OAuth enables secure authorization by allowing users to grant third-party applications limited access to their resources without sharing credentials, commonly used for API access. SAML provides an XML-based framework for exchanging authentication and authorization data between identity providers and service providers, primarily for single sign-on in enterprise environments. Choosing between OAuth and SAML depends on the use case: OAuth excels in delegated access scenarios, while SAML is suited for federated identity and enterprise SSO solutions.
Table of Comparison
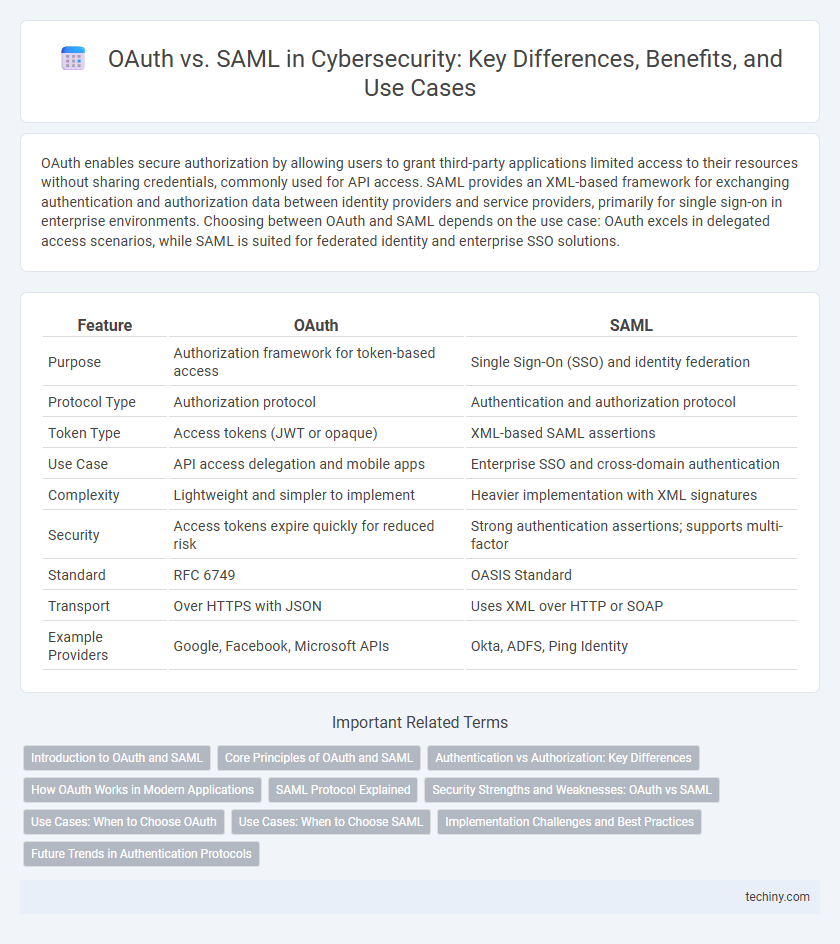
| Feature | OAuth | SAML |
|---|---|---|
| Purpose | Authorization framework for token-based access | Single Sign-On (SSO) and identity federation |
| Protocol Type | Authorization protocol | Authentication and authorization protocol |
| Token Type | Access tokens (JWT or opaque) | XML-based SAML assertions |
| Use Case | API access delegation and mobile apps | Enterprise SSO and cross-domain authentication |
| Complexity | Lightweight and simpler to implement | Heavier implementation with XML signatures |
| Security | Access tokens expire quickly for reduced risk | Strong authentication assertions; supports multi-factor |
| Standard | RFC 6749 | OASIS Standard |
| Transport | Over HTTPS with JSON | Uses XML over HTTP or SOAP |
| Example Providers | Google, Facebook, Microsoft APIs | Okta, ADFS, Ping Identity |
Introduction to OAuth and SAML
OAuth is an open-standard authorization protocol enabling secure API access by allowing users to grant third-party applications limited access without sharing credentials. SAML, or Security Assertion Markup Language, is an XML-based framework for exchanging authentication and authorization data between identity providers and service providers, primarily used in single sign-on (SSO) scenarios. Both OAuth and SAML facilitate secure identity management, but OAuth is optimized for delegated access to resources, while SAML focuses on federated authentication across enterprises.
