Spyware covertly collects user information without consent, posing serious privacy risks by tracking keystrokes, browsing habits, and personal data. Adware primarily displays unwanted advertisements, often slowing down devices and disrupting user experience, but usually does not steal sensitive information. Both types of malicious software can degrade system performance, making robust cybersecurity measures essential for protection.
Table of Comparison
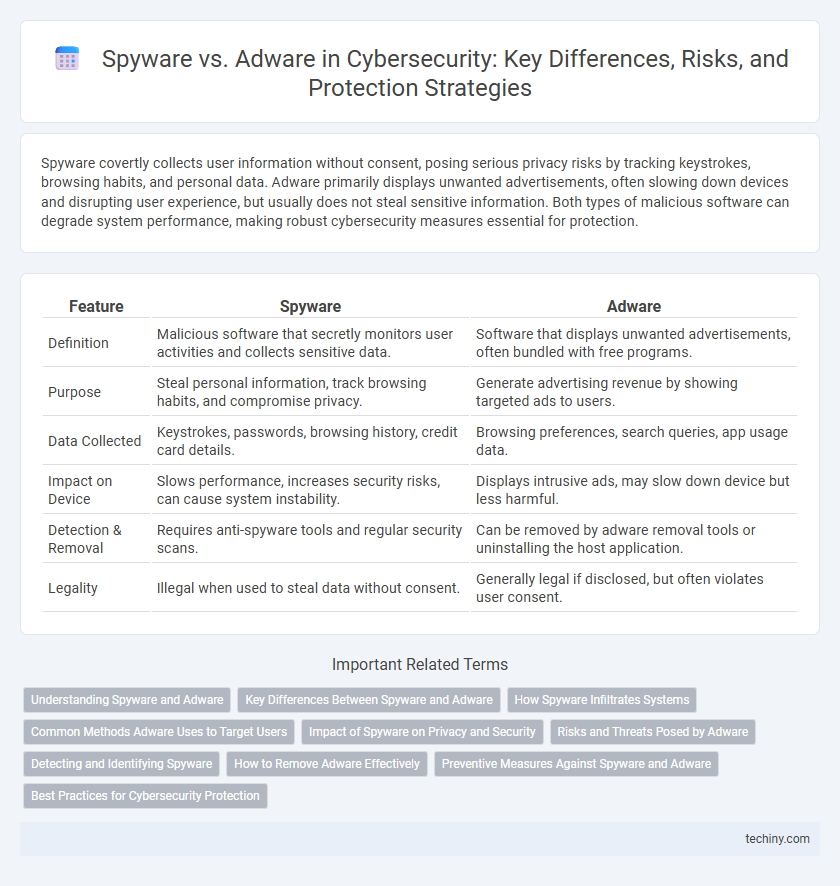
| Feature | Spyware | Adware |
|---|---|---|
| Definition | Malicious software that secretly monitors user activities and collects sensitive data. | Software that displays unwanted advertisements, often bundled with free programs. |
| Purpose | Steal personal information, track browsing habits, and compromise privacy. | Generate advertising revenue by showing targeted ads to users. |
| Data Collected | Keystrokes, passwords, browsing history, credit card details. | Browsing preferences, search queries, app usage data. |
| Impact on Device | Slows performance, increases security risks, can cause system instability. | Displays intrusive ads, may slow down device but less harmful. |
| Detection & Removal | Requires anti-spyware tools and regular security scans. | Can be removed by adware removal tools or uninstalling the host application. |
| Legality | Illegal when used to steal data without consent. | Generally legal if disclosed, but often violates user consent. |
Understanding Spyware and Adware
Spyware is malicious software designed to secretly monitor user activities, steal sensitive information, and compromise privacy, often installed without consent. Adware, while also intrusive, primarily focuses on displaying unwanted advertisements and tracking browsing behavior to generate revenue, typically with less harmful intent than spyware. Understanding the distinct behaviors and risks of spyware and adware is crucial for effective cybersecurity measures and protecting personal data.
Key Differences Between Spyware and Adware
Spyware stealthily collects sensitive information from users without consent, often monitoring keystrokes, browsing habits, and personal data, whereas adware primarily displays unwanted advertisements to generate revenue rather than steal data. Spyware operates covertly to compromise privacy and security, while adware is generally intrusive but less harmful, focusing on persistent ad delivery. Understanding these distinctions is critical for deploying effective cybersecurity measures and protecting user data privacy.
How Spyware Infiltrates Systems
Spyware infiltrates systems primarily through deceptive methods such as phishing emails, malicious downloads, and exploiting software vulnerabilities. Once installed, it covertly monitors user activity, capturing sensitive data like passwords and financial information without consent. Unlike adware, which focuses on displaying unwanted advertisements, spyware operates stealthily to gather intelligence for cybercriminals.
Common Methods Adware Uses to Target Users
Adware commonly targets users through browser hijacking, injecting unwanted advertisements into web pages, and bundling with free software downloads to install without explicit consent. It exploits tracking cookies and browser history to deliver personalized ads, often slowing down system performance and compromising user privacy. These techniques distinguish adware from spyware, which primarily focuses on stealth data extraction.
Impact of Spyware on Privacy and Security
Spyware significantly compromises privacy by covertly collecting sensitive data such as passwords, browsing habits, and financial information without user consent. Its presence can lead to identity theft, unauthorized access to personal accounts, and severe security breaches. Unlike adware, which primarily displays unwanted advertisements, spyware operates in the background to exploit confidential information, making it a critical threat to cybersecurity.
Risks and Threats Posed by Adware
Adware poses significant risks by collecting sensitive user data, including browsing habits and personal information, often without explicit consent. This unauthorized data harvesting can lead to privacy breaches and targeted cyberattacks, increasing vulnerability to phishing and identity theft. Unlike spyware, adware primarily disrupts user experience through intrusive ads but shares similar threats by enabling malicious actors to exploit gathered information for fraudulent activities.
Detecting and Identifying Spyware
Detecting and identifying spyware involves monitoring unusual system behavior, such as unauthorized data transmissions and significant slowdowns in device performance. Key indicators include unexpected pop-ups, changes in browser settings, and the presence of unknown processes in task managers or antivirus scans. Advanced cybersecurity tools use heuristic analysis and signature-based detection to isolate spyware from legitimate adware, ensuring precise threat mitigation.
How to Remove Adware Effectively
Removing adware effectively involves using specialized anti-malware tools designed to detect and eliminate potentially unwanted programs embedded in browsers or system files. Manual removal requires uninstalling suspicious applications, clearing browser extensions, resetting browser settings, and deleting temporary files that adware exploits. Regularly updating security software and practicing cautious browsing habits significantly reduce the risk of adware reinfection and maintain system integrity.
Preventive Measures Against Spyware and Adware
Effective preventive measures against spyware and adware include regularly updating antivirus software and employing real-time malware scanning to detect and block malicious threats. Implementing strict browser security settings, avoiding suspicious downloads, and using ad blockers help minimize exposure to adware and spyware infections. Conducting user education on phishing scams and enabling firewall protection further strengthens defenses against intrusive and harmful software.
Best Practices for Cybersecurity Protection
Spyware and adware both pose significant cybersecurity risks by compromising user privacy and system performance through unauthorized data collection and intrusive advertisements. Best practices for cybersecurity protection include regularly updating antivirus software, using strong, unique passwords, and enabling multi-factor authentication to mitigate potential breaches caused by these malicious programs. Implementing network firewalls and educating users on recognizing phishing attempts further strengthens defenses against spyware and adware infections.
Spyware vs adware Infographic
 techiny.com
techiny.com