Malware encompasses various harmful software types designed to damage or exploit systems, including viruses, worms, spyware, and ransomware. Ransomware specifically encrypts files or locks users out of their systems until a ransom is paid, posing a highly targeted threat to individuals and organizations. Effective cybersecurity strategies require understanding these distinctions to implement appropriate detection and prevention measures.
Table of Comparison
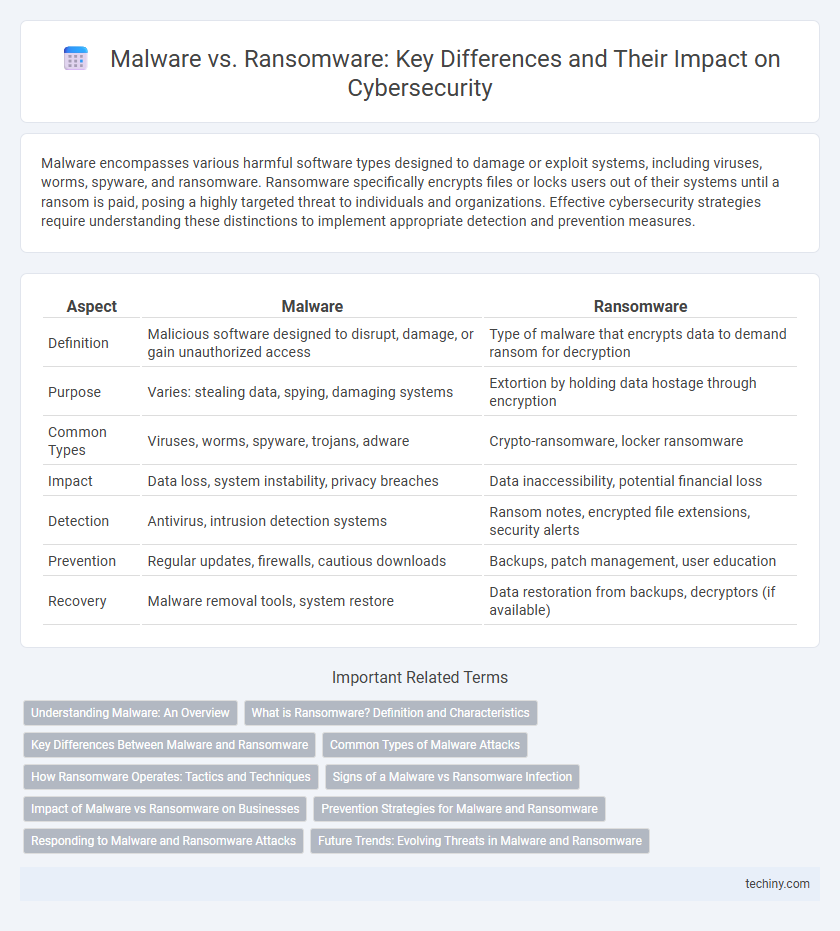
| Aspect | Malware | Ransomware |
|---|---|---|
| Definition | Malicious software designed to disrupt, damage, or gain unauthorized access | Type of malware that encrypts data to demand ransom for decryption |
| Purpose | Varies: stealing data, spying, damaging systems | Extortion by holding data hostage through encryption |
| Common Types | Viruses, worms, spyware, trojans, adware | Crypto-ransomware, locker ransomware |
| Impact | Data loss, system instability, privacy breaches | Data inaccessibility, potential financial loss |
| Detection | Antivirus, intrusion detection systems | Ransom notes, encrypted file extensions, security alerts |
| Prevention | Regular updates, firewalls, cautious downloads | Backups, patch management, user education |
| Recovery | Malware removal tools, system restore | Data restoration from backups, decryptors (if available) |
Understanding Malware: An Overview
Malware encompasses a wide range of malicious software designed to disrupt, damage, or gain unauthorized access to computer systems, including viruses, worms, trojans, spyware, and ransomware. Understanding malware involves recognizing its various forms and attack vectors, such as phishing emails, drive-by downloads, and infected software updates, that compromise system integrity. Effective malware detection relies on antivirus software, behavior analysis, and real-time monitoring to mitigate the risks posed to data security and network operations.