Core Principles of OAuth and SAML
OAuth is a token-based authorization framework that enables third-party applications to access user resources without sharing credentials, relying on access tokens and scopes for controlled permissions. SAML (Security Assertion Markup Language) is an XML-based authentication protocol that facilitates secure single sign-on (SSO) by exchanging digitally signed authentication assertions between identity providers and service providers. Both OAuth and SAML emphasize secure identity delegation and authentication but differ in their core mechanisms, with OAuth focusing on delegated authorization and SAML prioritizing identity verification and federation.
Authentication vs Authorization: Key Differences
OAuth primarily handles authorization by granting third-party applications limited access to user resources without exposing credentials, while SAML focuses on authentication by enabling single sign-on (SSO) through secure exchange of identity assertions between identity providers and service providers. OAuth uses token-based access delegation suited for API interactions, whereas SAML utilizes XML-based assertions ideal for enterprise-level authentication across multiple domains. Understanding their distinct roles helps organizations implement robust security strategies aligned with either identity verification or controlled resource access.
How OAuth Works in Modern Applications
OAuth operates as an authorization framework enabling third-party applications to access user resources without exposing credentials, utilizing access tokens granted by an authorization server. Modern applications implement OAuth flows such as Authorization Code or Implicit Grant to securely delegate permissions across web, mobile, and API environments. This token-based mechanism enhances security by limiting scope and duration of access, preventing credential misuse in distributed systems.
SAML Protocol Explained
SAML (Security Assertion Markup Language) is an open standard protocol used for single sign-on (SSO) that facilitates secure exchange of authentication and authorization data between an identity provider (IdP) and a service provider (SP). It leverages XML-based assertions to transmit user credentials securely, enabling seamless access to multiple applications without repeated logins. SAML is widely adopted in enterprise environments for federated identity management, offering robust security features such as digital signatures and encryption.
Security Strengths and Weaknesses: OAuth vs SAML
OAuth excels in delegated access, enabling secure token-based authorization for third-party applications without exposing user credentials, but it can be vulnerable to token interception and misuse if not properly implemented. SAML offers robust security for single sign-on (SSO) by using digitally signed XML assertions, ensuring identity verification and message integrity across enterprises, but its complexity and XML-based nature may introduce processing overhead and implementation challenges. Both protocols require careful configuration to mitigate risks such as token replay attacks in OAuth and assertion spoofing in SAML.
Use Cases: When to Choose OAuth
OAuth is ideal for modern web and mobile applications requiring delegated access, such as allowing users to log in via third-party services like Google or Facebook. It excels in scenarios where users need to grant limited access to their resources without sharing credentials, particularly in API authorization for cloud-based applications and microservices. OAuth's token-based approach supports scalable, user-centric authentication flows suited for single-page applications and mobile device environments.
Use Cases: When to Choose SAML
SAML is ideal for enterprise environments requiring robust, secure single sign-on (SSO) across multiple internal applications and legacy systems, especially within federated identity management frameworks. It excels in scenarios where organizations need to enforce strict compliance standards like HIPAA, GDPR, or FedRAMP due to its detailed security assertions and support for XML-based protocols. Choose SAML when integrating with traditional on-premises directories such as Active Directory or LDAP, ensuring seamless authentication for employees accessing internal resources.
Implementation Challenges and Best Practices
Implementing OAuth often requires careful management of access tokens and scopes to prevent unauthorized access, while SAML implementation can be complicated by XML signature handling and assertion validation. Ensuring secure token exchange and mitigating replay attacks are critical best practices for OAuth, whereas validating SAML assertions and maintaining compatibility across identity providers are essential for SAML deployments. Both protocols demand rigorous security testing and adherence to standards like RFC 6749 for OAuth and OASIS standards for SAML to optimize authentication workflows and protect sensitive data.
Future Trends in Authentication Protocols
Future trends in authentication protocols highlight the shift toward decentralized identity frameworks and increased adoption of OAuth 2.1 with enhanced security features such as Mutual TLS and Proof Key for Code Exchange (PKCE). SAML remains prevalent in enterprise settings but faces challenges integrating with modern cloud-native applications, driving a migration toward OAuth and OpenID Connect for seamless, scalable single sign-on experiences. Emerging protocols emphasize adaptive authentication and continuous risk assessment to balance security with user convenience in evolving threat landscapes.
OAuth vs SAML Infographic
 techiny.com
techiny.com