Token-based authentication offers scalability and simplicity for IoT devices by using lightweight tokens that reduce processing overhead and improve speed. Certificate-based authentication provides stronger security through cryptographic certificates, ensuring device identity verification and secure communication in complex IoT ecosystems. Choosing between them depends on the required balance between security level and resource constraints of the IoT environment.
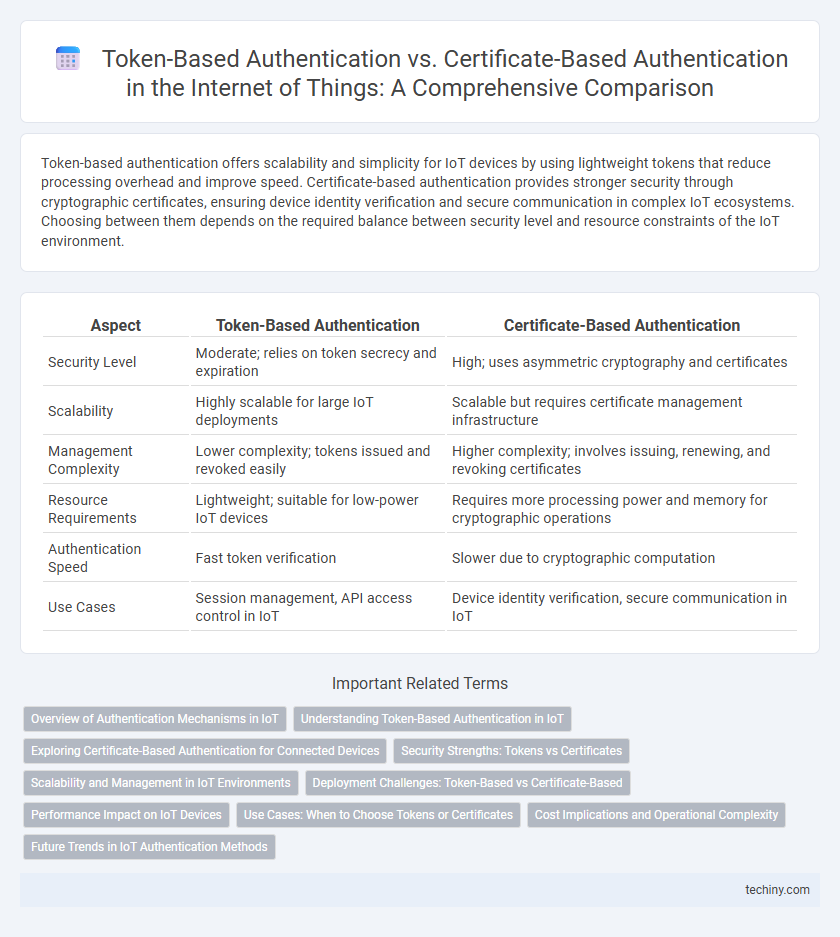
Table of Comparison
| Aspect | Token-Based Authentication | Certificate-Based Authentication |
|---|---|---|
| Security Level | Moderate; relies on token secrecy and expiration | High; uses asymmetric cryptography and certificates |
| Scalability | Highly scalable for large IoT deployments | Scalable but requires certificate management infrastructure |
| Management Complexity | Lower complexity; tokens issued and revoked easily | Higher complexity; involves issuing, renewing, and revoking certificates |
| Resource Requirements | Lightweight; suitable for low-power IoT devices | Requires more processing power and memory for cryptographic operations |
| Authentication Speed | Fast token verification | Slower due to cryptographic computation |
| Use Cases | Session management, API access control in IoT | Device identity verification, secure communication in IoT |
Overview of Authentication Mechanisms in IoT
Token-based authentication in IoT leverages unique tokens exchanged between devices and servers to verify identity, enabling lightweight and scalable access control suitable for constrained environments. Certificate-based authentication employs digital certificates issued by trusted Certificate Authorities, ensuring robust security through cryptographic validation and mutual device authentication. Both mechanisms address critical IoT challenges such as device heterogeneity and scalability, with token-based methods favored for simplicity and certificate-based systems for enhanced security and trust management.
