Malware refers to malicious software designed to damage, disrupt, or gain unauthorized access to computer systems, including viruses, worms, and ransomware. Exploits are specific techniques or code that take advantage of vulnerabilities within software to execute malicious actions or gain control over a system. Understanding the difference between malware and exploits is crucial for implementing effective cybersecurity defenses and mitigating potential threats.
Table of Comparison
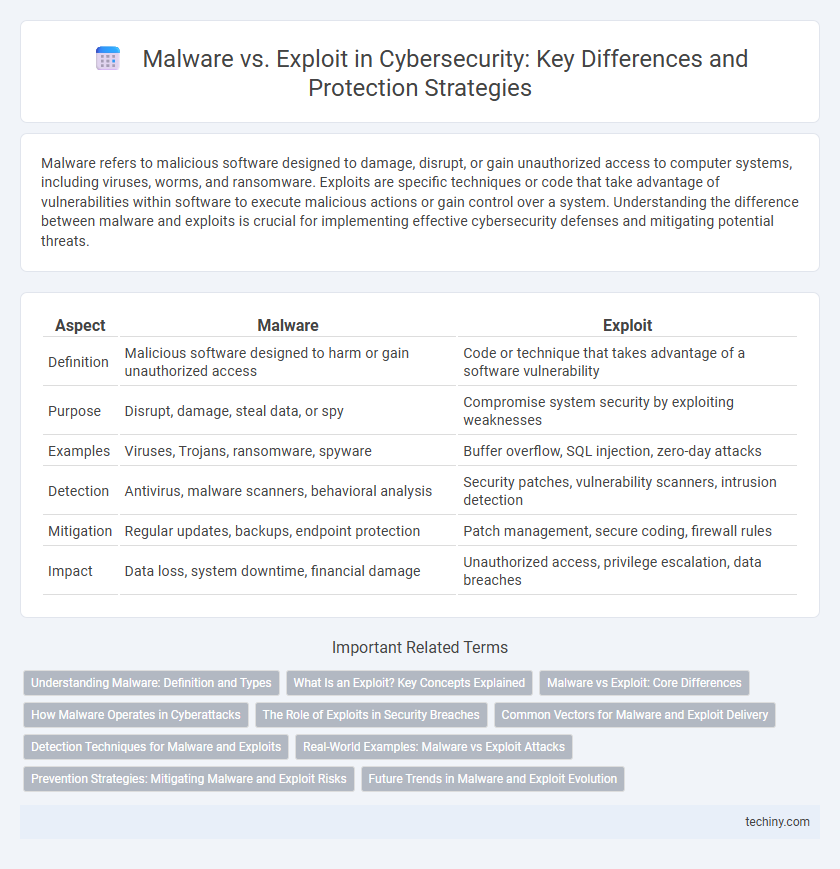
| Aspect | Malware | Exploit |
|---|---|---|
| Definition | Malicious software designed to harm or gain unauthorized access | Code or technique that takes advantage of a software vulnerability |
| Purpose | Disrupt, damage, steal data, or spy | Compromise system security by exploiting weaknesses |
| Examples | Viruses, Trojans, ransomware, spyware | Buffer overflow, SQL injection, zero-day attacks |
| Detection | Antivirus, malware scanners, behavioral analysis | Security patches, vulnerability scanners, intrusion detection |
| Mitigation | Regular updates, backups, endpoint protection | Patch management, secure coding, firewall rules |
| Impact | Data loss, system downtime, financial damage | Unauthorized access, privilege escalation, data breaches |
Understanding Malware: Definition and Types
Malware is malicious software designed to damage, disrupt, or gain unauthorized access to computer systems, encompassing various types such as viruses, worms, trojans, ransomware, spyware, and adware. Each type of malware operates differently, with viruses attaching to files and spreading through systems, ransomware encrypting data to demand payment, and spyware secretly collecting user information. Understanding these distinct varieties helps in identifying threats and implementing effective cybersecurity defenses against malware attacks.
