Rainbow table attacks exploit precomputed hash values to quickly reverse cryptographic hashes, significantly reducing the time required to crack passwords compared to brute force attacks. Brute force attacks systematically attempt every possible password combination without prior knowledge, making them more time-consuming and resource-intensive. Implementing strong salting techniques effectively mitigates rainbow table attacks by ensuring each password hash is unique and resistant to these precomputed lookup methods.
Table of Comparison
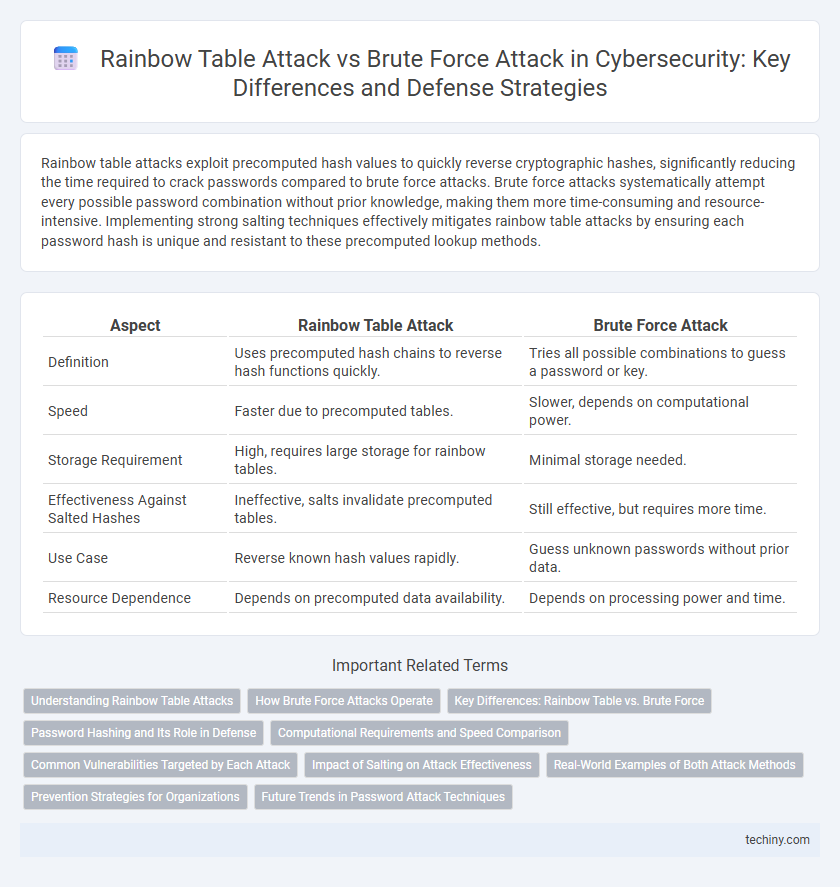
| Aspect | Rainbow Table Attack | Brute Force Attack |
|---|---|---|
| Definition | Uses precomputed hash chains to reverse hash functions quickly. | Tries all possible combinations to guess a password or key. |
| Speed | Faster due to precomputed tables. | Slower, depends on computational power. |
| Storage Requirement | High, requires large storage for rainbow tables. | Minimal storage needed. |
| Effectiveness Against Salted Hashes | Ineffective, salts invalidate precomputed tables. | Still effective, but requires more time. |
| Use Case | Reverse known hash values rapidly. | Guess unknown passwords without prior data. |
| Resource Dependence | Depends on precomputed data availability. | Depends on processing power and time. |
Understanding Rainbow Table Attacks
Rainbow table attacks exploit precomputed hash chains to reverse cryptographic hash functions more efficiently than brute force attacks, which rely on exhaustive guessing of every possible password. These attacks leverage vast databases of hash-value pairs to quickly identify original passwords, significantly reducing the time required compared to brute force methods. Effective defenses include salting hashes and using computationally intensive hashing algorithms to render rainbow tables impractical.
