CVE (Common Vulnerabilities and Exposures) provides a standardized identifier for publicly known cybersecurity vulnerabilities, enabling consistent tracking and communication across platforms. CWE (Common Weakness Enumeration) categorizes the root causes and types of software weaknesses that lead to vulnerabilities, helping developers understand and prevent common coding errors. Together, CVE highlights specific security issues while CWE offers insight into underlying software flaws, making both essential for comprehensive vulnerability management.
Table of Comparison
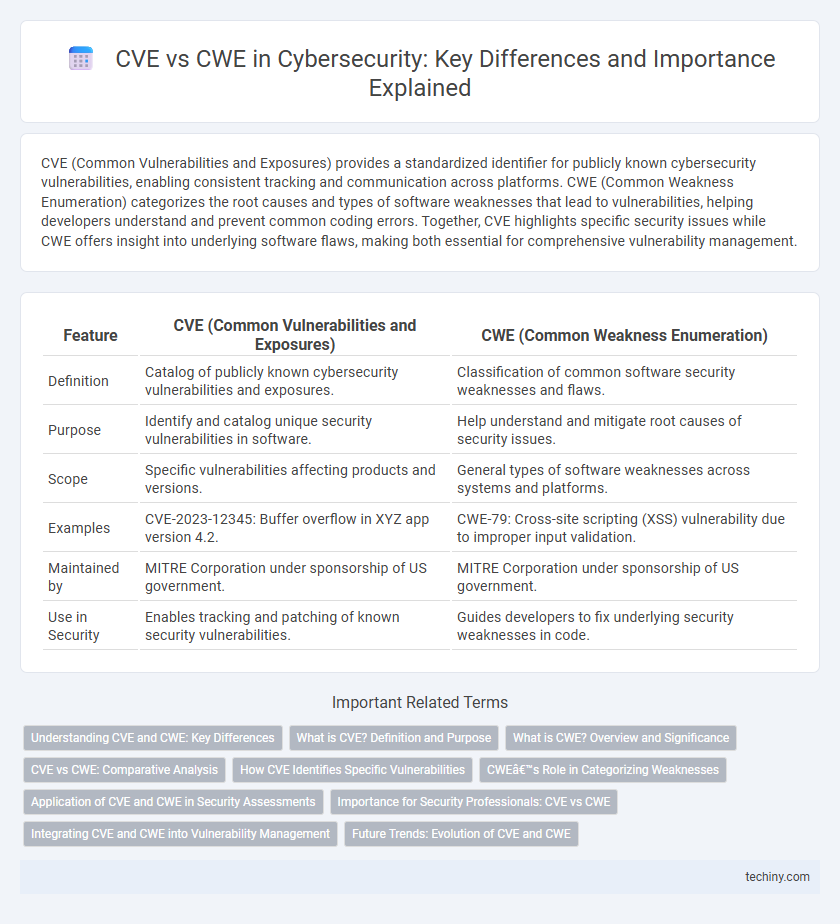
| Feature | CVE (Common Vulnerabilities and Exposures) | CWE (Common Weakness Enumeration) |
|---|---|---|
| Definition | Catalog of publicly known cybersecurity vulnerabilities and exposures. | Classification of common software security weaknesses and flaws. |
| Purpose | Identify and catalog unique security vulnerabilities in software. | Help understand and mitigate root causes of security issues. |
| Scope | Specific vulnerabilities affecting products and versions. | General types of software weaknesses across systems and platforms. |
| Examples | CVE-2023-12345: Buffer overflow in XYZ app version 4.2. | CWE-79: Cross-site scripting (XSS) vulnerability due to improper input validation. |
| Maintained by | MITRE Corporation under sponsorship of US government. | MITRE Corporation under sponsorship of US government. |
| Use in Security | Enables tracking and patching of known security vulnerabilities. | Guides developers to fix underlying security weaknesses in code. |
Understanding CVE and CWE: Key Differences
CVE (Common Vulnerabilities and Exposures) identifies and catalogs specific cybersecurity vulnerabilities with unique identifiers, facilitating precise tracking and remediation. CWE (Common Weakness Enumeration) categorizes the underlying software weaknesses or coding errors that often lead to vulnerabilities, helping developers understand root causes and prevent future issues. Understanding the key differences between CVE and CWE enhances vulnerability management by linking concrete security flaws with their broader systemic causes.
What is CVE? Definition and Purpose
CVE (Common Vulnerabilities and Exposures) is a standardized identifier for publicly known cybersecurity vulnerabilities and exposures. It serves as a universal reference that allows security professionals, researchers, and tools to communicate clearly and efficiently about specific vulnerabilities. The primary purpose of CVE is to provide a consistent framework for tracking and addressing security risks across multiple platforms and systems.
