Security by design prioritizes robust architecture and proactive threat mitigation to ensure system resilience against attacks, while security by obscurity relies on secrecy of system details to deter attackers, often resulting in weak protection. Effective cybersecurity strategies emphasize security by design, integrating encryption, authentication, and access controls from the outset to create inherently secure environments. Relying solely on obscurity can lead to vulnerabilities once system details are exposed, making it a less reliable approach compared to transparent, well-engineered security frameworks.
Table of Comparison
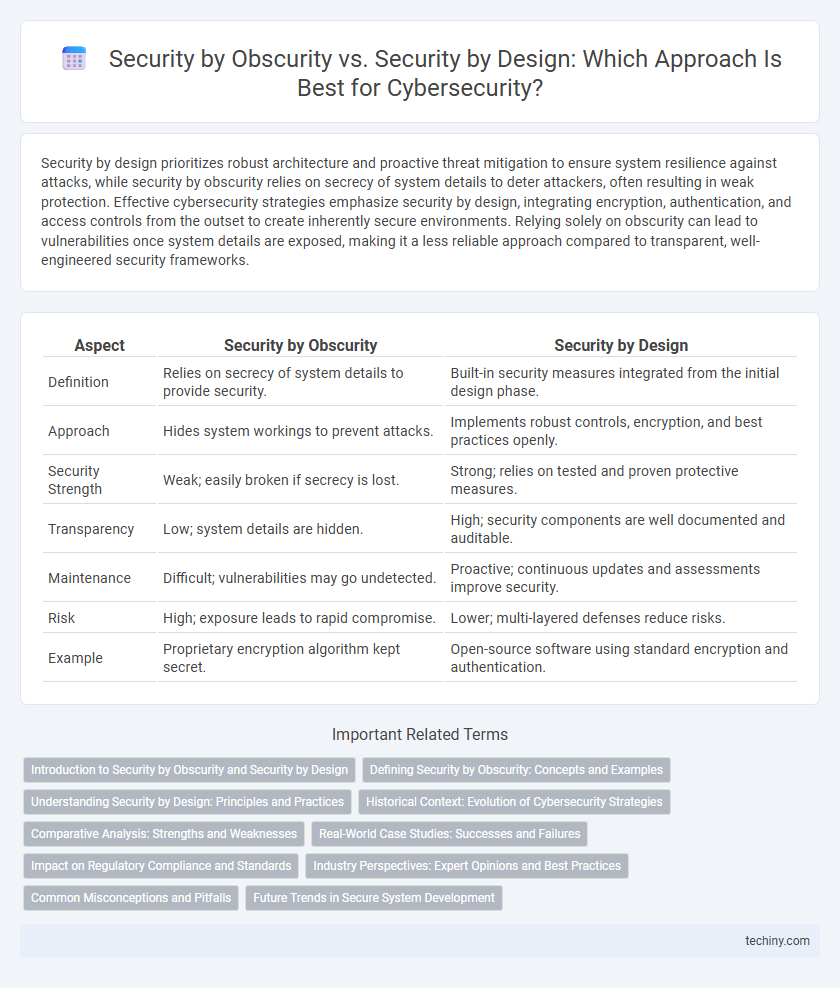
| Aspect | Security by Obscurity | Security by Design |
|---|---|---|
| Definition | Relies on secrecy of system details to provide security. | Built-in security measures integrated from the initial design phase. |
| Approach | Hides system workings to prevent attacks. | Implements robust controls, encryption, and best practices openly. |
| Security Strength | Weak; easily broken if secrecy is lost. | Strong; relies on tested and proven protective measures. |
| Transparency | Low; system details are hidden. | High; security components are well documented and auditable. |
| Maintenance | Difficult; vulnerabilities may go undetected. | Proactive; continuous updates and assessments improve security. |
| Risk | High; exposure leads to rapid compromise. | Lower; multi-layered defenses reduce risks. |
| Example | Proprietary encryption algorithm kept secret. | Open-source software using standard encryption and authentication. |
Introduction to Security by Obscurity and Security by Design
Security by Obscurity relies on hiding system details and mechanisms to prevent attacks, assuming that secrecy alone can deter threats. In contrast, Security by Design emphasizes building systems from the ground up with robust security principles, ensuring protection even if internal workings are known. Implementing Security by Design involves rigorous threat modeling, secure coding practices, and continuous vulnerability assessment to create resilient cybersecurity architectures.
