Application security involves safeguarding software applications from vulnerabilities and threats through practices like code reviews, penetration testing, and secure coding. Network security focuses on protecting the integrity and usability of network infrastructure using firewalls, intrusion detection systems, and encryption protocols. Both are essential components of a comprehensive cybersecurity strategy, addressing threats at different layers to prevent data breaches and unauthorized access.
Table of Comparison
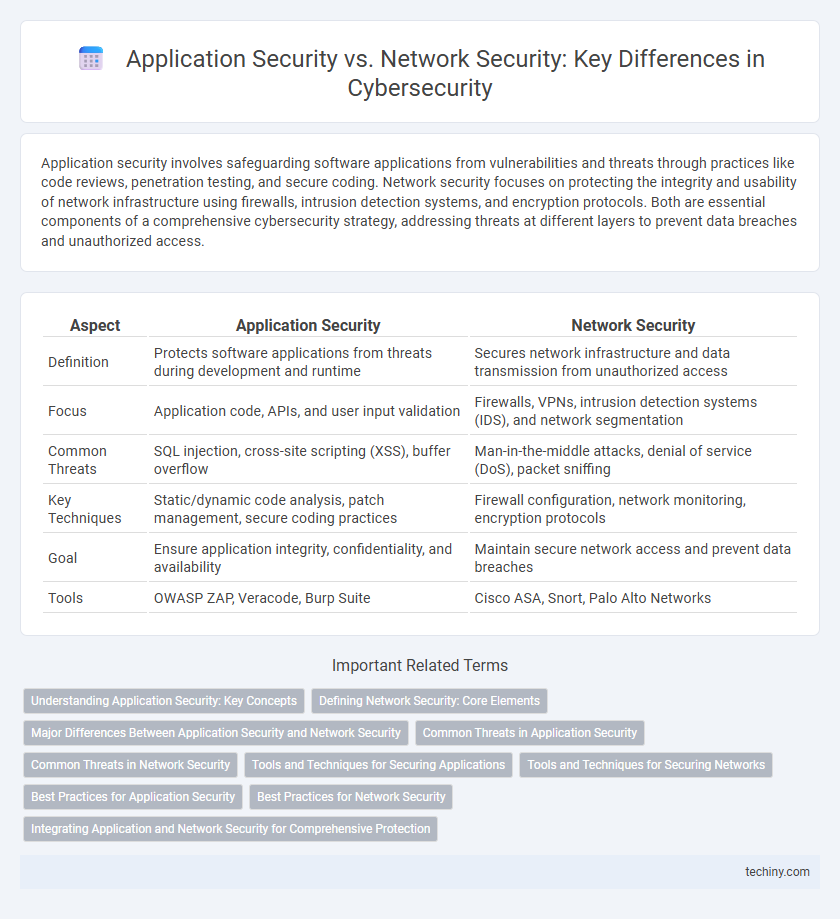
| Aspect | Application Security | Network Security |
|---|---|---|
| Definition | Protects software applications from threats during development and runtime | Secures network infrastructure and data transmission from unauthorized access |
| Focus | Application code, APIs, and user input validation | Firewalls, VPNs, intrusion detection systems (IDS), and network segmentation |
| Common Threats | SQL injection, cross-site scripting (XSS), buffer overflow | Man-in-the-middle attacks, denial of service (DoS), packet sniffing |
| Key Techniques | Static/dynamic code analysis, patch management, secure coding practices | Firewall configuration, network monitoring, encryption protocols |
| Goal | Ensure application integrity, confidentiality, and availability | Maintain secure network access and prevent data breaches |
| Tools | OWASP ZAP, Veracode, Burp Suite | Cisco ASA, Snort, Palo Alto Networks |
Understanding Application Security: Key Concepts
Application security involves protecting software applications from vulnerabilities and threats by implementing measures such as code reviews, encryption, and secure authentication. It focuses on detecting and mitigating risks like injection attacks, cross-site scripting (XSS), and buffer overflows within the application layer. Prioritizing secure software development lifecycle (SDLC) practices and continuous security testing ensures robust defense against exploitation attempts targeting application-specific weaknesses.
