SIEM (Security Information and Event Management) platforms provide real-time analysis of security alerts generated by applications and network hardware, offering advanced threat detection and incident response capabilities. Log management focuses primarily on the collection, storage, and retrieval of log data, enabling compliance and basic troubleshooting without the proactive security insights. While log management serves as a foundation, SIEM integrates and correlates log data for comprehensive security monitoring and faster breach detection.
Table of Comparison
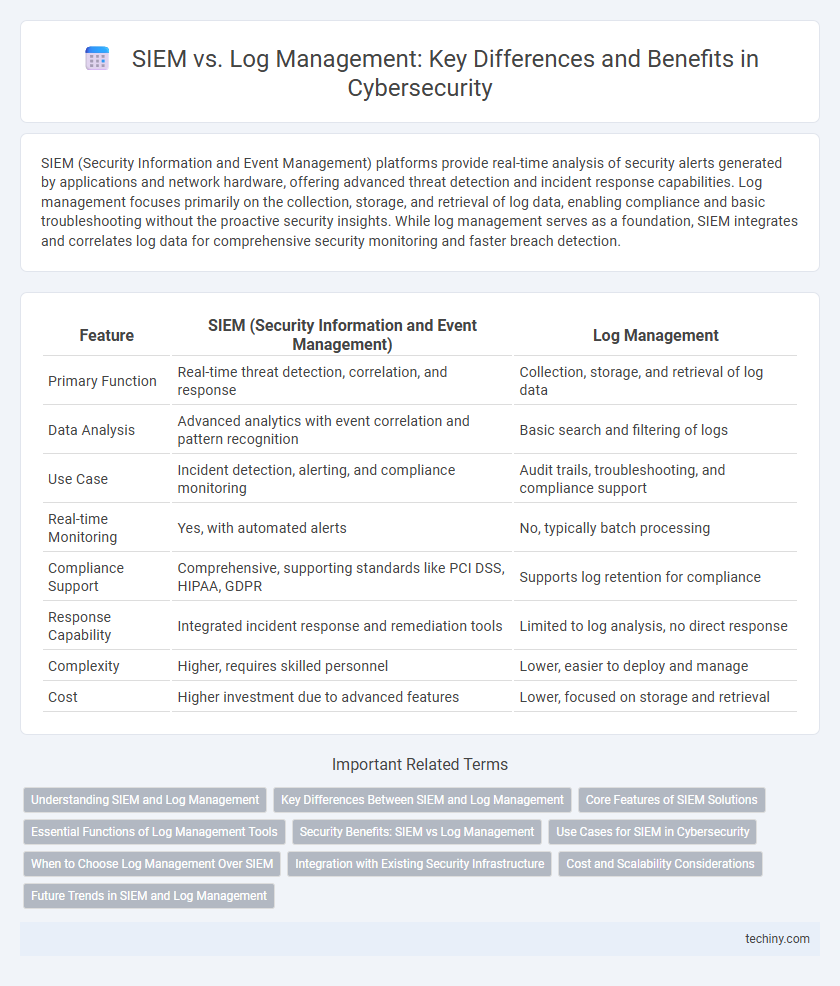
| Feature | SIEM (Security Information and Event Management) | Log Management |
|---|---|---|
| Primary Function | Real-time threat detection, correlation, and response | Collection, storage, and retrieval of log data |
| Data Analysis | Advanced analytics with event correlation and pattern recognition | Basic search and filtering of logs |
| Use Case | Incident detection, alerting, and compliance monitoring | Audit trails, troubleshooting, and compliance support |
| Real-time Monitoring | Yes, with automated alerts | No, typically batch processing |
| Compliance Support | Comprehensive, supporting standards like PCI DSS, HIPAA, GDPR | Supports log retention for compliance |
| Response Capability | Integrated incident response and remediation tools | Limited to log analysis, no direct response |
| Complexity | Higher, requires skilled personnel | Lower, easier to deploy and manage |
| Cost | Higher investment due to advanced features | Lower, focused on storage and retrieval |
Understanding SIEM and Log Management
Security Information and Event Management (SIEM) integrates real-time analysis of security alerts generated by applications and network hardware, providing comprehensive threat detection and incident response capabilities. Log Management focuses on the collection, storage, and basic analysis of log data from various sources, enabling compliance and forensic investigations. The core difference lies in SIEM's advanced correlation and real-time monitoring features versus Log Management's emphasis on centralized log aggregation and retention.
