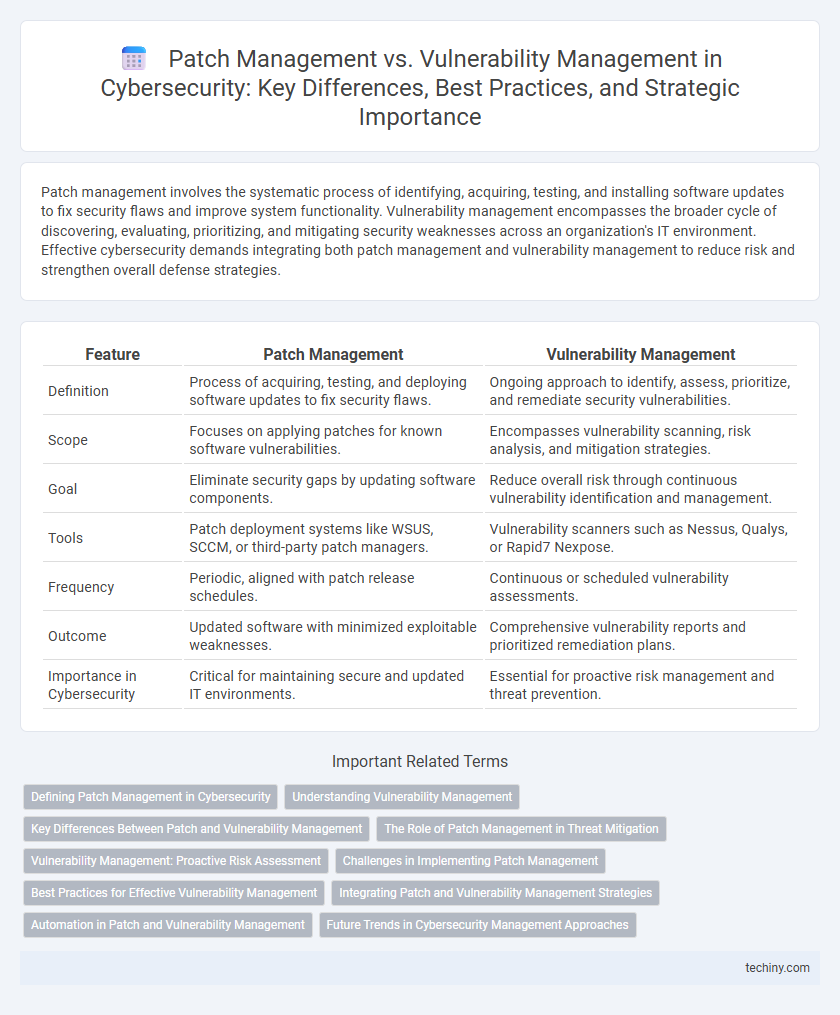
| Feature | Patch Management | Vulnerability Management |
|---|---|---|
| Definition | Process of acquiring, testing, and deploying software updates to fix security flaws. | Ongoing approach to identify, assess, prioritize, and remediate security vulnerabilities. |
| Scope | Focuses on applying patches for known software vulnerabilities. | Encompasses vulnerability scanning, risk analysis, and mitigation strategies. |
| Goal | Eliminate security gaps by updating software components. | Reduce overall risk through continuous vulnerability identification and management. |
| Tools | Patch deployment systems like WSUS, SCCM, or third-party patch managers. | Vulnerability scanners such as Nessus, Qualys, or Rapid7 Nexpose. |
| Frequency | Periodic, aligned with patch release schedules. | Continuous or scheduled vulnerability assessments. |
| Outcome | Updated software with minimized exploitable weaknesses. | Comprehensive vulnerability reports and prioritized remediation plans. |
| Importance in Cybersecurity | Critical for maintaining secure and updated IT environments. | Essential for proactive risk management and threat prevention. |
Defining Patch Management in Cybersecurity
Patch management in cybersecurity refers to the systematic process of identifying, acquiring, testing, and deploying software updates or patches to fix vulnerabilities, improve functionality, and enhance security across IT systems. This process helps prevent exploitation of known security flaws by attackers, thereby reducing the organization's risk exposure. Effective patch management involves maintaining up-to-date inventories of software assets and applying patches promptly to mitigate potential threats.
