A Trojan horse disguises itself as legitimate software to trick users into installing malware, often granting attackers unauthorized access or stealing sensitive data. In contrast, a rootkit operates stealthily at the system's core, enabling persistent control by hiding its presence and activities from detection tools. Understanding the differences between these threats is crucial for implementing effective cybersecurity defenses and maintaining system integrity.
Table of Comparison
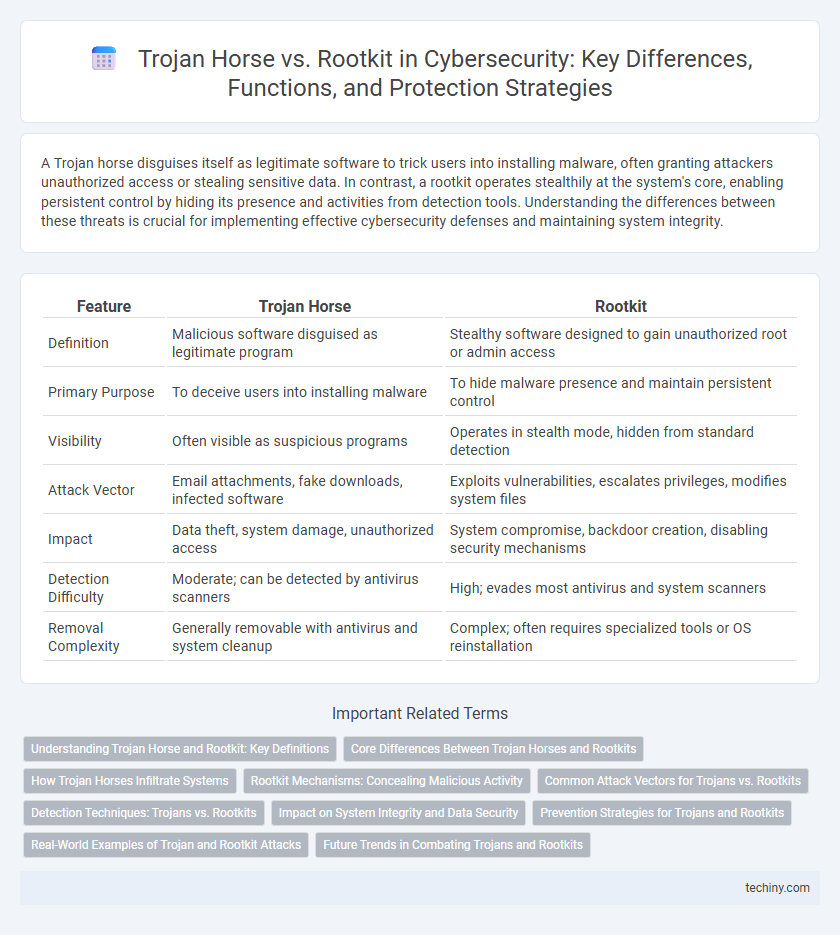
| Feature | Trojan Horse | Rootkit |
|---|---|---|
| Definition | Malicious software disguised as legitimate program | Stealthy software designed to gain unauthorized root or admin access |
| Primary Purpose | To deceive users into installing malware | To hide malware presence and maintain persistent control |
| Visibility | Often visible as suspicious programs | Operates in stealth mode, hidden from standard detection |
| Attack Vector | Email attachments, fake downloads, infected software | Exploits vulnerabilities, escalates privileges, modifies system files |
| Impact | Data theft, system damage, unauthorized access | System compromise, backdoor creation, disabling security mechanisms |
| Detection Difficulty | Moderate; can be detected by antivirus scanners | High; evades most antivirus and system scanners |
| Removal Complexity | Generally removable with antivirus and system cleanup | Complex; often requires specialized tools or OS reinstallation |
Understanding Trojan Horse and Rootkit: Key Definitions
A Trojan horse is a malicious software disguised as legitimate to deceive users into executing it, often leading to unauthorized access or data theft. Rootkits are stealthy programs designed to gain root-level control over a system while hiding their presence from detection tools. Understanding the key differences between Trojan horses and rootkits is crucial for identifying attack vectors and implementing effective cybersecurity defenses.