Defining Security by Obscurity: Concepts and Examples
Security by obscurity relies on hiding system details to protect against attacks, such as concealing source code or using non-standard ports. This approach assumes attackers cannot exploit what they cannot see, but it is vulnerable if obscured information is discovered. Examples include proprietary encryption algorithms and hidden network addresses, which lack robustness compared to comprehensive security measures.
Understanding Security by Design: Principles and Practices
Security by Design emphasizes embedding robust security measures into the architecture and development process, ensuring systems are resilient against potential threats from the start. Key principles include minimizing attack surfaces, applying least privilege access, and conducting regular threat modeling and testing. This proactive approach contrasts with Security by Obscurity, which relies on hiding vulnerabilities rather than eliminating them through fundamental design integrity.
Historical Context: Evolution of Cybersecurity Strategies
Early cybersecurity relied heavily on security by obscurity, where system vulnerabilities were hidden to deter attackers, but this approach often failed as adversaries uncovered hidden flaws. The evolution toward security by design emphasized building robust systems with inherent protections, integrating principles like least privilege and defense in depth from inception. This shift reflects a maturation in cybersecurity strategies, prioritizing transparency and proactive risk management over secrecy.
Comparative Analysis: Strengths and Weaknesses
Security by Design embeds robust security principles into system architecture, ensuring resilience against known vulnerabilities and facilitating proactive threat mitigation. Security by Obscurity relies on concealing system details to deter attackers, but it often fails when hidden mechanisms are discovered, leading to significant security breaches. While Security by Design emphasizes transparency and continuous improvement, Security by Obscurity provides limited protection and can create a false sense of security.
Real-World Case Studies: Successes and Failures
Security by design, exemplified by companies like Microsoft with its Secure Development Lifecycle, demonstrates consistent success in mitigating vulnerabilities through proactive threat modeling and rigorous testing. In contrast, security by obscurity, often seen in early IoT devices, has repeatedly failed as hidden mechanisms were eventually exposed, leading to massive breaches such as the Mirai botnet attack. Real-world case studies underscore that robust, transparent design frameworks outperform reliance on secrecy, minimizing risks and enhancing long-term resilience.
Impact on Regulatory Compliance and Standards
Security by design aligns with regulatory compliance frameworks such as GDPR, HIPAA, and NIST by embedding robust security controls from the outset, ensuring systematic risk management and data protection. Security by obscurity often fails regulatory standards due to its reliance on secrecy rather than verifiable safeguards, increasing vulnerability to audits and penalties. Organizations adopting security by design demonstrate proactive adherence to compliance mandates, reducing legal risks and enhancing trust with stakeholders.
Industry Perspectives: Expert Opinions and Best Practices
Industry experts emphasize that Security by Design, which integrates robust security measures from the initial stages of development, outperforms Security by Obscurity, where protection relies on secrecy of system details. Best practices in cybersecurity highlight comprehensive risk assessment, encryption, and continuous monitoring as foundational elements of Security by Design, fostering resilience against evolving threats. Leading organizations advocate for transparency, rigorous testing, and adherence to security frameworks like NIST and ISO/IEC 27001 to ensure sustainable protection beyond mere concealment tactics.
Common Misconceptions and Pitfalls
Security by Obscurity relies on hiding system details to protect assets but is often criticized for providing a false sense of security, leading to overlooked vulnerabilities once obscurity is breached. Security by Design emphasizes building robust systems with layered protections and thorough testing, yet misconceptions persist that it is excessively costly or complex, causing some organizations to underinvest in essential security measures. Common pitfalls include neglecting regular updates and penetration testing, which can render both approaches ineffective if not combined with comprehensive risk management strategies.
Future Trends in Secure System Development
Future trends in secure system development emphasize Security by Design, integrating proactive measures such as zero-trust architecture, continuous threat modeling, and automated vulnerability assessments. Security by Obscurity, relying on hidden system details to prevent attacks, suffers from inherent fragility and is increasingly replaced by transparent, robust protocols that prioritize resilience and scalability. Emerging technologies like AI-driven security analytics and blockchain-based identity management further reinforce the shift toward foundational security principles embedded throughout the development lifecycle.
Security by Obscurity vs Security by Design Infographic
 techiny.com
techiny.com