The DMZ (Demilitarized Zone) in networking provides an isolated perimeter network segment that hosts public-facing services, offering controlled access from untrusted external networks while protecting the internal network. The internal network remains secure and strictly restricted to trusted devices and users, ensuring sensitive data and systems are safeguarded from external threats. Separating the DMZ from the internal network with firewalls and access controls enables organizations to minimize attack surfaces and enforce security policies effectively.
Table of Comparison
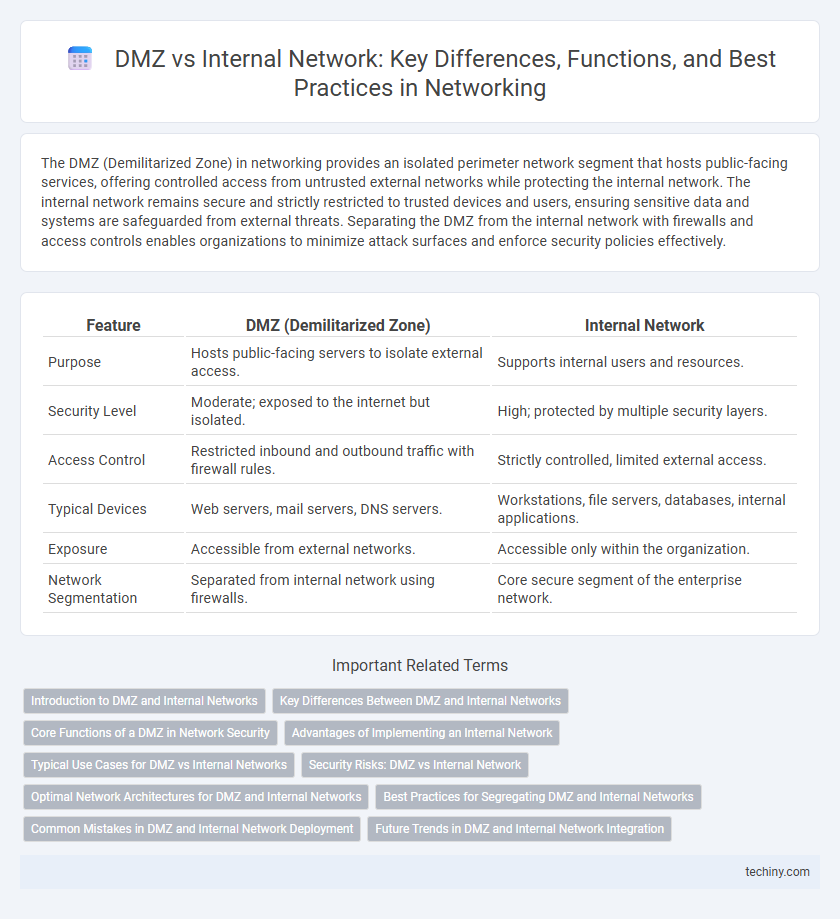
| Feature | DMZ (Demilitarized Zone) | Internal Network |
|---|---|---|
| Purpose | Hosts public-facing servers to isolate external access. | Supports internal users and resources. |
| Security Level | Moderate; exposed to the internet but isolated. | High; protected by multiple security layers. |
| Access Control | Restricted inbound and outbound traffic with firewall rules. | Strictly controlled, limited external access. |
| Typical Devices | Web servers, mail servers, DNS servers. | Workstations, file servers, databases, internal applications. |
| Exposure | Accessible from external networks. | Accessible only within the organization. |
| Network Segmentation | Separated from internal network using firewalls. | Core secure segment of the enterprise network. |
Introduction to DMZ and Internal Networks
A DMZ (Demilitarized Zone) is a specialized network segment that isolates external-facing services from the internal network, enhancing security by limiting access to sensitive data. Internal networks consist of protected resources and devices that are only accessible by authorized users within an organization, minimizing exposure to external threats. Implementing a DMZ creates a controlled buffer zone, reducing the risk of cyberattacks spreading from public-facing servers to critical internal systems.
