Passive attacks in cybersecurity involve unauthorized monitoring or eavesdropping on data without altering the information, making them difficult to detect. Active attacks, by contrast, entail intentional modification, disruption, or destruction of data to compromise system integrity and availability. Understanding the distinction between these attacks is essential for implementing effective security measures and protecting sensitive information.
Table of Comparison
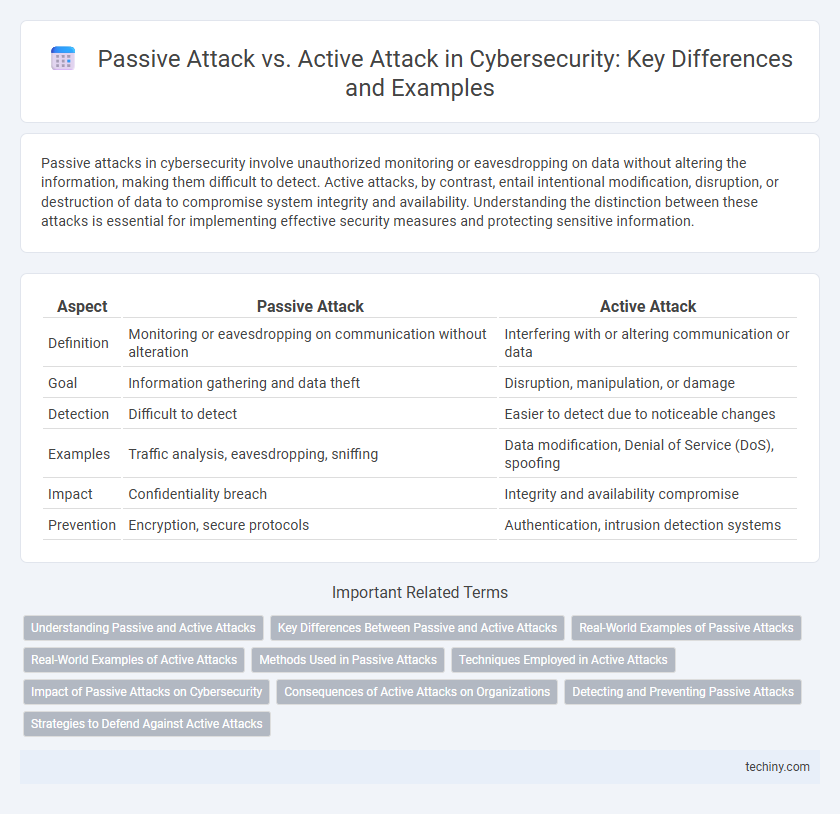
| Aspect | Passive Attack | Active Attack |
|---|---|---|
| Definition | Monitoring or eavesdropping on communication without alteration | Interfering with or altering communication or data |
| Goal | Information gathering and data theft | Disruption, manipulation, or damage |
| Detection | Difficult to detect | Easier to detect due to noticeable changes |
| Examples | Traffic analysis, eavesdropping, sniffing | Data modification, Denial of Service (DoS), spoofing |
| Impact | Confidentiality breach | Integrity and availability compromise |
| Prevention | Encryption, secure protocols | Authentication, intrusion detection systems |
Understanding Passive and Active Attacks
Passive attacks in cybersecurity involve unauthorized interception or monitoring of data without altering the system or communication flow, aiming to gather sensitive information covertly. Active attacks, by contrast, involve tampering with or disrupting data transmission, such as data modification, impersonation, or Denial of Service (DoS), to compromise system integrity and availability. Recognizing the distinct objectives and methods of passive versus active attacks is essential for developing effective security measures like encryption for confidentiality and intrusion detection systems for real-time threat response.
Key Differences Between Passive and Active Attacks
Passive attacks in cybersecurity involve unauthorized monitoring or eavesdropping on data transmissions without altering the communication, primarily aiming to gather information discreetly. Active attacks, by contrast, entail deliberate interference such as data modification, disruption, or injection of malicious content to compromise system integrity and availability. Key differences include the detectability of active attacks due to their disruptive nature, whereas passive attacks remain stealthy, making detection more challenging and necessitating distinct security measures like encryption versus intrusion detection systems.