Core Differences Between Trojan Horses and Rootkits
Trojan horses disguise themselves as legitimate software to deceive users into executing malicious code, often facilitating unauthorized access or data theft. Rootkits operate stealthily at the system or kernel level, maintaining persistent control and hiding their presence from security tools and the operating system. The core difference lies in their operational method: Trojan horses rely on social engineering and user interaction, whereas rootkits focus on deep system-level concealment and persistence.
How Trojan Horses Infiltrate Systems
Trojan horses infiltrate systems by masquerading as legitimate software, tricking users into downloading and executing malicious code. Once activated, they can create backdoors for unauthorized access, steal sensitive data, or deliver additional payloads. Unlike rootkits, which primarily conceal themselves to maintain persistent control, Trojan horses rely on social engineering to initiate infiltration.
Rootkit Mechanisms: Concealing Malicious Activity
Rootkits employ advanced techniques such as kernel-level hooks and direct memory manipulation to conceal their presence and malicious activities from standard detection tools. By embedding themselves deeply within the operating system, rootkits intercept system calls and modify system processes, effectively hiding files, processes, and network connections associated with malware. This stealth mechanism makes rootkits particularly challenging to detect and remove compared to Trojan horses, which rely more on deception and social engineering.
Common Attack Vectors for Trojans vs. Rootkits
Trojan horses commonly infiltrate systems through phishing emails, malicious downloads, and compromised websites, exploiting user interaction to execute payloads. Rootkits often gain access via privilege escalation exploits, software vulnerabilities, or by piggybacking on existing malware to maintain persistent, hidden control over system processes. Both attack vectors target system security but differ in entry points and persistence strategies, with Trojans focusing on initial infection and Rootkits emphasizing stealth and long-term accessibility.
Detection Techniques: Trojans vs. Rootkits
Detection techniques for Trojan horses primarily involve signature-based antivirus scans and behavior analysis to identify unauthorized code execution and unusual system activities. Rootkits require more advanced detection methods such as memory dump analysis, integrity checking of kernel modules, and heuristic tools designed to uncover hidden processes and files. Both demand continuous monitoring and updated threat intelligence to effectively identify and neutralize these stealthy cyber threats.
Impact on System Integrity and Data Security
Trojan horses deceive users by masquerading as legitimate software, enabling unauthorized access and data theft without immediate system damage, while rootkits operate at a deeper level, embedding themselves into the operating system to maintain persistent control and evade detection, severely compromising system integrity. Rootkits can manipulate core system functions and hide malicious activities, making data breaches more difficult to identify and mitigate. Both threats undermine data security, but rootkits pose a more critical risk due to their stealth and direct interference with system processes.
Prevention Strategies for Trojans and Rootkits
Effective prevention strategies for Trojans and rootkits include maintaining updated antivirus and anti-malware software that can detect and isolate suspicious behavior patterns. Implementing strict access controls and regular system audits helps minimize vulnerability exploitation, while user education on avoiding phishing scams and untrusted downloads significantly reduces infection risks. Network segmentation and real-time monitoring further strengthen defenses by limiting unauthorized access and enabling rapid identification of intrusions.
Real-World Examples of Trojan and Rootkit Attacks
The Zeus Trojan, responsible for stealing millions of dollars by targeting banking credentials, exemplifies the devastating financial impact Trojan horses can have. Rootkits like Sony BMG's infamous XCP, which covertly installed software on millions of computers under the guise of DRM protection, highlight the stealth and persistence these threats maintain on infected systems. Both attack types demonstrate sophisticated methods of evading detection, making cybersecurity defenses critical for safeguarding sensitive data in enterprise and personal environments.
Future Trends in Combating Trojans and Rootkits
Advancements in artificial intelligence and machine learning are enhancing the detection and mitigation of Trojans and rootkits by identifying anomalous behavior patterns in real-time. Emerging endpoint detection and response (EDR) solutions utilize behavioral analytics combined with threat intelligence to proactively isolate and remediate these stealthy threats. Collaboration between cybersecurity firms and cloud service providers is accelerating the development of adaptive defense mechanisms designed to combat increasingly sophisticated Trojan and rootkit variants.
Trojan horse vs rootkit Infographic
 techiny.com
techiny.com