Key Differences Between DMZ and Internal Networks
A DMZ (Demilitarized Zone) is a separate network segment designed to expose external-facing services to the internet while isolating them from the internal network for enhanced security. Internal networks house sensitive data and critical systems, enforcing stricter access controls and allowing trusted internal communications. Key differences include the DMZ's role in mitigating external attacks by acting as a buffer zone, whereas the internal network prioritizes confidentiality and integrity of internal resources.
Core Functions of a DMZ in Network Security
A DMZ (Demilitarized Zone) serves as a buffer zone between the internal network and external untrusted networks, such as the internet, providing controlled access to public-facing services like web servers and email servers. It isolates critical internal resources, reducing exposure to cyber threats by limiting direct access from outside networks and containing potential breaches within the DMZ segment. Core functions of a DMZ include traffic filtering through firewalls, preventing unauthorized access to the internal network, and enabling secure external connectivity with minimal risk to sensitive data.
Advantages of Implementing an Internal Network
Implementing an internal network enhances security by isolating sensitive data and critical systems from external threats common in DMZ environments. It enables granular access control and monitoring, reducing the risk of unauthorized access and lateral movement within the organization. Internal networks also improve performance and reliability by minimizing exposure to public network traffic and potential attacks.
Typical Use Cases for DMZ vs Internal Networks
DMZs typically host public-facing services such as web servers, mail servers, and DNS servers to provide controlled access from external networks while isolating the internal network from potential threats. Internal networks house sensitive resources like databases, application servers, and employee workstations, emphasizing strict access controls and data protection. Organizations deploy DMZs to enhance security by segregating external traffic from critical internal systems, minimizing the risk of lateral movement in case of a breach.
Security Risks: DMZ vs Internal Network
DMZ networks expose public-facing services to external threats, increasing the risk of attacks such as DDoS, intrusion attempts, and malware infections, whereas internal networks are shielded by firewalls and designed for secure internal communication. Compromises in the DMZ can serve as a launchpad for lateral movement into the internal network, potentially leading to data breaches and unauthorized access. Implementing strict access control lists, segmentation, and continuous monitoring are critical to minimizing security risks between the DMZ and internal network environments.
Optimal Network Architectures for DMZ and Internal Networks
An optimal network architecture for a DMZ involves isolating publicly accessible servers in a separate subnet, protected by firewalls to limit access from both external and internal networks. Internal networks should be segmented using VLANs and layered security controls to safeguard sensitive data and restrict lateral movement. Employing intrusion detection systems and strict access control policies enhances the security posture across both DMZ and internal network zones.
Best Practices for Segregating DMZ and Internal Networks
Segregating the DMZ from internal networks involves implementing strict firewall rules that limit traffic to only necessary protocols and ports, ensuring minimal exposure of internal resources. Network segmentation best practices include deploying dedicated hardware or virtualized environments for the DMZ, coupled with monitoring tools that detect anomalies or unauthorized access attempts. Utilizing access control lists (ACLs) and intrusion detection systems (IDS) further fortifies the boundary, maintaining a secure separation between public-facing services and sensitive internal assets.
Common Mistakes in DMZ and Internal Network Deployment
Common mistakes in DMZ and internal network deployment include improper segmentation that allows unauthorized access between zones, weak firewall rules that fail to restrict traffic effectively, and insufficient monitoring of traffic flows within the DMZ. Network architects often neglect to update security policies regularly, leaving legacy configurations vulnerable to exploitation. Misconfigurations such as exposing internal servers directly to the DMZ or using default credentials increase the risk of lateral movement by attackers.
Future Trends in DMZ and Internal Network Integration
Future trends in DMZ and internal network integration emphasize enhanced zero-trust architectures, where micro-segmentation isolates resources to minimize attack surfaces. Advances in AI-driven threat detection enable real-time monitoring and automated response within DMZs, improving security without compromising internal network performance. Cloud-native technologies further unify DMZ and internal network infrastructures, promoting seamless, scalable, and secure hybrid environments.
DMZ vs Internal Network Infographic
 techiny.com
techiny.com