A payload in cybersecurity refers to the harmful code or malicious software delivered during a cyberattack, designed to execute specific actions like data theft or system damage. An attack vector is the method or pathway that hackers use to deliver the payload, such as phishing emails, software vulnerabilities, or compromised websites. Understanding the distinction between payload and attack vector is crucial for developing effective defense strategies and mitigating cybersecurity threats.
Table of Comparison
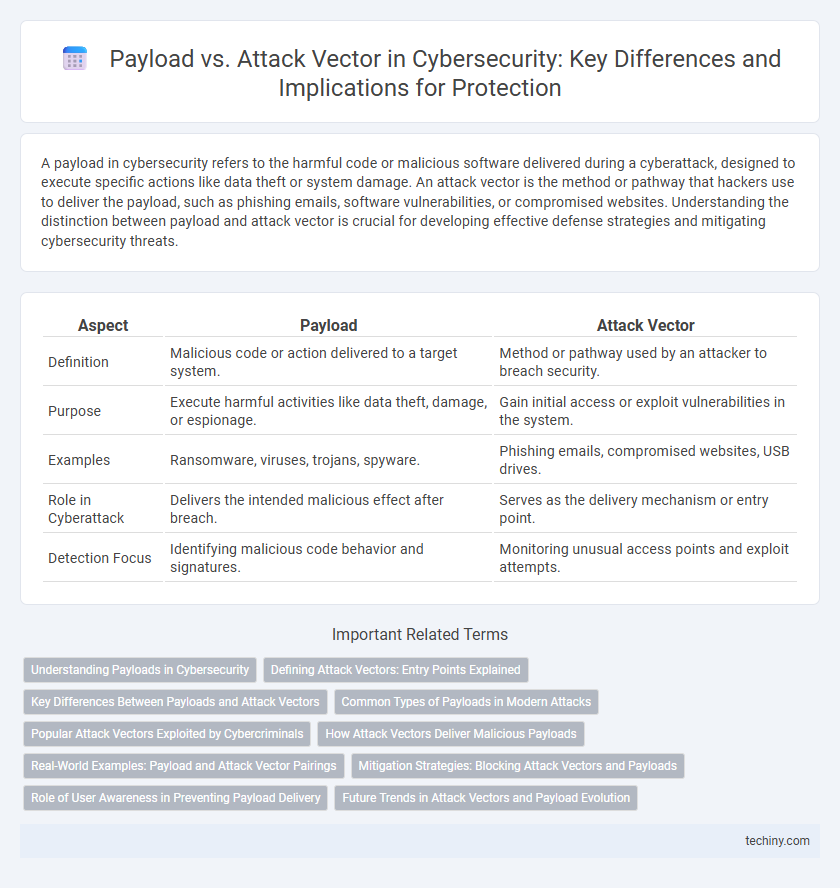
| Aspect | Payload | Attack Vector |
|---|---|---|
| Definition | Malicious code or action delivered to a target system. | Method or pathway used by an attacker to breach security. |
| Purpose | Execute harmful activities like data theft, damage, or espionage. | Gain initial access or exploit vulnerabilities in the system. |
| Examples | Ransomware, viruses, trojans, spyware. | Phishing emails, compromised websites, USB drives. |
| Role in Cyberattack | Delivers the intended malicious effect after breach. | Serves as the delivery mechanism or entry point. |
| Detection Focus | Identifying malicious code behavior and signatures. | Monitoring unusual access points and exploit attempts. |
Understanding Payloads in Cybersecurity
Payloads in cybersecurity refer to the malicious code or actions delivered by an attack vector to exploit vulnerabilities within a system, such as ransomware, spyware, or trojans. Understanding payloads involves analyzing their behavior, intent, and potential impact on confidentiality, integrity, and availability of data. Effective defense requires identifying payload characteristics and correlating them with attack vectors like phishing emails, drive-by downloads, or exploit kits for timely detection and mitigation.
