Endpoint security protects individual devices such as laptops, smartphones, and tablets from cyber threats by securing entry points directly accessed by users. Network security focuses on safeguarding the entire network infrastructure, including routers, switches, and firewalls, to prevent unauthorized access and attacks on data as it travels across the network. Combining endpoint security with network security creates a comprehensive defense strategy that minimizes vulnerabilities and enhances overall cybersecurity resilience.
Table of Comparison
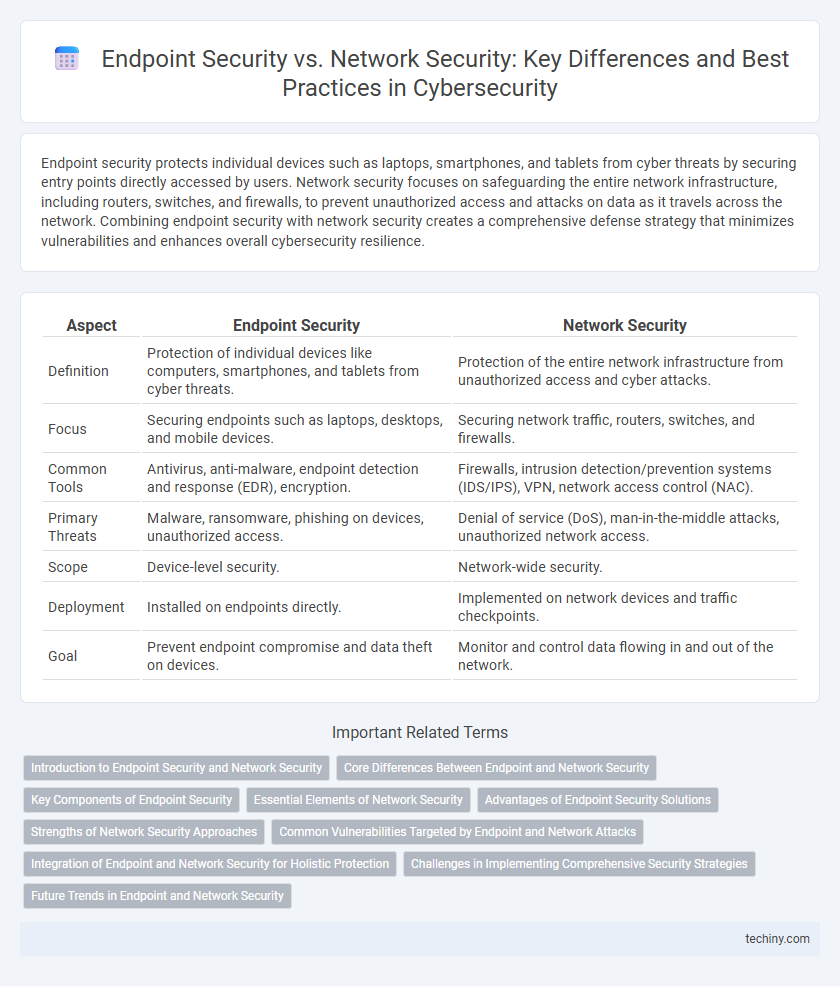
| Aspect | Endpoint Security | Network Security |
|---|---|---|
| Definition | Protection of individual devices like computers, smartphones, and tablets from cyber threats. | Protection of the entire network infrastructure from unauthorized access and cyber attacks. |
| Focus | Securing endpoints such as laptops, desktops, and mobile devices. | Securing network traffic, routers, switches, and firewalls. |
| Common Tools | Antivirus, anti-malware, endpoint detection and response (EDR), encryption. | Firewalls, intrusion detection/prevention systems (IDS/IPS), VPN, network access control (NAC). |
| Primary Threats | Malware, ransomware, phishing on devices, unauthorized access. | Denial of service (DoS), man-in-the-middle attacks, unauthorized network access. |
| Scope | Device-level security. | Network-wide security. |
| Deployment | Installed on endpoints directly. | Implemented on network devices and traffic checkpoints. |
| Goal | Prevent endpoint compromise and data theft on devices. | Monitor and control data flowing in and out of the network. |
Introduction to Endpoint Security and Network Security
Endpoint security protects individual devices such as laptops, smartphones, and tablets from cyber threats by implementing antivirus software, encryption, and intrusion detection on each device. Network security safeguards the overall infrastructure by controlling access, monitoring traffic, and preventing unauthorized intrusions within a corporate network through firewalls, virtual private networks (VPNs), and intrusion prevention systems (IPS). Both endpoint and network security are critical components of a comprehensive cybersecurity strategy to mitigate risks and ensure data integrity across all access points.