Key Differences Between SIEM and Log Management
SIEM (Security Information and Event Management) integrates real-time analysis of security alerts from network hardware and applications, whereas log management primarily focuses on the collection, storage, and retrieval of log data. SIEM platforms utilize correlation and advanced analytics to detect security incidents, while log management systems provide centralized log aggregation without in-depth event correlation. The key differences lie in SIEM's proactive threat detection capabilities versus log management's role in compliance and forensic investigations through comprehensive log retention.
Core Features of SIEM Solutions
SIEM solutions integrate real-time event correlation, advanced threat detection, and automated incident response to provide comprehensive cybersecurity monitoring. They consolidate log data from diverse sources and apply analytics to identify anomalies, ensuring rapid detection of potential security breaches. Core SIEM features include centralized log management, customizable alerting, and compliance reporting to enhance organizational security posture.
Essential Functions of Log Management Tools
Log management tools primarily focus on the collection, storage, and analysis of log data to enhance visibility across IT environments, enabling efficient identification of system anomalies and potential security threats. These tools support essential functions such as centralized log aggregation, real-time event monitoring, and compliance reporting, which are critical for forensic investigations and regulatory adherence. Effective log management lays the foundation for advanced Security Information and Event Management (SIEM) systems that provide correlation, alerting, and threat detection capabilities.
Security Benefits: SIEM vs Log Management
SIEM solutions provide advanced security benefits by correlating log data from multiple sources to detect and respond to threats in real time, enhancing incident detection and reducing response times. Log management focuses primarily on collecting, storing, and retrieving log data for compliance and forensic analysis but lacks the proactive threat identification capabilities of SIEM. Implementing SIEM strengthens security posture through automated alerting and comprehensive analysis, whereas log management serves as a foundational tool for maintaining visibility and audit trails.
Use Cases for SIEM in Cybersecurity
SIEM (Security Information and Event Management) platforms provide real-time analysis of security alerts generated by applications and network hardware, crucial for threat detection, incident response, and compliance reporting. Unlike traditional log management which primarily focuses on log storage and retrieval, SIEM integrates log data from diverse sources to identify patterns indicative of cyber threats such as breaches, insider attacks, and advanced persistent threats (APTs). Key use cases for SIEM in cybersecurity include automated correlation of security events, continuous monitoring for suspicious activity, and forensic investigations following security incidents.
When to Choose Log Management Over SIEM
Log management is ideal for organizations seeking cost-effective, scalable solutions primarily for collecting, storing, and analyzing large volumes of log data without the complexity of real-time threat detection. When the primary need is compliance reporting, historical data retention, and basic troubleshooting, log management provides a simpler framework compared to SIEM. Enterprises with limited security teams or smaller IT environments often choose log management to maintain visibility while avoiding the resource-intensive demands of full SIEM deployment.
Integration with Existing Security Infrastructure
SIEM platforms offer comprehensive integration with existing security infrastructure by aggregating data from firewalls, intrusion detection systems, and endpoint protection tools to enable real-time analysis and incident response. Log management solutions primarily focus on collecting, storing, and indexing log data but may lack advanced correlation and alerting capabilities inherent in SIEM systems. Effective integration ensures streamlined threat detection, compliance reporting, and centralized security operations across diverse enterprise environments.
Cost and Scalability Considerations
SIEM platforms often involve higher upfront and ongoing costs due to their advanced correlation, threat detection, and compliance capabilities, whereas log management solutions tend to be more cost-effective for basic storage and retrieval tasks. Scalability in SIEMs is crucial as data volumes increase exponentially, potentially requiring significant infrastructure investment or cloud-based scaling options; log management tools generally scale more easily but lack the sophisticated analytics of SIEM. Cost optimization for enterprises hinges on balancing the need for in-depth threat analysis with budget constraints, favoring SIEM for complex environments and log management for smaller or less security-intensive operations.
Future Trends in SIEM and Log Management
Future trends in SIEM (Security Information and Event Management) emphasize the integration of artificial intelligence and machine learning to enhance threat detection and response accuracy. Log management systems are evolving to handle exponentially growing data volumes with improved scalability and real-time analytics capabilities. The convergence of SIEM and log management is driving proactive cybersecurity measures through advanced automation and predictive insights.
SIEM vs Log Management Infographic
 techiny.com
techiny.com