Defining Attack Vectors: Entry Points Explained
Attack vectors are the specific pathways or methods cybercriminals exploit to gain unauthorized access to a network or system, serving as the critical entry points in cybersecurity breaches. These can include phishing emails, malicious websites, unsecured Wi-Fi networks, or vulnerable software applications. Understanding and identifying attack vectors is essential for implementing effective defense mechanisms to prevent payload delivery and subsequent damage.
Key Differences Between Payloads and Attack Vectors
Payloads represent the malicious code or actions delivered by a threat actor, such as ransomware, spyware, or data exfiltration tools. Attack vectors denote the methods or pathways used to infiltrate a system, including phishing emails, compromised websites, or unsecured networks. Understanding the distinction is crucial for cybersecurity defenses, as attack vectors enable delivery while payloads execute harm.
Common Types of Payloads in Modern Attacks
Common types of payloads in modern cyberattacks include ransomware, which encrypts victim data and demands payment for decryption keys, and spyware, designed to secretly gather sensitive information. Other prevalent payloads feature remote access trojans (RATs), enabling attackers to control compromised systems remotely, and keyloggers that capture every keystroke to steal credentials or other private data. Understanding the variety and function of these payloads is crucial in developing targeted defenses against sophisticated threat actors.
Popular Attack Vectors Exploited by Cybercriminals
Popular attack vectors exploited by cybercriminals include phishing emails, malware-infected websites, and unsecured Wi-Fi networks, which serve as common entry points to deliver malicious payloads. Attack vectors enable the initial breach or infiltration, while the payload executes the malicious actions such as data theft, encryption in ransomware, or system damage. Understanding these attack vectors is critical for implementing effective cybersecurity defenses like firewalls, intrusion detection systems, and employee training programs.
How Attack Vectors Deliver Malicious Payloads
Attack vectors serve as the methods or pathways through which cybercriminals deliver malicious payloads into targeted systems, exploiting vulnerabilities such as phishing emails, compromised websites, or unsecured networks. These vectors facilitate the transmission of payloads like ransomware, malware, or spyware, which execute harmful actions once inside the system. Understanding the interaction between attack vectors and payloads is essential for developing effective cybersecurity defenses and threat mitigation strategies.
Real-World Examples: Payload and Attack Vector Pairings
Ransomware often employs phishing emails as the attack vector to deliver a malicious payload that encrypts victims' data and demands payment for decryption keys. In web application attacks, SQL injection serves as the attack vector that delivers a payload designed to extract or manipulate sensitive database information. Exploit kits leverage vulnerabilities in outdated software as attack vectors to deploy payloads such as remote access Trojans (RATs) that enable unauthorized control over compromised systems.
Mitigation Strategies: Blocking Attack Vectors and Payloads
Effective mitigation strategies in cybersecurity prioritize blocking both attack vectors and payloads to reduce system vulnerabilities. Implementing robust network filtering, intrusion detection systems (IDS), and endpoint protection can prevent the delivery and execution of malicious payloads by intercepting common attack vectors such as phishing emails, drive-by downloads, and exploited software vulnerabilities. Continuous monitoring and behavioral analysis enhance the identification and neutralization of sophisticated payloads, ensuring comprehensive defense against evolving cyber threats.
Role of User Awareness in Preventing Payload Delivery
User awareness plays a critical role in disrupting attack vectors before payload delivery can occur, as informed users are more likely to recognize and avoid phishing emails, malicious links, and social engineering tactics. Effective cybersecurity training enhances a user's ability to detect suspicious activities, thereby preventing attackers from exploiting vulnerabilities to execute payloads such as malware or ransomware. Organizations that invest in continuous user education reduce the risk of successful payload delivery, strengthening their overall defense against cyber threats.
Future Trends in Attack Vectors and Payload Evolution
Emerging attack vectors increasingly exploit Internet of Things (IoT) devices and 5G network vulnerabilities, expanding the attack surface for threat actors. Payload evolution shows a shift towards modular, polymorphic malware that adapts dynamically to evade AI-driven detection systems. Future cybersecurity strategies must prioritize real-time threat intelligence and machine learning integration to counteract these advanced, multi-stage attack techniques.
Payload vs Attack Vector Infographic
 techiny.com
techiny.com