Core Differences Between Endpoint and Network Security
Endpoint security protects individual devices such as laptops, smartphones, and desktops by securing access points from malware, ransomware, and unauthorized access. Network security focuses on safeguarding the entire network infrastructure--routers, switches, and firewalls--by monitoring and controlling incoming and outgoing traffic to prevent breaches and attacks. The core difference lies in endpoint security targeting device-level vulnerabilities, while network security addresses broader traffic and perimeter defense mechanisms.
Key Components of Endpoint Security
Endpoint security centers on protecting individual devices such as laptops, smartphones, and desktops through key components like antivirus software, intrusion detection systems, and data encryption. Advanced endpoint security also includes behavioral analysis, application control, and device management to prevent unauthorized access and data breaches. These elements work together to secure endpoints against malware, ransomware, and insider threats, ensuring comprehensive device-level protection within the broader cybersecurity infrastructure.
Essential Elements of Network Security
Network security involves critical elements such as firewalls, intrusion detection systems (IDS), and encryption protocols to protect data during transmission across networks. Robust network security also includes access control measures, secure VPNs, and continuous monitoring to identify and mitigate potential threats. These components work together to prevent unauthorized access, data breaches, and cyberattacks targeting network infrastructure.
Advantages of Endpoint Security Solutions
Endpoint security solutions provide granular protection by directly securing individual devices such as laptops, smartphones, and desktops, reducing vulnerabilities introduced by remote work and mobile access. These solutions offer real-time threat detection and response capabilities, enabling rapid isolation and remediation of malware or unauthorized access on endpoints. Endpoint security also enhances data protection through encryption and access controls, minimizing the risk of data breaches originating from compromised devices.
Strengths of Network Security Approaches
Network security approaches excel at safeguarding data exchanges across entire organizational infrastructures by implementing firewalls, intrusion detection systems, and encrypted communication protocols. They provide comprehensive visibility and control over traffic patterns, enabling rapid identification and mitigation of threats such as DDoS attacks and unauthorized access attempts. Robust segmentation and access control policies enhance protection against lateral movement, reducing the risk of widespread breaches within corporate networks.
Common Vulnerabilities Targeted by Endpoint and Network Attacks
Endpoint attacks frequently exploit vulnerabilities such as outdated software, weak authentication protocols, and unpatched operating systems, enabling malware infiltration and data breaches. Network security threats typically target misconfigured firewalls, insecure network protocols, and inadequate intrusion detection systems, facilitating unauthorized access and data interception. Effective cybersecurity strategies must address both sets of vulnerabilities to protect assets from ransomware, phishing, and advanced persistent threats.
Integration of Endpoint and Network Security for Holistic Protection
Integrating endpoint security with network security creates a comprehensive defense system that detects and mitigates threats at both device and network levels. This unified approach enhances real-time threat intelligence sharing, enabling faster response to sophisticated cyberattacks such as advanced persistent threats (APTs) and zero-day exploits. Leveraging endpoint detection and response (EDR) alongside network intrusion detection systems (NIDS) optimizes overall security posture by providing visibility, control, and automated threat remediation across the entire IT infrastructure.
Challenges in Implementing Comprehensive Security Strategies
Implementing comprehensive security strategies faces challenges such as the complexity of integrating endpoint security with network security tools, which often operate on different protocols and management frameworks. Endpoint security must address diverse device types and user behaviors, creating gaps when coordinated with network-level defenses that monitor traffic patterns and access controls. Balancing resource allocation between protecting individual devices and overseeing network-wide threats demands continuous updates, skilled personnel, and effective communication across security domains.
Future Trends in Endpoint and Network Security
Future trends in endpoint security emphasize artificial intelligence-driven threat detection and zero-trust architecture to mitigate increasingly sophisticated cyberattacks targeting individual devices. Network security advancements prioritize software-defined networking (SDN) and encrypted traffic analysis to enhance real-time response and protect against complex, distributed threats. Integration of endpoint and network security through unified threat management platforms offers enhanced visibility and automated defense mechanisms against evolving cyber threats.
Endpoint Security vs Network Security Infographic
 techiny.com
techiny.com