Data Loss Prevention (DLP) and Digital Rights Management (DRM) both aim to protect sensitive information but serve different purposes; DLP focuses on preventing unauthorized data breaches by monitoring and controlling data in use, in motion, and at rest, while DRM restricts access to digital content by enforcing usage policies and licensing rights. DLP solutions are essential for detecting and blocking potential data leaks across an organization's network, whereas DRM tools safeguard intellectual property by managing how content is accessed and shared post-distribution. Combining DLP with DRM provides a comprehensive cybersecurity strategy, addressing both data leakage prevention and controlled content usage.
Table of Comparison
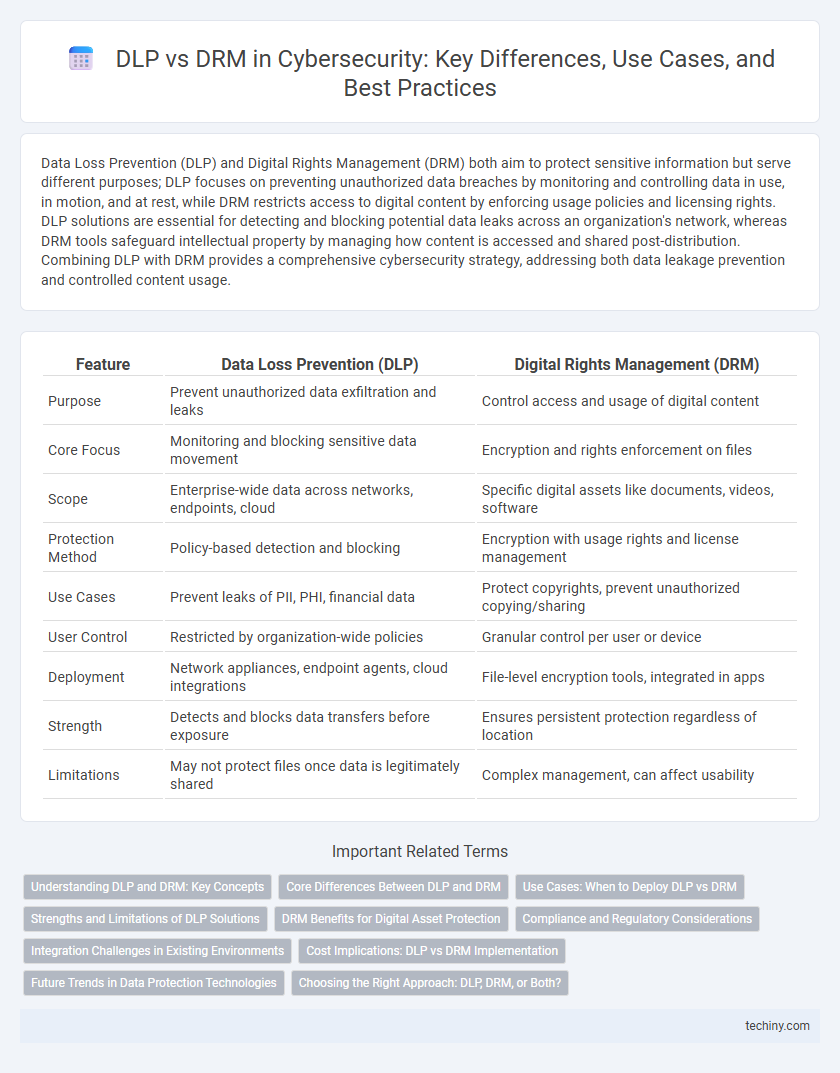
| Feature | Data Loss Prevention (DLP) | Digital Rights Management (DRM) |
|---|---|---|
| Purpose | Prevent unauthorized data exfiltration and leaks | Control access and usage of digital content |
| Core Focus | Monitoring and blocking sensitive data movement | Encryption and rights enforcement on files |
| Scope | Enterprise-wide data across networks, endpoints, cloud | Specific digital assets like documents, videos, software |
| Protection Method | Policy-based detection and blocking | Encryption with usage rights and license management |
| Use Cases | Prevent leaks of PII, PHI, financial data | Protect copyrights, prevent unauthorized copying/sharing |
| User Control | Restricted by organization-wide policies | Granular control per user or device |
| Deployment | Network appliances, endpoint agents, cloud integrations | File-level encryption tools, integrated in apps |
| Strength | Detects and blocks data transfers before exposure | Ensures persistent protection regardless of location |
| Limitations | May not protect files once data is legitimately shared | Complex management, can affect usability |
Understanding DLP and DRM: Key Concepts
Data Loss Prevention (DLP) focuses on detecting and preventing unauthorized data transfers by monitoring data in use, motion, and at rest to protect sensitive information within an organization. Digital Rights Management (DRM) controls access and usage rights of digital content, enabling content owners to enforce encryption, authentication, and licensing policies. Understanding these fundamental differences helps organizations implement comprehensive cybersecurity strategies that safeguard both data integrity and content access.
