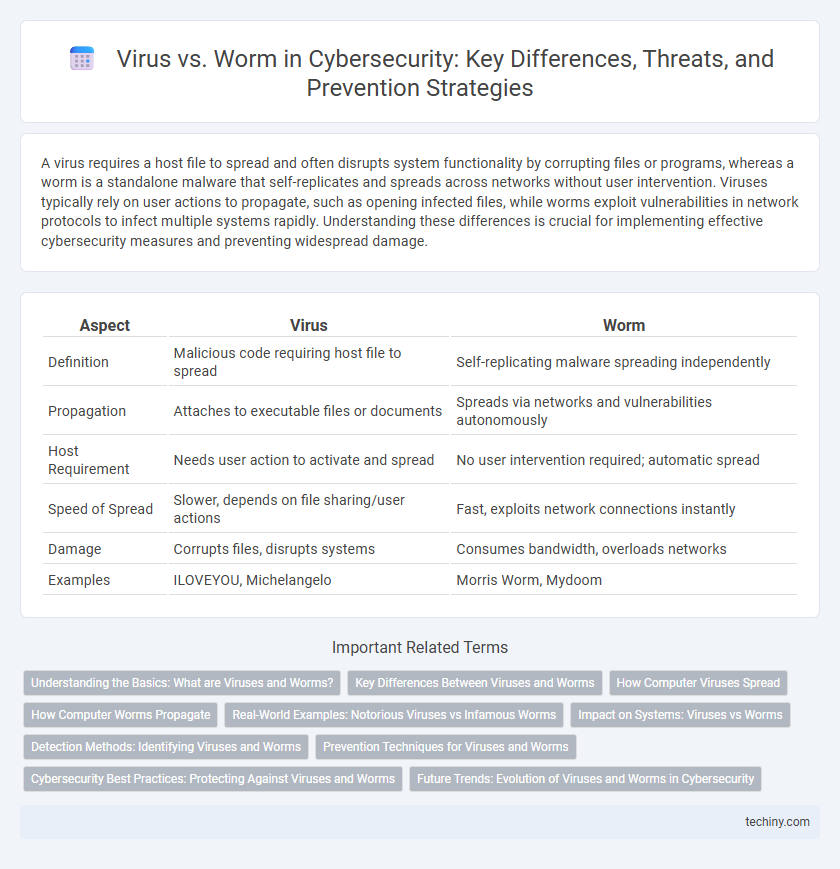
A virus requires a host file to spread and often disrupts system functionality by corrupting files or programs, whereas a worm is a standalone malware that self-replicates and spreads across networks without user intervention. Viruses typically rely on user actions to propagate, such as opening infected files, while worms exploit vulnerabilities in network protocols to infect multiple systems rapidly. Understanding these differences is crucial for implementing effective cybersecurity measures and preventing widespread damage.
Table of Comparison
| Aspect | Virus | Worm |
|---|---|---|
| Definition | Malicious code requiring host file to spread | Self-replicating malware spreading independently |
| Propagation | Attaches to executable files or documents | Spreads via networks and vulnerabilities autonomously |
| Host Requirement | Needs user action to activate and spread | No user intervention required; automatic spread |
| Speed of Spread | Slower, depends on file sharing/user actions | Fast, exploits network connections instantly |
| Damage | Corrupts files, disrupts systems | Consumes bandwidth, overloads networks |
| Examples | ILOVEYOU, Michelangelo | Morris Worm, Mydoom |
Understanding the Basics: What are Viruses and Worms?
Viruses are malicious programs that attach themselves to legitimate files and require human action to spread, often causing damage by corrupting or modifying data. Worms are standalone malware that replicate autonomously across networks, exploiting vulnerabilities to propagate without user intervention. Understanding these fundamental differences is crucial for developing effective cybersecurity defenses and mitigating infection risks.
Key Differences Between Viruses and Worms
Viruses require user action to spread by attaching themselves to executable files, while worms are standalone malware that replicate autonomously across networks. Unlike viruses, worms exploit vulnerabilities to propagate rapidly without host file modification. Understanding these key differences is crucial for effective cybersecurity defense and incident response strategies.
How Computer Viruses Spread
Computer viruses spread primarily through infected files, email attachments, and software downloads, which execute malicious code when opened or installed by the user. Unlike worms, viruses require human action to propagate, often embedding themselves in executable programs or documents to infect other files and systems. This method relies heavily on social engineering tactics to trick users into initiating the infection process.
How Computer Worms Propagate
Computer worms propagate by exploiting vulnerabilities in network protocols and software applications, allowing them to self-replicate and spread autonomously across interconnected systems. Unlike viruses, worms do not require user interaction to activate, enabling rapid dissemination through email attachments, file-sharing networks, or unsecured network ports. This autonomous replication causes widespread network congestion and significant security risks within enterprise infrastructures.
Real-World Examples: Notorious Viruses vs Infamous Worms
The ILOVEYOU virus, which caused over $10 billion in damages worldwide, exemplifies the destructive potential of viruses through email-based propagation and file corruption. In contrast, the Mydoom worm remains one of the fastest-spreading worms, exploiting network vulnerabilities to launch massive Distributed Denial of Service (DDoS) attacks against major websites. Both malware types highlight distinct infection mechanisms, with viruses attaching to files and worms self-replicating across networks, emphasizing the need for diverse cybersecurity defenses.
Impact on Systems: Viruses vs Worms
Viruses typically require user interaction to spread and attach themselves to executable files, causing direct damage by corrupting files or altering system functions. Worms propagate autonomously through networks, rapidly consuming bandwidth and resources, often resulting in widespread system slowdowns or network outages. The autonomous nature of worms generally leads to a more severe impact on network infrastructure compared to viruses, which primarily affect individual systems.
Detection Methods: Identifying Viruses and Worms
Detection methods for viruses and worms primarily rely on signature-based scanning, heuristic analysis, and behavioral monitoring to identify malicious code. Viruses often require file scanning to detect embedded malicious signatures, while worms are detected through network traffic analysis and unusual propagation patterns. Advanced intrusion detection systems (IDS) use anomaly detection and sandboxing to recognize and isolate both viruses and worms before they cause significant damage.
Prevention Techniques for Viruses and Worms
Effective prevention techniques for viruses and worms include regular software updates and patch management to close security vulnerabilities. Employing reputable antivirus and anti-malware solutions with real-time scanning capabilities helps detect and remove threats before they cause harm. Network segmentation and using firewalls limit worm propagation, while strong email filtering and user education reduce the risk of virus infections through phishing and malicious attachments.
Cybersecurity Best Practices: Protecting Against Viruses and Worms
Implementing robust cybersecurity best practices is essential to protect against viruses and worms, which both pose significant threats by disrupting systems and stealing data. Using updated antivirus software, enabling firewalls, and regularly applying security patches limit vulnerabilities exploited by these malicious programs. Employee training on recognizing phishing scams and avoiding suspicious downloads further strengthens defenses against infections and propagation within networks.
Future Trends: Evolution of Viruses and Worms in Cybersecurity
Future trends in cybersecurity indicate viruses and worms will increasingly leverage artificial intelligence and machine learning to improve evasion techniques and adapt to security defenses in real-time. The evolution of these malware types shows a shift towards multi-vector attacks combining viruses, worms, ransomware, and phishing for higher impact and persistence. Enhanced detection technologies based on behavioral analysis and threat intelligence sharing will be critical to counteract these more sophisticated and autonomous cyber threats.
Virus vs Worm Infographic
 techiny.com
techiny.com