Access Control Lists (ACLs) provide basic packet filtering by defining rules that permit or deny traffic based on IP addresses, ports, or protocols, primarily used within routers and switches for granular control. Firewalls offer a more comprehensive security solution by inspecting traffic at multiple layers, applying stateful inspection, and blocking unwanted connections to protect entire networks from threats. While ACLs are efficient for simple traffic control, firewalls deliver advanced protection essential for robust network security.
Table of Comparison
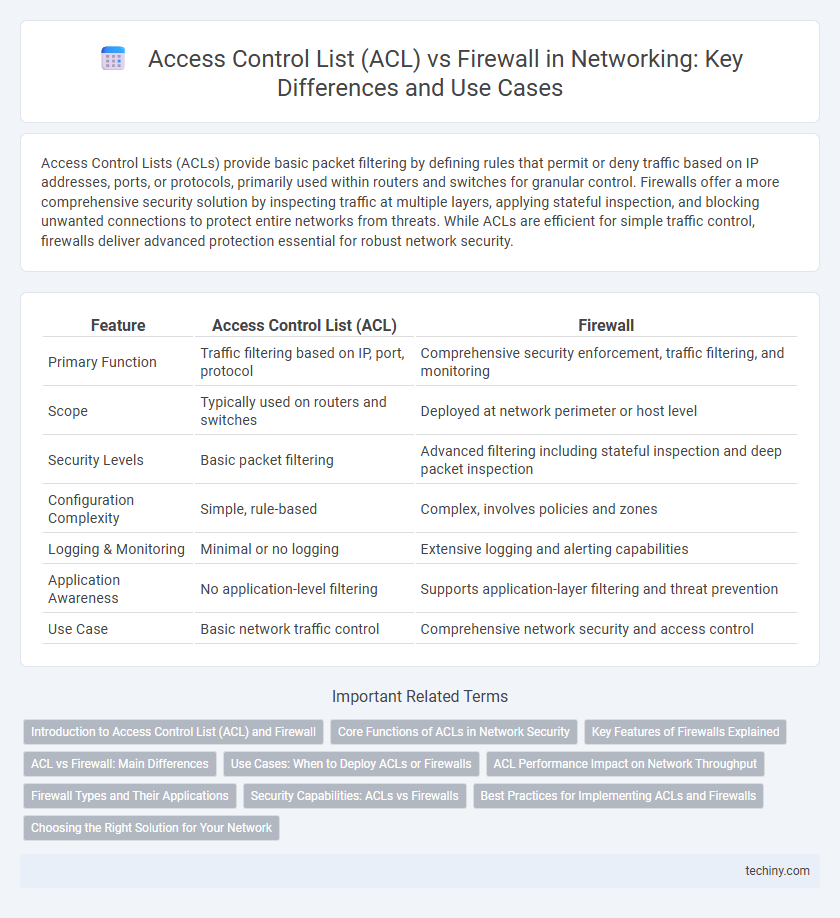
| Feature | Access Control List (ACL) | Firewall |
|---|---|---|
| Primary Function | Traffic filtering based on IP, port, protocol | Comprehensive security enforcement, traffic filtering, and monitoring |
| Scope | Typically used on routers and switches | Deployed at network perimeter or host level |
| Security Levels | Basic packet filtering | Advanced filtering including stateful inspection and deep packet inspection |
| Configuration Complexity | Simple, rule-based | Complex, involves policies and zones |
| Logging & Monitoring | Minimal or no logging | Extensive logging and alerting capabilities |
| Application Awareness | No application-level filtering | Supports application-layer filtering and threat prevention |
| Use Case | Basic network traffic control | Comprehensive network security and access control |
Introduction to Access Control List (ACL) and Firewall
Access Control Lists (ACLs) are network security tools that filter traffic by defining rules based on IP addresses, protocols, and ports to permit or deny data packets at routers or switches. Firewalls operate as comprehensive security systems that monitor and control incoming and outgoing network traffic through established security policies, often encompassing stateful inspection and application-layer filtering. Both ACLs and firewalls serve to enforce network access control, but ACLs typically focus on packet-level filtering while firewalls provide broader, multi-layer protection mechanisms.