Understanding Vulnerability Management
Vulnerability management involves the continuous process of identifying, assessing, and prioritizing security weaknesses across an organization's IT environment to reduce risk exposure. It leverages tools such as vulnerability scanners, threat intelligence, and risk assessments to detect potential entry points for cyberattacks before exploitation. Unlike patch management, which focuses on deploying software updates, vulnerability management provides a comprehensive risk-based strategy to address both known and unknown security gaps.
Key Differences Between Patch and Vulnerability Management
Patch management involves the systematic process of identifying, acquiring, testing, and deploying software updates to fix security flaws and improve system functionality. Vulnerability management encompasses the broader practice of discovering, assessing, prioritizing, and mitigating security weaknesses across an organization's IT environment, including but not limited to patching. Key differences include patch management's focus on applying specific fixes, whereas vulnerability management addresses the overall risk posture through continuous monitoring and remediation strategies.
The Role of Patch Management in Threat Mitigation
Patch management plays a critical role in threat mitigation by systematically identifying, acquiring, testing, and deploying software updates to fix known vulnerabilities that cyber attackers exploit. Effective patch management reduces the attack surface by closing security gaps in operating systems, applications, and firmware, thereby preventing unauthorized access and data breaches. Integrating patch management within a comprehensive vulnerability management program enhances organizational resilience against emerging threats and compliance with cybersecurity standards.
Vulnerability Management: Proactive Risk Assessment
Vulnerability Management emphasizes proactive risk assessment by continuously identifying, evaluating, and prioritizing security weaknesses to prevent potential breaches. This process involves automated scanning tools, real-time threat intelligence, and risk-based prioritization to ensure high-risk vulnerabilities are remediated swiftly. Effective vulnerability management reduces exposure and strengthens organizational security posture beyond the reactive nature of patch management.
Challenges in Implementing Patch Management
Implementing patch management faces challenges such as the complexity of tracking and prioritizing numerous patches across diverse systems and software, which increases the risk of missed updates and security breaches. Limited resources and downtime constraints often delay patch deployment, leaving vulnerabilities exposed to cyber threats. Additionally, compatibility issues with existing infrastructure and the potential for patch-induced system disruptions complicate timely and effective patch implementation.
Best Practices for Effective Vulnerability Management
Effective vulnerability management relies on continuous asset discovery, prioritization of vulnerabilities based on risk, and timely remediation through patch deployment. Integrating automated scanning tools with a robust patch management system ensures swift identification and mitigation of security flaws. Comprehensive reporting and collaboration across IT and security teams enhance accuracy and speed in addressing critical vulnerabilities.
Integrating Patch and Vulnerability Management Strategies
Integrating patch management and vulnerability management strategies enhances organizational cybersecurity by enabling comprehensive risk mitigation through continuous identification, assessment, and timely remediation of security flaws. Efficient synchronization of vulnerability scanning with patch deployment ensures prioritization of critical threats based on real-time risk analytics, reducing exposure windows and preventing exploitation. Leveraging automated tools for integrating these processes accelerates patch rollouts and vulnerability resolution, optimizing resource allocation and compliance with industry security standards.
Automation in Patch and Vulnerability Management
Automation in patch management accelerates the identification, testing, and deployment of software updates, significantly reducing the window of exposure to known vulnerabilities. In vulnerability management, automated scanning tools continuously detect, categorize, and prioritize security flaws, enabling proactive risk mitigation. Integrating automation across both domains enhances operational efficiency, reduces human error, and fortifies organizational defenses against evolving cyber threats.
Future Trends in Cybersecurity Management Approaches
Future trends in cybersecurity management emphasize the convergence of patch management and vulnerability management through integrated platforms that leverage AI-driven analytics to predict and prioritize threats. Automation and continuous monitoring enhance real-time response capabilities, reducing the window of exposure to exploits. Advanced threat intelligence and adaptive security frameworks are shaping proactive defense strategies, optimizing resource allocation and minimizing risk across complex IT environments.
Patch Management vs Vulnerability Management Infographic
 techiny.com
techiny.com