Red Team and Blue Team exercises simulate real-world cyberattack scenarios where the Red Team adopts the role of attackers attempting to exploit vulnerabilities, while the Blue Team focuses on defense by detecting, responding to, and mitigating these threats. This adversarial approach enhances organizational cybersecurity by identifying weaknesses and improving incident response strategies. Continuous collaboration and feedback between both teams foster robust security postures and proactive threat management.
Table of Comparison
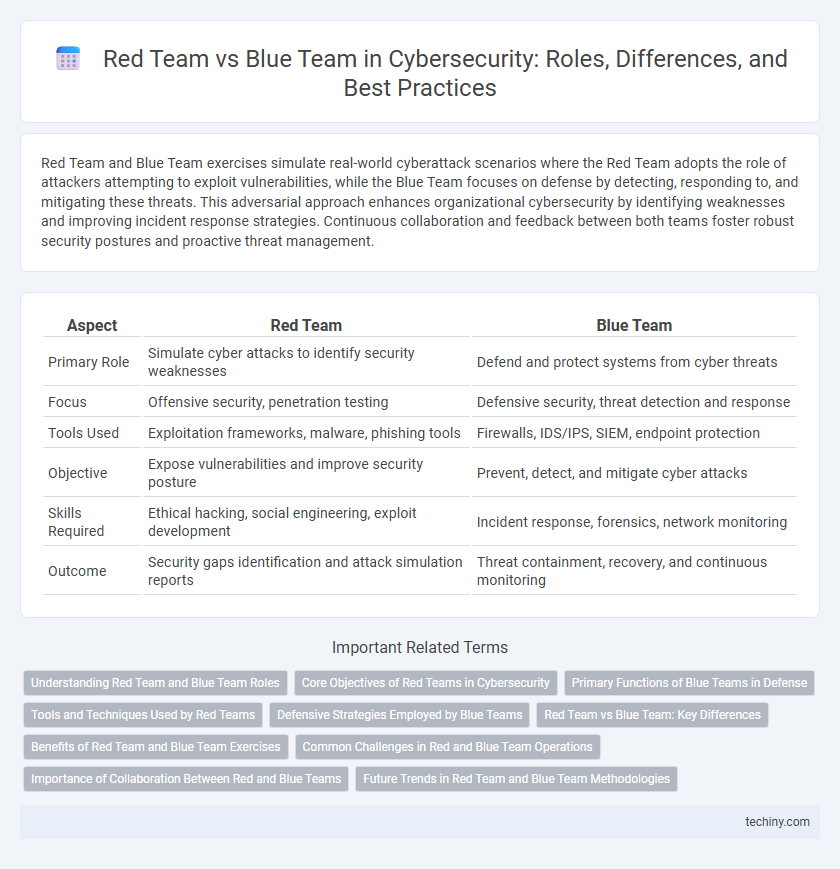
| Aspect | Red Team | Blue Team |
|---|---|---|
| Primary Role | Simulate cyber attacks to identify security weaknesses | Defend and protect systems from cyber threats |
| Focus | Offensive security, penetration testing | Defensive security, threat detection and response |
| Tools Used | Exploitation frameworks, malware, phishing tools | Firewalls, IDS/IPS, SIEM, endpoint protection |
| Objective | Expose vulnerabilities and improve security posture | Prevent, detect, and mitigate cyber attacks |
| Skills Required | Ethical hacking, social engineering, exploit development | Incident response, forensics, network monitoring |
| Outcome | Security gaps identification and attack simulation reports | Threat containment, recovery, and continuous monitoring |
Understanding Red Team and Blue Team Roles
Red Team members simulate real-world cyber attacks to identify system vulnerabilities, employing tactics like penetration testing and social engineering to test organizational defenses. Blue Team professionals focus on defending against these attacks by monitoring networks, analyzing threats, and enhancing security measures through incident response and continuous system hardening. Effective collaboration between Red Team and Blue Team roles strengthens overall cybersecurity posture by combining offensive insights with defensive expertise.
