Air gaps provide physical isolation by completely separating critical systems from unsecured networks, significantly reducing the risk of remote cyberattacks. Sandboxes offer a controlled, virtual environment where potentially malicious code is executed safely to analyze behavior without impacting host systems. Combining air gaps with sandboxing enhances security by isolating sensitive assets while enabling dynamic threat detection and analysis.
Table of Comparison
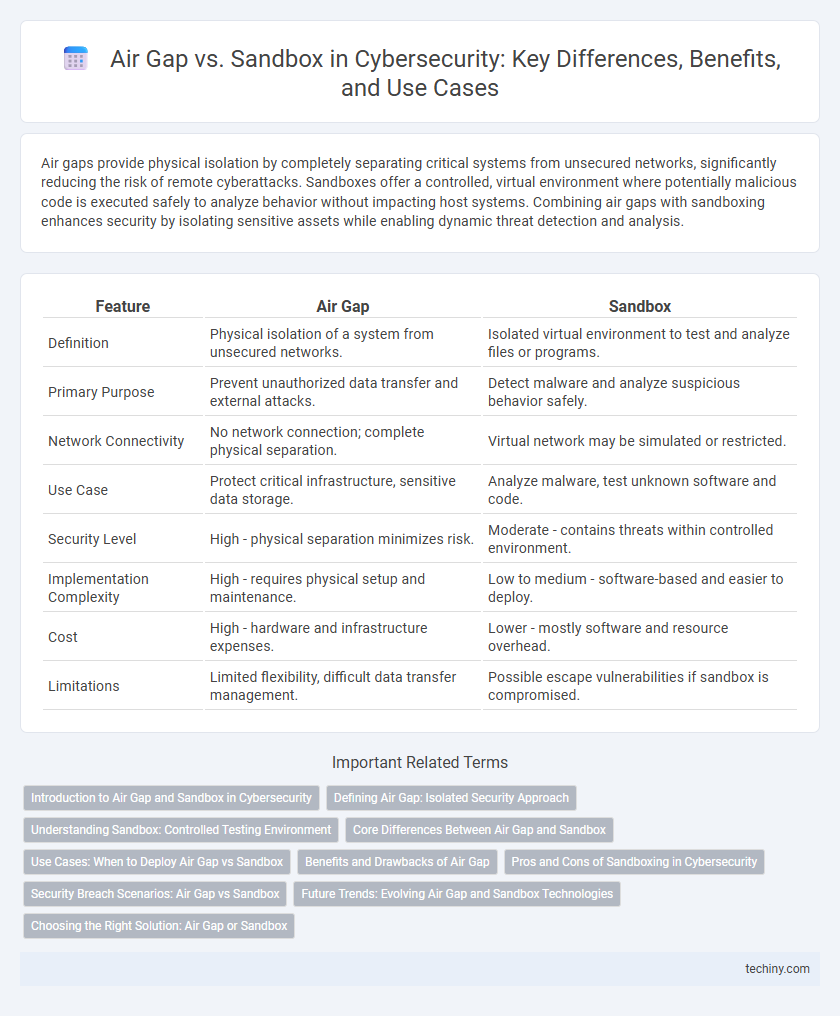
| Feature | Air Gap | Sandbox |
|---|---|---|
| Definition | Physical isolation of a system from unsecured networks. | Isolated virtual environment to test and analyze files or programs. |
| Primary Purpose | Prevent unauthorized data transfer and external attacks. | Detect malware and analyze suspicious behavior safely. |
| Network Connectivity | No network connection; complete physical separation. | Virtual network may be simulated or restricted. |
| Use Case | Protect critical infrastructure, sensitive data storage. | Analyze malware, test unknown software and code. |
| Security Level | High - physical separation minimizes risk. | Moderate - contains threats within controlled environment. |
| Implementation Complexity | High - requires physical setup and maintenance. | Low to medium - software-based and easier to deploy. |
| Cost | High - hardware and infrastructure expenses. | Lower - mostly software and resource overhead. |
| Limitations | Limited flexibility, difficult data transfer management. | Possible escape vulnerabilities if sandbox is compromised. |
Introduction to Air Gap and Sandbox in Cybersecurity
An air gap in cybersecurity refers to a physical or logical separation between secure systems and unsecured networks, preventing direct data transfer and minimizing exposure to cyber threats. Sandboxing involves isolating running programs or files in a controlled environment to analyze behavior and detect malicious activity without risking the host system. Both approaches enhance security by containing potential breaches and limiting unauthorized access to critical assets.