What Is an Exploit? Key Concepts Explained
An exploit is a piece of software, code, or sequence of commands that takes advantage of a vulnerability in a computer system or application to cause unintended behavior or unauthorized access. Unlike malware, which is malicious software designed to harm or infiltrate systems, an exploit specifically targets security flaws to breach defenses. Understanding exploits is crucial for identifying potential threats and implementing effective cybersecurity measures to protect networks and data.
Malware vs Exploit: Core Differences
Malware refers to malicious software designed to damage, disrupt, or gain unauthorized access to computer systems, including viruses, worms, ransomware, and trojans. Exploits are techniques or code that take advantage of specific vulnerabilities in software or hardware to execute unauthorized actions, often serving as the delivery mechanism for malware. Understanding the core difference highlights that malware is the harmful payload, while exploits are the method used to breach defenses and deploy that payload.
How Malware Operates in Cyberattacks
Malware operates in cyberattacks by infiltrating systems through various vectors such as email attachments, malicious downloads, or compromised websites, executing hidden payloads that disrupt, steal, or damage data. It often employs techniques like code obfuscation, rootkits, and polymorphism to evade detection by antivirus software and maintain persistence within the target environment. By leveraging vulnerabilities in software or user behavior, malware establishes control over infected devices to facilitate data exfiltration, ransomware deployment, or botnet creation.
The Role of Exploits in Security Breaches
Exploits serve as critical tools for attackers by taking advantage of vulnerabilities in software or hardware systems to gain unauthorized access, often acting as the initial vector for severe security breaches. These attacks leverage specific weaknesses that bypass security measures, enabling the deployment of malware payloads that compromise data integrity and availability. Understanding the role of exploits in the attack chain is essential for developing advanced threat detection and vulnerability management strategies to mitigate potential breaches effectively.
Common Vectors for Malware and Exploit Delivery
Malware commonly spreads through phishing emails, malicious attachments, and infected software downloads, exploiting human error and weak security controls. Exploits typically leverage software vulnerabilities, delivered via compromised websites, drive-by downloads, or network-based attacks like man-in-the-middle and zero-day exploits. Both rely heavily on social engineering, outdated systems, and unpatched software to infiltrate targeted environments.
Detection Techniques for Malware and Exploits
Malware detection techniques rely heavily on signature-based scanning, heuristic analysis, and behavior monitoring to identify known and unknown threats by examining file patterns, code anomalies, and suspicious activities. Exploit detection primarily involves intrusion detection systems (IDS) and exploit mitigation tools that monitor unusual network traffic, application behavior, and memory corruption attempts targeting software vulnerabilities. Both approaches leverage machine learning algorithms and sandbox environments to enhance the accuracy and speed of threat identification, minimizing false positives while improving response times.
Real-World Examples: Malware vs Exploit Attacks
Malware attacks like the 2017 WannaCry ransomware infected over 230,000 computers worldwide, encrypting data and demanding ransom payments, while the 2017 Equifax data breach exploited a vulnerability in Apache Struts to expose sensitive information of 147 million people. Malware typically involves malicious software such as viruses, worms, or ransomware directly installed on systems, whereas exploits leverage software vulnerabilities to execute unauthorized code or escalate privileges. Understanding these real-world attacks highlights the importance of patch management, endpoint protection, and robust intrusion detection systems in cybersecurity defense strategies.
Prevention Strategies: Mitigating Malware and Exploit Risks
Effective prevention strategies against malware and exploit risks include deploying advanced endpoint protection with real-time threat detection to identify and neutralize malicious software before execution. Regular software patching and vulnerability management reduce exploit opportunities by addressing security flaws in operating systems and applications. Implementing network segmentation, strict access controls, and user education on phishing awareness further minimizes attack surfaces and potential breach vectors.
Future Trends in Malware and Exploit Evolution
Future trends in malware and exploit evolution indicate increased sophistication with the integration of artificial intelligence and machine learning techniques, enabling adaptive evasion and targeted attacks. The rise of polymorphic malware and zero-day exploits will challenge traditional detection methods, driving advancements in behavior-based and heuristic security solutions. Quantum computing poses a potential threat to cryptographic defenses, accelerating the development of quantum-resistant algorithms to safeguard against emerging cyber threats.
Malware vs exploit Infographic
 techiny.com
techiny.com