GRE tunnels provide a simple, stateless method for encapsulating a wide variety of network layer protocols inside IP tunnels, making them ideal for routing protocol traffic and supporting multicast or broadcast packets. IPsec tunnels offer robust encryption and authentication, ensuring data confidentiality and integrity over unsecured networks, but they introduce additional overhead and complexity. While GRE tunnels excel in protocol flexibility and simplicity, IPsec tunnels prioritize security, often leading to the use of GRE over IPsec for encrypted routing solutions.
Table of Comparison
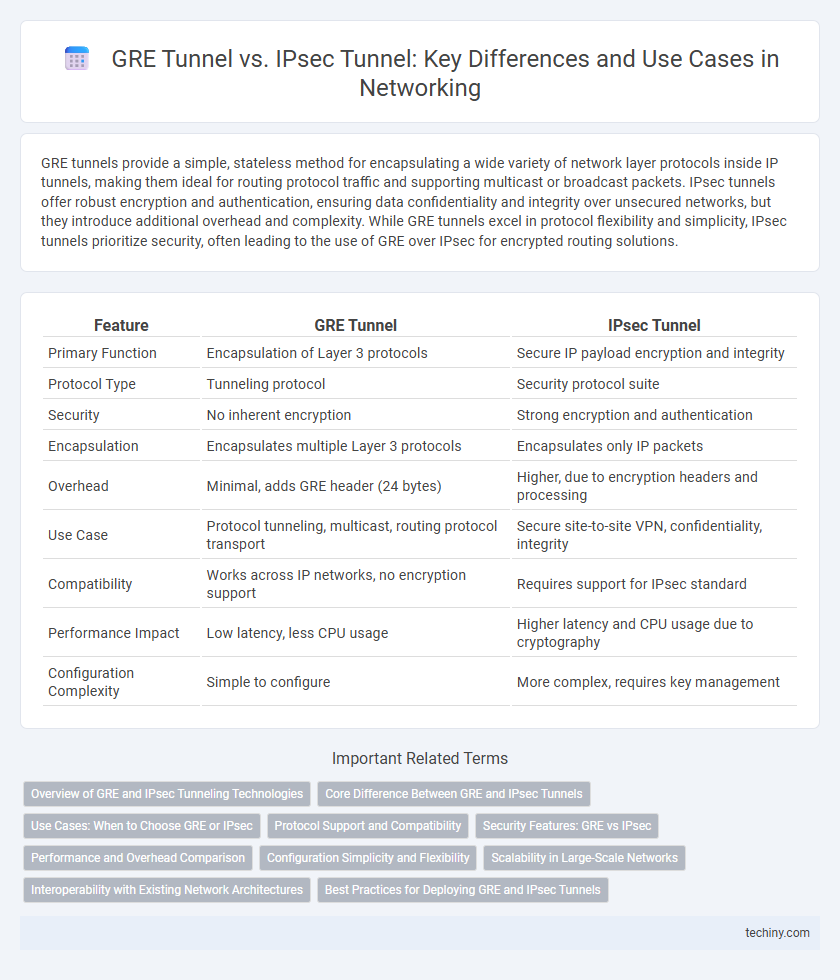
| Feature | GRE Tunnel | IPsec Tunnel |
|---|---|---|
| Primary Function | Encapsulation of Layer 3 protocols | Secure IP payload encryption and integrity |
| Protocol Type | Tunneling protocol | Security protocol suite |
| Security | No inherent encryption | Strong encryption and authentication |
| Encapsulation | Encapsulates multiple Layer 3 protocols | Encapsulates only IP packets |
| Overhead | Minimal, adds GRE header (24 bytes) | Higher, due to encryption headers and processing |
| Use Case | Protocol tunneling, multicast, routing protocol transport | Secure site-to-site VPN, confidentiality, integrity |
| Compatibility | Works across IP networks, no encryption support | Requires support for IPsec standard |
| Performance Impact | Low latency, less CPU usage | Higher latency and CPU usage due to cryptography |
| Configuration Complexity | Simple to configure | More complex, requires key management |
Overview of GRE and IPsec Tunneling Technologies
GRE (Generic Routing Encapsulation) tunneling provides a simple, protocol-independent method for encapsulating a wide variety of network layer protocols inside IP tunnels, facilitating routing protocols and multicast traffic through VPNs. IPsec (Internet Protocol Security) tunneling, in contrast, focuses on encrypting and authenticating IP packets to ensure confidentiality, integrity, and secure communication over public networks. While GRE tunnels encapsulate packets without encryption, IPsec adds robust security features, making it suitable for secure remote access and site-to-site VPNs.