What is CWE? Overview and Significance
CWE (Common Weakness Enumeration) is a comprehensive catalog of software and hardware weaknesses that lead to vulnerabilities, maintained by MITRE Corporation to support secure coding and risk management. It provides a standardized classification system enabling developers and security professionals to identify, categorize, and address root causes of security flaws, thus preventing CVEs (Common Vulnerabilities and Exposures). The significance of CWE lies in its role as a foundational resource for improving software security by enhancing vulnerability detection, mitigation strategies, and fostering industry-wide communication on weakness patterns.
CVE vs CWE: Comparative Analysis
CVE (Common Vulnerabilities and Exposures) provides a standardized identifier for publicly known cybersecurity vulnerabilities, enabling consistent tracking and management across platforms. CWE (Common Weakness Enumeration) categorizes software weaknesses and coding errors that can lead to vulnerabilities, facilitating improved software development and security assessment. Comparing CVE and CWE reveals that CVE focuses on specific, identified vulnerabilities while CWE addresses underlying systemic weaknesses that cause those vulnerabilities, making both essential for comprehensive cybersecurity risk management.
How CVE Identifies Specific Vulnerabilities
CVE (Common Vulnerabilities and Exposures) uniquely identifies specific security vulnerabilities through a standardized numbering system, enabling consistent reference across cybersecurity tools and databases. Each CVE entry details a distinct flaw, including information such as affected software, vulnerability type, and potential impact, facilitating precise vulnerability management. This specificity contrasts with CWE (Common Weakness Enumeration), which categorizes general classes of software weaknesses rather than individual instances.
CWE’s Role in Categorizing Weaknesses
CWE (Common Weakness Enumeration) plays a crucial role in categorizing software and system weaknesses by providing a comprehensive taxonomy of security flaws, enabling organizations to prioritize mitigation strategies effectively. Unlike CVE (Common Vulnerabilities and Exposures), which identifies specific instances of vulnerabilities, CWE focuses on the underlying root causes and patterns that lead to security issues. This structured classification aids developers and security professionals in understanding common coding errors and design flaws, ultimately improving secure software development and risk management.
Application of CVE and CWE in Security Assessments
CVE (Common Vulnerabilities and Exposures) provides a standardized list of publicly known cybersecurity vulnerabilities, enabling security professionals to identify and prioritize specific threats in security assessments. CWE (Common Weakness Enumeration) focuses on the root causes of software vulnerabilities, allowing for more effective threat modeling and secure coding practices during application development and review. Applying CVE and CWE together enhances security assessments by linking concrete vulnerabilities to underlying weaknesses, improving both detection accuracy and remediation strategies.
Importance for Security Professionals: CVE vs CWE
CVE (Common Vulnerabilities and Exposures) provides unique identifiers for publicly known cybersecurity vulnerabilities, enabling security professionals to track and prioritize threat remediation efficiently. CWE (Common Weakness Enumeration) categorizes the root causes or software weaknesses that lead to vulnerabilities, helping security teams understand and mitigate systemic security flaws during development. Mastery of both CVE and CWE frameworks is critical for comprehensive vulnerability management and enhancing organizational security posture.
Integrating CVE and CWE into Vulnerability Management
Integrating CVE (Common Vulnerabilities and Exposures) and CWE (Common Weakness Enumeration) into vulnerability management enhances the precision of identifying and prioritizing security risks by combining specific vulnerability data with underlying software weakness patterns. CVE provides unique identifiers for known vulnerabilities, enabling standardized tracking and remediation across systems, while CWE categorizes the root causes, facilitating deeper analysis and prevention strategies. Leveraging both frameworks streamlines vulnerability assessment workflows, improves threat intelligence correlation, and strengthens overall cybersecurity posture.
Future Trends: Evolution of CVE and CWE
The future evolution of CVE (Common Vulnerabilities and Exposures) and CWE (Common Weakness Enumeration) emphasizes integrating advanced machine learning algorithms and real-time data analytics to enhance vulnerability identification and classification accuracy. Expect increased collaboration between CVE and CWE frameworks to provide more precise mapping of weaknesses to exposures, enabling more efficient risk management and mitigation strategies. Enhanced automation and ecosystem interoperability will drive the continuous update of CVE and CWE databases, reflecting emerging cyber threats and security weaknesses in dynamic environments.
CVE vs CWE Infographic
 techiny.com
techiny.com