Core Objectives of Red Teams in Cybersecurity
Red Teams simulate real-world cyberattacks to identify vulnerabilities and gaps in an organization's security defenses by mimicking adversarial tactics, techniques, and procedures (TTPs). Their core objectives include testing the effectiveness of detection and response mechanisms, uncovering weaknesses in infrastructure, and providing actionable insights for strengthening security posture. Red Teams operate covertly to challenge assumptions, validate security controls, and enhance organizational resilience against sophisticated cyber threats.
Primary Functions of Blue Teams in Defense
Blue Teams in cybersecurity primarily focus on defending information systems by monitoring for threats, analyzing security data, and implementing proactive countermeasures to prevent breaches. They conduct vulnerability assessments, manage incident response protocols, and ensure continuous system hardening to maintain organizational security posture. These teams utilize advanced detection tools and threat intelligence to identify and mitigate potential cyber attacks efficiently.
Tools and Techniques Used by Red Teams
Red Teams utilize advanced penetration testing tools such as Metasploit, Cobalt Strike, and BloodHound to simulate realistic cyberattacks and identify system vulnerabilities. They employ techniques like social engineering, phishing campaigns, vulnerability scanning, and custom malware deployment to bypass defenses and test incident response. Leveraging command and control frameworks, Red Teams mimic adversary tactics to expose security gaps and improve organizational resilience.
Defensive Strategies Employed by Blue Teams
Blue Teams deploy advanced network segmentation and continuous endpoint monitoring to detect and isolate threats rapidly, minimizing potential damage. They implement real-time intrusion detection systems (IDS) alongside threat intelligence platforms to anticipate and mitigate cyberattacks effectively. Comprehensive vulnerability assessments and regular patch management form the backbone of Blue Team defensive strategies, ensuring system resilience against evolving cyber threats.
Red Team vs Blue Team: Key Differences
Red Team and Blue Team play complementary roles in cybersecurity, with the Red Team simulating real-world cyberattacks to identify vulnerabilities, while the Blue Team focuses on defense by detecting, responding to, and mitigating these threats. The Red Team employs offensive tactics such as penetration testing and social engineering, whereas the Blue Team strengthens security posture through continuous monitoring, incident response, and system hardening. Effective cybersecurity relies on the dynamic interaction between these teams to expose weaknesses and enhance organizational resilience.
Benefits of Red Team and Blue Team Exercises
Red Team exercises simulate real-world cyber attacks, identifying vulnerabilities and enhancing an organization's threat detection and response capabilities. Blue Team activities focus on defending against these simulated attacks by improving incident response protocols, security monitoring, and system hardening. Together, Red and Blue Team collaborations strengthen overall cyber resilience by fostering continuous improvement and proactive defense strategies.
Common Challenges in Red and Blue Team Operations
Red and Blue Teams frequently encounter challenges such as communication gaps that hinder effective threat simulation and response, as well as resource constraints limiting comprehensive attack and defense scenarios. Both teams struggle with staying updated on evolving cyber threats and implementing accurate detection and mitigation strategies without false positives. Balancing offensive tactics while maintaining network stability remains a persistent issue in joint cybersecurity exercises.
Importance of Collaboration Between Red and Blue Teams
Collaboration between Red and Blue Teams enhances an organization's cybersecurity by facilitating continuous threat identification and defense improvement. Red Teams simulate real-world attacks, providing critical insights that help Blue Teams strengthen detection and response mechanisms. Effective communication and joint exercises ensure adaptive security measures, reducing vulnerabilities and mitigating risks efficiently.
Future Trends in Red Team and Blue Team Methodologies
Emerging AI-driven automation is transforming Red Team tactics by enabling more sophisticated attack simulations and real-time vulnerability discovery. Blue Team methodologies are increasingly integrating advanced threat intelligence platforms and behavioral analytics to enhance proactive defense and rapid incident response. The convergence of machine learning and cloud-based security tools is driving continuous evolution in both offensive and defensive cybersecurity strategies.
Red Team vs Blue Team Infographic
 techiny.com
techiny.com