A DMZ (Demilitarized Zone) is a network segment that isolates external-facing services from the internal LAN (Local Area Network), enhancing security by limiting access to critical resources. Unlike the LAN, which connects trusted devices within a private network, the DMZ hosts servers like web, mail, and DNS that require exposure to the internet while protecting the internal network from potential threats. Properly configuring the DMZ and LAN reduces vulnerability to cyberattacks, ensuring sensitive pet networking data remains secure.
Table of Comparison
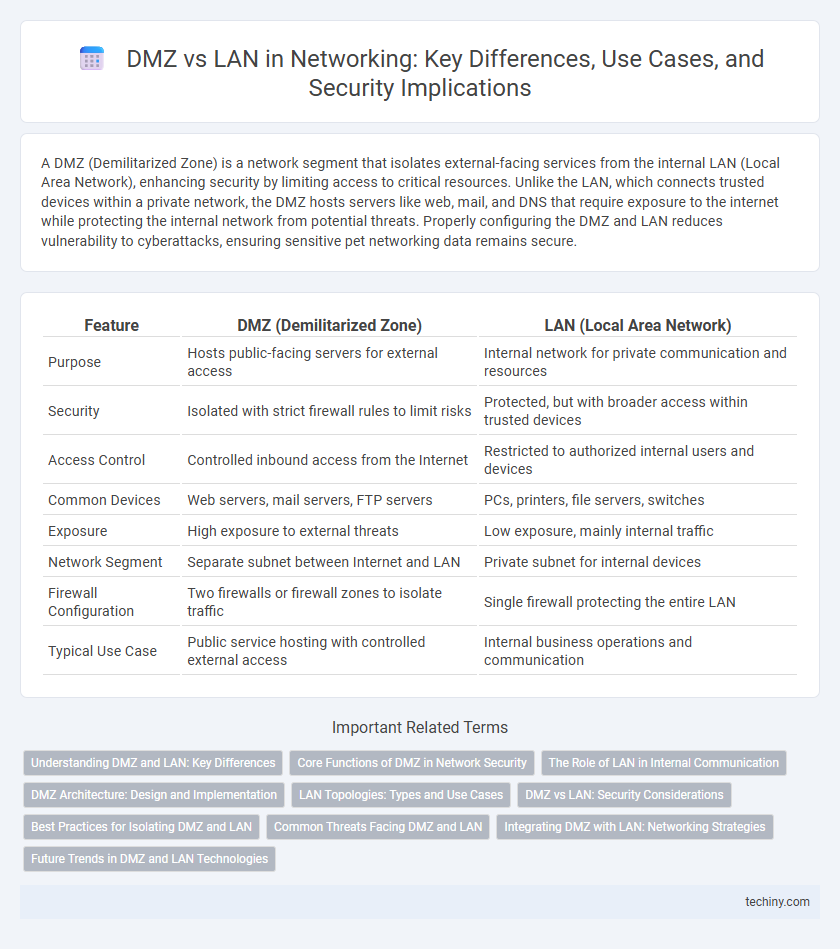
| Feature | DMZ (Demilitarized Zone) | LAN (Local Area Network) |
|---|---|---|
| Purpose | Hosts public-facing servers for external access | Internal network for private communication and resources |
| Security | Isolated with strict firewall rules to limit risks | Protected, but with broader access within trusted devices |
| Access Control | Controlled inbound access from the Internet | Restricted to authorized internal users and devices |
| Common Devices | Web servers, mail servers, FTP servers | PCs, printers, file servers, switches |
| Exposure | High exposure to external threats | Low exposure, mainly internal traffic |
| Network Segment | Separate subnet between Internet and LAN | Private subnet for internal devices |
| Firewall Configuration | Two firewalls or firewall zones to isolate traffic | Single firewall protecting the entire LAN |
| Typical Use Case | Public service hosting with controlled external access | Internal business operations and communication |
Understanding DMZ and LAN: Key Differences
A DMZ (Demilitarized Zone) in networking is a separate subnetwork that exposes external-facing services to the internet while isolating them from the internal LAN (Local Area Network) to enhance security. The LAN is a private, secure network where internal devices communicate freely, protected from external threats by firewalls and network policies. Understanding the key difference lies in their roles: the DMZ serves as a buffer zone for public access, whereas the LAN maintains the protected internal network environment.