Core Difference Between GRE and IPsec Tunnels
GRE tunnels encapsulate a wide variety of network layer protocols inside virtual point-to-point links, enabling the transport of multicast and broadcast traffic over an IP network, while IPsec tunnels prioritize security by encrypting data for secure communication between endpoints. GRE lacks built-in encryption, making it suitable for scenarios requiring protocol flexibility but not confidentiality, whereas IPsec provides robust encryption and authentication but is limited to IP traffic. The core difference lies in GRE focusing on protocol encapsulation and transport versatility, contrasted with IPsec's focus on securing IP traffic through encryption and integrity checks.
Use Cases: When to Choose GRE or IPsec
GRE tunnels are ideal for scenarios requiring the encapsulation of multicast traffic, routing protocols, or running non-IP protocols over an IP network, commonly used in site-to-site VPNs or connecting disparate networks. IPsec tunnels provide robust encryption and authentication, making them suitable for securing sensitive data in public or untrusted networks, especially in remote access VPNs and secure communications between data centers. Choosing GRE is optimal for flexibility and protocol support, while IPsec is preferred for confidentiality and integrity in network security.
Protocol Support and Compatibility
GRE tunnels support a wide range of protocols, including multicast and non-IP protocols, enabling versatile compatibility for various networking environments. IPsec tunnels primarily secure IP traffic with robust encryption but do not natively support non-IP protocols or multicast traffic. Combining GRE with IPsec enhances protocol support and security, allowing the encapsulation of diverse protocols within an encrypted IPsec tunnel.
Security Features: GRE vs IPsec
GRE tunnels provide simple encapsulation of packets without any built-in encryption or authentication, making them vulnerable to interception and attacks. IPsec tunnels offer robust security features including encryption, integrity checks, and authentication, ensuring confidentiality and data integrity over untrusted networks. Enterprises prioritize IPsec tunnels for secure VPN connections, while GRE tunnels are often combined with IPsec to achieve both routing flexibility and strong security.
Performance and Overhead Comparison
GRE tunnels introduce minimal overhead by encapsulating packets with a simple header, resulting in lower latency and better throughput compared to IPsec tunnels, which require extensive encryption and decryption processes that increase CPU load and packet size. IPsec provides robust security features such as authentication and encryption, but this added security results in higher overhead and reduced network performance. In scenarios prioritizing speed and efficiency, GRE tunnels outperform IPsec, while IPsec is preferred for secure communications despite its performance cost.
Configuration Simplicity and Flexibility
GRE tunnels offer straightforward configuration with minimal overhead, enabling easy encapsulation of various protocols and multicast traffic. IPsec tunnels require more complex setup due to encryption key management and security policies but provide enhanced data protection. GRE allows flexible routing and protocol support, whereas IPsec prioritizes secure communication at the cost of increased configuration complexity.
Scalability in Large-Scale Networks
GRE tunnels offer flexibility by supporting multicast and non-IP protocols, making them suitable for scalable, complex network architectures in large-scale environments. IPsec tunnels provide robust security with encryption but may face scalability limitations due to increased overhead and processing demands on network devices. Combining GRE with IPsec can optimize large-scale network scalability by enabling secure tunneling alongside versatile protocol support and efficient routing.
Interoperability with Existing Network Architectures
GRE tunnels provide flexible interoperability with various network protocols by encapsulating multiple Layer 3 protocols over IP networks, making them ideal for integrating legacy systems within existing network architectures. IPsec tunnels offer secure encrypted communication and are widely supported across different vendors, ensuring seamless compatibility with standard VPN infrastructures and facilitating secure connectivity in heterogeneous environments. Combining GRE with IPsec can enhance interoperability by enabling multiprotocol transport over secure channels without sacrificing compatibility or security.
Best Practices for Deploying GRE and IPsec Tunnels
When deploying GRE tunnels, configure keepalive timers and ensure proper routing protocols for dynamic path selection to maintain tunnel stability and performance. For IPsec tunnels, prioritize strong encryption algorithms, integrity checks, and key management practices such as IKEv2 with robust authentication methods to secure data confidentiality and integrity. Combining GRE with IPsec offers best practice by encapsulating multicast traffic and routing protocols inside GRE while securing the tunnel with IPsec encryption for comprehensive network security and flexibility.
GRE Tunnel vs IPsec Tunnel Infographic
 techiny.com
techiny.com