Real-World Examples of Passive Attacks
Passive attacks in cybersecurity involve unauthorized monitoring or eavesdropping without altering the data, exemplified by network sniffing tools used to capture sensitive information like login credentials in public Wi-Fi networks. Real-world incidents include the NSA's PRISM program, which intercepted internet communications, and cybercriminals harvesting email content and metadata through packet sniffing. These attacks emphasize the importance of encryption protocols such as TLS and VPNs to protect data confidentiality against passive threats.
Real-World Examples of Active Attacks
Active attacks in cybersecurity involve direct interference with data or systems, exemplified by ransomware incidents such as the 2021 Colonial Pipeline attack that caused fuel supply disruptions across the U.S. Another notable example is the 2017 Equifax breach, where attackers exploited system vulnerabilities to steal sensitive personal information of over 147 million individuals. Advanced Persistent Threats (APTs) also represent active attacks, with groups like APT28 conducting prolonged espionage campaigns targeting governmental and corporate networks worldwide.
Methods Used in Passive Attacks
Passive attacks in cybersecurity involve methods such as eavesdropping, traffic analysis, and wiretapping to intercept and monitor data without altering it, aiming to gather sensitive information secretly. Techniques like packet sniffing and network reconnaissance facilitate unauthorized access to communication between systems, enabling attackers to capture passwords, encryption keys, and other confidential data. Since passive attacks do not modify or disrupt system resources, they are difficult to detect and often serve as precursors to more invasive active attacks.
Techniques Employed in Active Attacks
Active attacks employ techniques such as man-in-the-middle (MITM) interception, where attackers alter communication between parties to steal or manipulate data. Other methods include replay attacks that resend captured data to gain unauthorized access and denial-of-service (DoS) attacks aimed at overwhelming systems to disrupt normal service. Exploiting vulnerabilities with malware implants and session hijacking also represent common strategies for compromising system integrity in active cybersecurity threats.
Impact of Passive Attacks on Cybersecurity
Passive attacks in cybersecurity primarily involve unauthorized interception and monitoring of data without altering the original information, leading to significant privacy breaches and intellectual property theft. These attacks compromise confidentiality by allowing attackers to gather sensitive information such as login credentials, financial data, and proprietary business information, often resulting in long-term reputational damage and regulatory penalties. Unlike active attacks, passive attacks are more challenging to detect because they do not produce immediate system disruptions, making them a stealthy and persistent threat to organizational security.
Consequences of Active Attacks on Organizations
Active attacks in cybersecurity result in significant consequences for organizations, including data breaches, financial losses, and reputational damage. Unlike passive attacks, which only intercept or monitor information, active attacks involve unauthorized modifications, deletion, or injection of data, leading to operational disruptions and compromised system integrity. The impact of active attacks often necessitates extensive incident response, legal liabilities, and increased cybersecurity expenditures.
Detecting and Preventing Passive Attacks
Detecting passive attacks involves monitoring network traffic for unusual data access patterns without alerting attackers, utilizing intrusion detection systems (IDS) and network analyzers to identify eavesdropping or data interception attempts. Implementing strong encryption protocols like TLS and VPNs ensures data confidentiality, preventing attackers from extracting useful information even if communication is intercepted. Regular security audits and strict access controls limit unauthorized data exposure, enhancing prevention of passive reconnaissance activities in cybersecurity environments.
Strategies to Defend Against Active Attacks
Active attack defense strategies in cybersecurity emphasize real-time monitoring, intrusion detection systems (IDS), and prompt incident response to identify and mitigate threats quickly. Implementing multi-factor authentication (MFA) and comprehensive encryption protocols enhances system resilience against unauthorized access and data manipulation. Continuous vulnerability assessments and patch management ensure that exploited weaknesses are minimized, significantly reducing the risk of successful active attacks.
Passive Attack vs Active Attack Infographic
 techiny.com
techiny.com