Defining Network Security: Core Elements
Network security focuses on protecting the integrity, confidentiality, and availability of data as it is transmitted across or accessed through network infrastructures. Core elements include firewall management, intrusion detection systems (IDS), virtual private networks (VPNs), and secure access controls that prevent unauthorized entry and data breaches. These components work together to safeguard network traffic, monitor suspicious activities, and enforce security policies to maintain a resilient digital environment.
Major Differences Between Application Security and Network Security
Application Security protects software applications from vulnerabilities and attacks by implementing measures such as code reviews, input validation, and encryption. Network Security safeguards the infrastructure by monitoring and controlling incoming and outgoing network traffic through firewalls, intrusion detection systems, and virtual private networks (VPNs). The major differences lie in their focus areas: Application Security targets flaws within software applications, while Network Security emphasizes protecting data as it travels across networks.
Common Threats in Application Security
Application security faces common threats such as SQL injection, cross-site scripting (XSS), and insecure deserialization that compromise data integrity and user privacy. Attackers exploit vulnerabilities in code and software logic to gain unauthorized access or disrupt application functionality. Robust input validation, regular security testing, and patch management are essential to mitigate these risks effectively.
Common Threats in Network Security
Common threats in network security include Distributed Denial of Service (DDoS) attacks, which overwhelm network resources to disrupt services, and Man-in-the-Middle (MitM) attacks that intercept and manipulate data transmissions. Network vulnerabilities such as unsecured Wi-Fi access points, outdated firmware, and weak firewall configurations expose systems to unauthorized access and data breaches. Effective defense strategies incorporate intrusion detection systems (IDS), robust encryption protocols, and continuous network monitoring to mitigate these prevalent cyber threats.
Tools and Techniques for Securing Applications
Application security leverages tools such as Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Software Composition Analysis (SCA) to identify and mitigate vulnerabilities within code before deployment. Techniques including secure coding practices, penetration testing, and runtime application self-protection (RASP) enhance defenses against threats like injection attacks and code tampering. These methods differ from network security tools that primarily focus on firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs) to protect data in transit and network infrastructure.
Tools and Techniques for Securing Networks
Network security relies on tools such as firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs) to monitor and control incoming and outgoing traffic, preventing unauthorized access and cyber threats. Techniques like network segmentation, encryption protocols (e.g., SSL/TLS), and regular vulnerability assessments enhance protection by isolating sensitive data and safeguarding communication channels. Unlike application security, which focuses on code-level defenses, network security emphasizes perimeter defense, traffic analysis, and real-time threat mitigation to maintain overall system integrity.
Best Practices for Application Security
Implementing robust input validation, encryption, and regular code audits are essential best practices for application security, preventing vulnerabilities such as SQL injection and cross-site scripting attacks. Secure coding standards and frequent penetration testing help identify and remediate weaknesses early in the development lifecycle. Integrating multi-factor authentication and comprehensive access controls further safeguard sensitive data within applications from unauthorized access and potential breaches.
Best Practices for Network Security
Implementing strong firewall configurations and regular network segmentation significantly reduces the attack surface and limits lateral movement within systems. Continuous monitoring with intrusion detection and prevention systems (IDPS) enables swift identification and mitigation of threats before they escalate. Enforcing strict access controls, multi-factor authentication, and secure VPN usage ensures that only authorized users can access sensitive network resources, enhancing overall network security posture.
Integrating Application and Network Security for Comprehensive Protection
Integrating application security and network security creates a robust defense strategy by addressing vulnerabilities at both the software and infrastructure levels, mitigating risks such as SQL injection, cross-site scripting, and distributed denial-of-service (DDoS) attacks. Employing tools like web application firewalls (WAFs), intrusion detection systems (IDS), and secure coding practices ensures continuous monitoring and rapid response across all threat vectors. This comprehensive protection reduces the attack surface and enhances the organization's ability to detect and prevent sophisticated cyber threats.
Application Security vs Network Security Infographic
 techiny.com
techiny.com