Defining Air Gap: Isolated Security Approach
An air gap is a cybersecurity measure that involves physically isolating a computer or network from unsecured networks, such as the internet, to prevent unauthorized access and cyber threats. This isolated security approach ensures that sensitive systems remain disconnected, eliminating potential attack vectors exploited in connected environments. Unlike sandboxes, which safely analyze suspicious files or code within a controlled virtual environment, air gaps provide a robust, physical barrier to safeguard critical infrastructure and highly confidential data.
Understanding Sandbox: Controlled Testing Environment
A sandbox is a controlled testing environment designed to safely execute, analyze, and observe suspicious files or code without risking system integrity or data breaches. Unlike air gaps that physically isolate systems to prevent unauthorized access, sandboxes use virtualized environments to simulate real-world interactions and detect malware behavior in real-time. This controlled containment allows cybersecurity professionals to study threats, test patches, and develop defense mechanisms without exposing critical infrastructure.
Core Differences Between Air Gap and Sandbox
Air gap technology physically isolates a network or device from unsecured networks, ensuring zero connectivity to the internet and preventing remote cyber threats, while a sandbox creates a virtualized environment to safely execute and analyze untrusted code without affecting the host system. Air gaps provide maximum security by eliminating external access, ideal for critical infrastructure like military or industrial control systems, whereas sandboxes offer dynamic malware detection and behavioral analysis, commonly used in endpoint security solutions. Core differences lie in physical isolation versus virtual containment, the scope of threat mitigation, and application depending on security needs and operational flexibility.
Use Cases: When to Deploy Air Gap vs Sandbox
Air gaps are critical for isolating highly sensitive systems such as nuclear plant controls or classified government networks where complete physical separation from external networks prevents any cyber intrusion risk. Sandboxes excel in dynamic threat analysis environments, allowing cybersecurity teams to safely execute and observe suspicious files or code behavior without risking system integrity in corporate networks or software development stages. Deploy air gaps for maximum security when data confidentiality is paramount, and deploy sandboxes for real-time malware detection and behavioral analysis.
Benefits and Drawbacks of Air Gap
Air gap security creates an isolated network environment physically disconnected from external connections, significantly reducing the risk of remote cyberattacks and unauthorized access. This method ensures maximum protection for sensitive data by preventing malware infiltration through network vulnerabilities but limits accessibility and real-time data sharing, posing operational challenges. The primary drawback of air gap systems lies in the complexity of maintenance and updates, requiring manual intervention that can delay critical security patches and increase human error risks.
Pros and Cons of Sandboxing in Cybersecurity
Sandboxing in cybersecurity allows untrusted code to execute in an isolated environment, minimizing the risk of malware spreading to critical systems. It offers rapid testing and analysis of suspicious files or applications without affecting the main network, but may fail against sophisticated attacks that detect the sandbox environment or exploit zero-day vulnerabilities. Despite limitations, sandboxing enhances threat detection and response capabilities by containing potential threats before deployment.
Security Breach Scenarios: Air Gap vs Sandbox
Air gap security prevents breaches by physically isolating critical systems from all networks, eliminating remote access and reducing malware spread risk. Sandboxes allow controlled execution of untrusted code within a virtual environment to detect exploits and minimize damage if a breach occurs. Comparing both, air gaps provide stronger protection against network-based attacks while sandboxes offer dynamic threat analysis but remain vulnerable if isolation fails.
Future Trends: Evolving Air Gap and Sandbox Technologies
Future trends in cybersecurity highlight the evolution of air gap and sandbox technologies through integration with AI-driven threat detection and automated response systems. Advanced air gap solutions now incorporate real-time monitoring and anomaly detection to mitigate sophisticated cyber risks in isolated environments. Sandbox environments are increasingly leveraging machine learning algorithms to simulate complex attack vectors, enabling proactive defense against emerging malware.
Choosing the Right Solution: Air Gap or Sandbox
Choosing between an air gap and a sandbox depends on the security requirements and operational constraints of the organization. Air gaps provide maximum isolation by physically separating critical systems from unsecured networks, minimizing the risk of data exfiltration or remote attacks. Sandboxes offer controlled environments for safely analyzing suspicious files or malware behaviors, ideal for dynamic threat detection without disrupting production systems.
Air gap vs sandbox Infographic
 techiny.com
techiny.com