Credential stuffing exploits stolen username and password combinations from data breaches to gain unauthorized access, relying on the reuse of credentials across multiple sites. Brute forcing involves systematically guessing passwords through automated software until the correct one is found, targeting individual accounts without prior knowledge. Both attacks threaten security but differ in approach, with credential stuffing leveraging existing data and brute forcing depending on computational power to crack passwords.
Table of Comparison
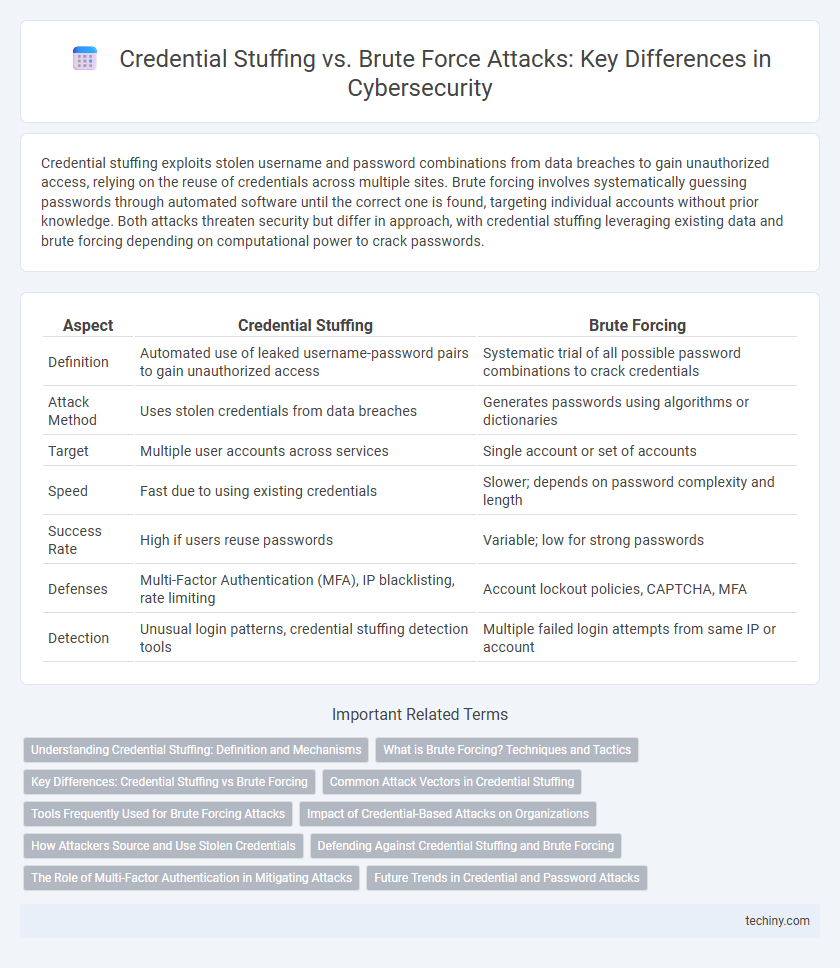
| Aspect | Credential Stuffing | Brute Forcing |
|---|---|---|
| Definition | Automated use of leaked username-password pairs to gain unauthorized access | Systematic trial of all possible password combinations to crack credentials |
| Attack Method | Uses stolen credentials from data breaches | Generates passwords using algorithms or dictionaries |
| Target | Multiple user accounts across services | Single account or set of accounts |
| Speed | Fast due to using existing credentials | Slower; depends on password complexity and length |
| Success Rate | High if users reuse passwords | Variable; low for strong passwords |
| Defenses | Multi-Factor Authentication (MFA), IP blacklisting, rate limiting | Account lockout policies, CAPTCHA, MFA |
| Detection | Unusual login patterns, credential stuffing detection tools | Multiple failed login attempts from same IP or account |
Understanding Credential Stuffing: Definition and Mechanisms
Credential stuffing is a cyberattack method where attackers use automated tools to try large volumes of stolen username and password pairs across multiple websites, exploiting reused credentials to gain unauthorized access. Unlike brute forcing, which attempts every possible password combination, credential stuffing relies on data leaked from previous breaches to optimize attacks quickly and efficiently. This technique leverages botnets and sophisticated scripts to bypass security measures like CAPTCHA and rate limiting, posing significant risks to users and organizations.