Understanding Token-Based Authentication in IoT
Token-based authentication in IoT enables secure device access by generating unique tokens that validate user identity without transmitting credentials repeatedly, reducing the risk of interception. These tokens, often time-limited and encrypted, streamline the authentication process for resource-constrained IoT devices by minimizing computational overhead compared to traditional methods. Implementing token-based authentication enhances scalability and flexibility in large IoT ecosystems by allowing seamless device interaction and dynamic access control.
Exploring Certificate-Based Authentication for Connected Devices
Certificate-based authentication for connected devices in the Internet of Things (IoT) enhances security by using digital certificates issued by trusted Certificate Authorities (CAs) to verify device identities. This method ensures robust protection against unauthorized access and supports scalable device management through automated certificate lifecycle processes. Compared to token-based authentication, certificate-based approaches offer stronger resistance to token theft and replay attacks, making them ideal for critical IoT deployments requiring high levels of trust and confidentiality.
Security Strengths: Tokens vs Certificates
Token-based authentication offers strong security by generating time-limited, single-use credentials that minimize the risk of replay attacks and unauthorized access in IoT environments. Certificate-based authentication provides robust identity validation through asymmetric cryptography and digital certificates issued by trusted Certificate Authorities, ensuring device authenticity and data integrity. Both methods enhance IoT security, with tokens excelling in lightweight, scalable scenarios and certificates offering stronger protection against man-in-the-middle attacks and impersonation.
Scalability and Management in IoT Environments
Token-based authentication offers superior scalability in IoT environments by enabling lightweight credential management and rapid validation across numerous devices, making it suitable for large-scale deployments. Certificate-based authentication provides robust security through cryptographic credentials but often incurs higher management overhead, including certificate issuance, renewal, and revocation processes that may challenge scalability. Effective IoT security architectures balance the lightweight scalability of tokens with the strong trust assurances of certificates to optimize device management and operational efficiency.
Deployment Challenges: Token-Based vs Certificate-Based
Token-based authentication in IoT deployments often faces scalability issues due to token management overhead and frequent renewal requirements, impacting device performance and network efficiency. Certificate-based authentication demands a robust public key infrastructure (PKI), which can be complex and costly to deploy, requiring secure certificate issuance, storage, and revocation processes across diverse IoT devices. Both methods present unique deployment challenges, with tokens favoring simpler implementation but limited scalability, while certificates offer stronger security at the expense of higher operational complexity.
Performance Impact on IoT Devices
Token-based authentication offers lightweight processing and faster validation, making it suitable for resource-constrained IoT devices by minimizing CPU and memory usage. Certificate-based authentication, while providing stronger security through asymmetric cryptography, imposes higher computational overhead and increased latency due to certificate verification and public-key operations. IoT devices with limited processing power and battery life often experience reduced performance and shorter operational lifespan when using certificate-based methods compared to token-based approaches.
Use Cases: When to Choose Tokens or Certificates
Token-based authentication suits IoT scenarios requiring lightweight, scalable access control such as smart home devices and wearables, where quick, stateless verification is essential. Certificate-based authentication excels in environments demanding strong, mutual authentication and encrypted communication, including industrial automation and critical infrastructure networks. Choosing between tokens and certificates depends on device capabilities, security requirements, and network complexity within the IoT deployment.
Cost Implications and Operational Complexity
Token-based authentication offers lower upfront costs and simpler deployment in IoT environments due to minimal infrastructure requirements, making it suitable for large-scale, resource-constrained devices. Certificate-based authentication involves higher costs related to certificate issuance, management, and renewal, along with increased operational complexity from maintaining Public Key Infrastructure (PKI) and handling certificate revocation processes. Organizations must balance cost efficiency and security demands when choosing between token-based and certificate-based authentication methods for IoT device management.
Future Trends in IoT Authentication Methods
Token-based authentication in IoT offers lightweight, scalable security ideal for resource-constrained devices, whereas certificate-based authentication provides robust identity verification through public key infrastructure (PKI), ensuring enhanced data integrity and device trust. Future trends in IoT authentication emphasize hybrid models combining token and certificate mechanisms, leveraging blockchain for decentralized trust and quantum-resistant cryptographic algorithms to counter emerging cyber threats. Advancements in AI-driven anomaly detection will further augment authentication processes, enabling real-time threat identification and adaptive security measures in complex IoT ecosystems.
Token-based authentication vs Certificate-based authentication Infographic
 techiny.com
techiny.com