Core Differences Between DLP and DRM
Data Loss Prevention (DLP) focuses on identifying, monitoring, and blocking sensitive data exfiltration across endpoints, networks, and cloud environments, ensuring data does not leave the organization unauthorized. Digital Rights Management (DRM) emphasizes protecting content by enforcing access controls, encryption, and usage restrictions on files regardless of location, preventing unauthorized sharing or copying. Core differences include DLP's broad scope on data movement and compliance monitoring versus DRM's applied protection to specific digital assets for persistent security and control.
Use Cases: When to Deploy DLP vs DRM
DLP (Data Loss Prevention) is ideal for preventing sensitive data leaks by monitoring and controlling data in motion, at rest, and in use, particularly in organizations handling regulated information such as healthcare or finance. DRM (Digital Rights Management) is best deployed for protecting intellectual property and controlling access to digital content, ensuring that only authorized users can view, edit, or distribute sensitive documents and media. Deploy DLP when the goal is to enforce compliance policies and detect insider threats, while DRM is preferred for enforcing usage rights and preventing unauthorized sharing in content-centric environments.
Strengths and Limitations of DLP Solutions
DLP solutions excel at monitoring, detecting, and preventing sensitive data leaks across endpoints, networks, and cloud environments, providing real-time visibility and control over data in motion. Their strength lies in automated policy enforcement and comprehensive data discovery, but limitations include challenges with encrypted data inspection, high false positive rates, and difficulties in managing data in use or at rest without integration with complementary security tools. Organizations benefit from leveraging DLP as part of a layered security strategy, acknowledging its role in minimizing insider threats and accidental data exposure while addressing gaps with DRM for robust data protection.
DRM Benefits for Digital Asset Protection
Digital Rights Management (DRM) offers robust protection for digital assets by controlling access, usage, and distribution, ensuring sensitive information remains secure across multiple platforms. DRM enforces persistent encryption and strict user authentication, preventing unauthorized copying, sharing, or alteration of proprietary content. By integrating DRM, organizations can safeguard intellectual property effectively, maintain regulatory compliance, and reduce the risk of data breaches.
Compliance and Regulatory Considerations
Data Loss Prevention (DLP) and Digital Rights Management (DRM) both play critical roles in compliance with regulatory frameworks such as GDPR, HIPAA, and CCPA by protecting sensitive data from unauthorized access and exfiltration. DLP systems monitor and control data flow to prevent leaks at endpoints, networks, and cloud environments, ensuring regulatory mandates on data confidentiality and breach prevention are met. DRM focuses on enforcing access rights and usage policies on sensitive documents, maintaining compliance with intellectual property laws and contractual data sharing agreements.
Integration Challenges in Existing Environments
Integrating Data Loss Prevention (DLP) and Digital Rights Management (DRM) into existing cybersecurity infrastructures often presents significant challenges related to compatibility with legacy systems and diverse endpoint devices. Both technologies require specialized configurations to avoid conflicts with established access controls and user workflows, which can lead to increased complexity in IT management. Ensuring seamless interoperability while maintaining robust data protection demands careful planning and ongoing monitoring to mitigate performance degradation and user friction.
Cost Implications: DLP vs DRM Implementation
DLP (Data Loss Prevention) implementation typically requires ongoing expenses for monitoring tools, policy management, and employee training, making initial costs moderate but recurring costs higher. DRM (Digital Rights Management) solutions often involve significant upfront investments in encryption technologies and license management systems but can reduce long-term data misuse risks. Evaluating total cost of ownership for both solutions is essential, considering factors like scalability, integration complexity, and potential data breach penalties.
Future Trends in Data Protection Technologies
Emerging trends in data protection technologies highlight the convergence of Data Loss Prevention (DLP) and Digital Rights Management (DRM) through AI-driven behavior analytics and zero-trust architectures to enhance real-time content control and threat detection. Integration of cloud-native DLP solutions with DRM frameworks enables dynamic policy enforcement across hybrid environments, securing sensitive data against insider threats and external breaches. Innovations such as automated encryption, machine learning-based anomaly detection, and blockchain for immutable audit trails are shaping the future landscape of comprehensive data security.
Choosing the Right Approach: DLP, DRM, or Both?
Choosing the right approach between Data Loss Prevention (DLP) and Digital Rights Management (DRM) depends on the organization's specific cybersecurity needs and data protection goals. DLP focuses on monitoring, detecting, and preventing unauthorized data transfers or leaks, ideal for controlling endpoint activities and network traffic. DRM offers robust protection through encryption and access controls to secure sensitive content, making it essential for managing intellectual property and ensuring compliance with regulatory requirements.
DLP vs DRM Infographic
 techiny.com
techiny.com