What is Brute Forcing? Techniques and Tactics
Brute forcing is a cybersecurity attack method where attackers systematically attempt every possible password combination to gain unauthorized access to accounts or systems. Common techniques include dictionary attacks, where attackers use lists of commonly used passwords, and credential cycling, which leverages reused passwords across multiple services. Advanced tactics involve leveraging high-performance computing and distributed botnets to accelerate password guessing and bypass rate-limiting defenses.
Key Differences: Credential Stuffing vs Brute Forcing
Credential stuffing exploits leaked username-password pairs from data breaches by automating login attempts on multiple websites, relying on the reuse of credentials across platforms. Brute forcing involves systematically trying all possible password combinations on a single account to gain unauthorized access, typically requiring more time and computing power. Credential stuffing attacks are more efficient and scalable due to the use of known credentials, while brute forcing targets individual accounts with exhaustive guessing methods.
Common Attack Vectors in Credential Stuffing
Credential stuffing exploits leaked username and password combinations from previous data breaches to gain unauthorized access, often targeting popular websites with high traffic. Attackers employ automated tools to test vast credential lists against multiple services, leveraging reused passwords and common user habits. This contrasts with brute forcing, which systematically attempts every possible password combination rather than relying on pre-obtained credentials.
Tools Frequently Used for Brute Forcing Attacks
Hydra, Medusa, and Ncrack are among the most frequently used tools for brute forcing attacks, leveraging automated trial-and-error methods to crack passwords. These tools support multiple protocols such as SSH, FTP, and HTTP, facilitating rapid and extensive credential guessing. Utilizing dictionaries and customizable attack configurations, they enable cybercriminals to bypass conventional security defenses by exploiting weak or reused passwords.
Impact of Credential-Based Attacks on Organizations
Credential stuffing and brute forcing pose severe threats to organizations by enabling unauthorized access through compromised credentials. These attacks can lead to significant financial losses, data breaches, and erosion of customer trust, with credential stuffing often exploiting large sets of leaked passwords while brute forcing relies on systematically guessing credentials. Implementing multi-factor authentication and continuous monitoring reduces the risk and mitigates the operational impact of these credential-based attacks.
How Attackers Source and Use Stolen Credentials
Attackers sourcing stolen credentials often obtain them from massive data breaches, dark web marketplaces, or phishing campaigns, compiling these into credential lists for automated attacks. In credential stuffing, attackers use these pre-acquired credentials to attempt logins across multiple sites, exploiting users who reuse passwords. Brute forcing, by contrast, involves systematically generating or guessing passwords for a single account without prior knowledge, relying on computational power to break weak or common passwords.
Defending Against Credential Stuffing and Brute Forcing
Defending against credential stuffing and brute forcing requires implementing multi-factor authentication (MFA) to add an extra layer of security beyond passwords. Employing rate limiting and IP blacklisting can effectively reduce the risk by blocking rapid, repeated login attempts typically seen in these attacks. Continuous monitoring combined with anomaly detection tools further identifies and mitigates suspicious access patterns before they lead to a breach.
The Role of Multi-Factor Authentication in Mitigating Attacks
Multi-factor authentication (MFA) significantly reduces the success rate of credential stuffing and brute force attacks by requiring additional verification beyond passwords, such as biometrics or one-time codes. This extra layer of security ensures that even if attackers obtain or guess login credentials, they cannot access accounts without the secondary authentication factor. Implementing MFA across critical systems drastically minimizes unauthorized access and strengthens overall cybersecurity defenses.
Future Trends in Credential and Password Attacks
Credential stuffing and brute forcing are evolving with AI-driven automation enabling more sophisticated, large-scale attacks that bypass traditional security measures. Future trends indicate a rise in hybrid attack techniques combining credential stuffing with AI-generated password variations, exploiting leaked data and behavioral analytics weaknesses. Organizations must adopt adaptive authentication methods and leverage machine learning for anomaly detection to mitigate these increasingly complex credential and password threats.
Credential Stuffing vs Brute Forcing Infographic
 techiny.com
techiny.com