Core Functions of ACLs in Network Security
Access Control Lists (ACLs) primarily filter traffic by defining specific rules that permit or deny packets based on IP addresses, protocols, and ports, serving as the first line of defense in network security. Unlike firewalls, ACLs operate at the router or switch level, providing granular control over inbound and outbound traffic within network segments. Their core function includes enforcing security policies, regulating traffic flow, and preventing unauthorized access by applying rule-based filters directly on network interfaces.
Key Features of Firewalls Explained
Firewalls provide comprehensive network security by filtering traffic based on defined rules, segmenting networks, and monitoring for suspicious activity through stateful inspection and deep packet inspection. Key features include intrusion prevention, application awareness, and the ability to create granular policies that control both inbound and outbound traffic across multiple layers. Firewalls also support VPN connectivity, logging, and real-time threat intelligence integration, offering a more robust defense compared to basic Access Control Lists (ACLs) that primarily focus on IP or port filtering.
ACL vs Firewall: Main Differences
Access Control Lists (ACLs) are packet-filtering mechanisms used primarily in routers to control traffic based on IP addresses, protocols, or port numbers, enabling basic network access management. Firewalls provide advanced security functions, including stateful inspection, intrusion prevention, and application-layer filtering, offering comprehensive protection beyond simple packet filtering. ACLs operate at the network layer and are limited in scope, whereas firewalls operate across multiple OSI layers and incorporate sophisticated policies to defend against diverse cyber threats.
Use Cases: When to Deploy ACLs or Firewalls
Access Control Lists (ACLs) are ideal for controlling traffic based on IP addresses and protocols within routers and switches, providing low-latency filtering for internal network segments or specific subnets. Firewalls excel in protecting entire network perimeters by offering advanced inspection, stateful filtering, and application-layer control to block unauthorized access and detect intrusions. Deploy ACLs for simple, rule-based traffic management and firewalls when comprehensive security policies, threat prevention, and detailed logging are required.
ACL Performance Impact on Network Throughput
Access Control Lists (ACLs) directly influence network throughput by filtering packets at the router or switch level, which can introduce latency depending on the complexity and number of ACL rules applied. Unlike firewalls that perform deep packet inspection with security features, ACLs primarily operate on layer 3 and 4 headers, offering faster processing but limited granular control. Efficient ACL design minimizes performance degradation by applying specific, streamlined rules targeting key traffic flows to maintain optimized network throughput.
Firewall Types and Their Applications
Firewalls are categorized into several types, including packet-filtering, stateful inspection, proxy, and next-generation firewalls (NGFW), each serving distinct security functions. Packet-filtering firewalls operate at the network layer to control traffic based on IP addresses and ports, while stateful inspection firewalls monitor active connections to ensure data packet integrity. NGFWs integrate traditional firewall capabilities with advanced features like intrusion prevention, application awareness, and deep packet inspection, making them ideal for complex network environments requiring robust threat detection.
Security Capabilities: ACLs vs Firewalls
Access Control Lists (ACLs) provide basic packet filtering by allowing or denying traffic based on IP addresses, protocols, and ports, offering stateless security at the network layer. Firewalls deliver advanced security capabilities including stateful inspection, deep packet inspection, intrusion prevention, and application-level filtering, enabling comprehensive threat mitigation. Firewalls are better suited for dynamic and granular control over network traffic compared to ACLs, which lack context-awareness and cannot inspect packet payloads.
Best Practices for Implementing ACLs and Firewalls
Implementing Access Control Lists (ACLs) and firewalls effectively requires defining clear security policies that specify permitted and denied traffic based on IP addresses, protocols, and ports. Best practices include regularly updating ACL rules to reflect current network needs, minimizing rule complexity to improve performance, and placing ACLs near the network edge to filter traffic early. Firewalls should be configured with layered rulesets, logging enabled for audit trails, and integrated with intrusion detection systems to enhance threat response.
Choosing the Right Solution for Your Network
Access Control Lists (ACLs) provide granular traffic filtering based on IP addresses and protocols, ideal for controlling access within internal network segments. Firewalls offer comprehensive security by inspecting traffic at multiple layers, including application-level controls and stateful inspection, making them better suited for perimeter defense. Selecting between ACLs and firewalls depends on network size, security requirements, and traffic complexity, with many enterprises combining both for layered security.
Access Control List (ACL) vs Firewall Infographic
 techiny.com
techiny.com