How Brute Force Attacks Operate
Brute force attacks operate by systematically attempting every possible combination of characters to crack passwords or encryption keys, relying on computational power to exhaust all options. These attacks leverage algorithms that incrementally test password guesses, often starting from simple patterns and progressing to complex strings, until the correct credential is found. Unlike rainbow table attacks that use precomputed hash databases, brute force attacks directly engage with the system, making their success dependent on processing speed and password complexity.
Key Differences: Rainbow Table vs. Brute Force
Rainbow table attacks leverage precomputed hash values to reverse cryptographic hashes efficiently, significantly reducing the time to crack passwords compared to brute force attacks. Brute force attacks systematically try all possible combinations without prior knowledge, making them slower and more resource-intensive. The key difference lies in the use of precomputed data in rainbow tables versus real-time exhaustive search in brute force methods.
Password Hashing and Its Role in Defense
Rainbow table attacks exploit precomputed hash chains to reverse password hashes efficiently, undermining weak or unsalted password hashing schemes. Brute force attacks systematically attempt every possible password combination, relying heavily on computational power and strong hashing algorithms with high computational costs to slow down cracking attempts. Employing salted hashes combined with adaptive hashing algorithms like bcrypt, scrypt, or Argon2 significantly enhances defense by preventing rainbow table use and increasing brute force attack difficulty.
Computational Requirements and Speed Comparison
Rainbow table attacks leverage precomputed hash values to dramatically reduce the time needed to crack passwords, significantly lowering computational requirements compared to brute force attacks. Brute force attacks, attempting every possible combination, demand exponentially higher processing power and time as password length and complexity increase. Consequently, rainbow table attacks offer much faster results against poorly salted passwords, while brute force remains the most resource-intensive but universally applicable method.
Common Vulnerabilities Targeted by Each Attack
Rainbow table attacks commonly target weak or unsalted hashed passwords stored in databases, exploiting precomputed hash values to quickly reverse-engineer user credentials. Brute force attacks focus on cracking passwords or encryption keys by systematically trying all possible combinations, often targeting systems with short or simple password policies. Both attacks exploit vulnerabilities in password complexity and storage practices, emphasizing the need for strong salts and robust password requirements to enhance cybersecurity defenses.
Impact of Salting on Attack Effectiveness
Salting significantly reduces the effectiveness of both rainbow table and brute force attacks by adding unique random data to each password before hashing. This randomization makes precomputed rainbow tables obsolete since attackers must generate new tables for each salt value, exponentially increasing computational effort. In brute force attacks, salting forces attackers to target each password hash individually, preventing the reuse of computations across multiple hashes and substantially increasing the time and resources needed for successful breaches.
Real-World Examples of Both Attack Methods
Rainbow table attacks famously compromised the LinkedIn breach in 2012, where attackers exploited precomputed hash tables to crack millions of weakly salted passwords swiftly. Conversely, brute force attacks were notably used during the 2017 WannaCry ransomware outbreak, where attackers systematically tried numerous password combinations to gain unauthorized access to systems. Both methods highlight the urgent need for strong password policies and advanced hash salting techniques to mitigate such cybersecurity risks.
Prevention Strategies for Organizations
Implementing strong, unique passwords combined with salting techniques significantly reduces the risk of rainbow table attacks by rendering precomputed hashes ineffective. Organizations should deploy multi-factor authentication and rate-limiting mechanisms to mitigate brute force attacks, preventing automated, repeated login attempts. Regularly updating security protocols and conducting penetration testing further strengthens defenses against both attack vectors.
Future Trends in Password Attack Techniques
Emerging trends in password attack techniques highlight increasing sophistication beyond traditional brute force and rainbow table attacks, driven by advancements in computational power and AI algorithms. Quantum computing is expected to dramatically reduce the time required for cracking hashed passwords, rendering current encryption standards vulnerable. Machine learning models now facilitate smarter password guessing strategies, combining pattern recognition with social engineering data to optimize attack efficiency.
rainbow table attack vs brute force attack Infographic
 techiny.com
techiny.com