What is Ransomware? Definition and Characteristics
Ransomware is a type of malicious software designed to block access to a computer system or data until a ransom is paid. It encrypts files or locks devices, often targeting businesses and critical infrastructure to maximize impact. Key characteristics include encryption of victim data, ransom demands typically in cryptocurrency, and the use of social engineering or phishing to infiltrate networks.
Key Differences Between Malware and Ransomware
Malware is a broad category of malicious software designed to harm or exploit any programmable device, system, or network, including viruses, worms, trojans, and spyware. Ransomware is a specific type of malware that encrypts victims' files or locks their systems, demanding payment for restoration. The key difference lies in ransomware's direct financial extortion goal, whereas malware can perform various harmful actions without immediate monetary demands.
Common Types of Malware Attacks
Malware encompasses various malicious software types, including viruses, worms, trojans, spyware, and adware, each designed to disrupt systems, steal information, or gain unauthorized access. Ransomware is a specialized malware variant that encrypts victim data, demanding payment for decryption keys to restore access. Common malware attacks exploit email phishing, drive-by downloads, and software vulnerabilities to infiltrate networks and compromise cybersecurity defenses.
How Ransomware Operates: Tactics and Techniques
Ransomware operates by encrypting a victim's files using advanced cryptographic algorithms, rendering data inaccessible until a ransom is paid. Attackers often deploy tactics such as phishing emails, exploit kits, and Remote Desktop Protocol (RDP) brute force to gain initial access to networks. Post-infection, ransomware groups commonly engage in lateral movement, data exfiltration, and use double extortion techniques to pressure victims into compliance.
Signs of a Malware vs Ransomware Infection
Malware infections often cause system slowdowns, frequent crashes, and unauthorized access to files, signaling compromised security. Ransomware specifically encrypts files and displays ransom notes demanding payment for decryption keys, making data inaccessible. Monitoring unusual network activity and abrupt file permission changes helps distinguish ransomware from general malware threats.
Impact of Malware vs Ransomware on Businesses
Malware broadly disrupts business operations by compromising data integrity, causing system downtime, and facilitating unauthorized access to sensitive information. Ransomware specifically impacts businesses by encrypting critical files and demanding payment for their release, often resulting in costly operational halts and potential data loss. Both malicious software types threaten financial stability, reputation, and regulatory compliance within organizations.
Prevention Strategies for Malware and Ransomware
Effective prevention strategies against malware and ransomware include implementing robust endpoint protection software, ensuring regular system and software updates, and utilizing advanced email filtering to block suspicious attachments and links. Employing multi-factor authentication and conducting frequent employee training on recognizing phishing attacks significantly reduce the risk of unauthorized access and infection. Regular data backups, stored offline or in secure cloud environments, enhance recovery capabilities in the event of ransomware attacks.
Responding to Malware and Ransomware Attacks
Effective response to malware attacks involves immediate isolation of affected systems, thorough scanning with updated antivirus tools, and applying security patches to prevent further exploitation. In ransomware incidents, prioritize data backup restoration, avoid paying ransoms, and engage with cybersecurity professionals to decrypt files and identify attack vectors. Implementing robust incident response plans, continuous monitoring, and employee training are critical to mitigating damage from both malware and ransomware threats.
Future Trends: Evolving Threats in Malware and Ransomware
Future trends in cybersecurity reveal an increasing sophistication in malware and ransomware attacks, leveraging artificial intelligence and machine learning to bypass traditional defenses. Cybercriminals are developing polymorphic malware capable of altering code dynamically, making detection more difficult and enabling targeted ransomware campaigns on critical infrastructure. Enhanced threat intelligence platforms and automated response systems are emerging to counter these evolving threats with real-time analysis and adaptive protection mechanisms.
Malware vs Ransomware Infographic
 techiny.com
techiny.com