Core Functions of DMZ in Network Security
The core functions of a DMZ in network security include isolating public-facing services from the internal LAN to prevent direct access to sensitive systems, thereby minimizing the attack surface. It enables controlled access to external users while maintaining strict firewall rules and monitoring to detect and mitigate threats. This segmentation ensures enhanced protection of internal networks by confining potential breaches within the DMZ environment.
The Role of LAN in Internal Communication
LAN (Local Area Network) serves as the backbone of internal communication within an organization, enabling direct data exchange among devices such as computers, printers, and servers. It ensures high-speed, secure connectivity for users inside the corporate perimeter, facilitating efficient resource sharing and collaboration. Unlike the DMZ, which isolates external-facing services, the LAN maintains protected internal traffic, supporting critical business operations and sensitive information flow.
DMZ Architecture: Design and Implementation
DMZ architecture in networking involves creating a buffer zone between an internal LAN and external networks, enhancing security by isolating public-facing services such as web and mail servers from the core internal network. The design typically includes multiple firewalls or a dual firewall setup to control and monitor traffic flow between the DMZ, LAN, and the internet, minimizing exposure to external threats while maintaining controlled access. Effective implementation requires detailed segmentation, strict access control policies, and continuous monitoring to protect sensitive LAN resources and ensure robust defense-in-depth strategies.
LAN Topologies: Types and Use Cases
LAN topologies such as star, ring, bus, and mesh define the physical or logical arrangement of devices in a Local Area Network, each impacting performance and fault tolerance differently. Star topology is widely used in corporate environments due to its simplicity and centralized management, while mesh topology offers high redundancy and reliability, ideal for critical systems requiring uninterrupted connectivity. Understanding these topologies helps network administrators optimize data flow and security within a LAN, contrasting with DMZ setups that isolate public-facing services from internal networks.
DMZ vs LAN: Security Considerations
DMZ (Demilitarized Zone) networks enhance security by isolating public-facing services from the internal LAN, reducing the risk of direct attacks on sensitive resources. Unlike LAN, which hosts trusted devices within an organization, the DMZ acts as a buffer zone, containing firewalls and intrusion prevention systems to monitor and control traffic flow. Segmentation between DMZ and LAN ensures that even if the DMZ is compromised, internal network integrity and confidential data remain protected.
Best Practices for Isolating DMZ and LAN
Isolating the DMZ from the LAN involves implementing strict firewall rules that restrict traffic flow between the two zones, minimizing exposure of internal resources. Best practices recommend using separate network segments with unique IP ranges and VLANs to compartmentalize network functions effectively. Employing intrusion detection systems (IDS) and regularly updating access controls further strengthens the security posture of both the DMZ and LAN environments.
Common Threats Facing DMZ and LAN
Common threats facing DMZs include external attacks such as Distributed Denial of Service (DDoS), intrusion attempts, and malware infiltration due to their exposure to the internet. LANs, while more protected by internal firewalls, face risks from insider threats, lateral movement of attackers, and ransomware spreading through compromised endpoints. Both environments require robust security measures like segmented firewalls, intrusion detection systems, and continuous monitoring to mitigate these risks effectively.
Integrating DMZ with LAN: Networking Strategies
Integrating a DMZ with a LAN involves using firewalls and access control lists to create a secure boundary that allows controlled communication between internal networks and public-facing services. Network segmentation techniques, such as VLANs and subnetting, optimize traffic management and limit the attack surface by isolating sensitive LAN resources from the potentially vulnerable DMZ. Implementing intrusion detection systems (IDS) and strict routing policies further enhances security while maintaining efficient data flow between the DMZ and LAN.
Future Trends in DMZ and LAN Technologies
Future trends in DMZ and LAN technologies emphasize enhanced security through micro-segmentation and zero-trust architectures, minimizing attack surfaces and lateral movement risks. Integration of AI-driven traffic analysis and automated threat detection in DMZ zones improves real-time response capabilities, while LANs evolve with increased adoption of Wi-Fi 6E and 5G for higher bandwidth and lower latency. Edge computing convergence with LAN and DMZ frameworks supports scalable, distributed network environments catering to IoT and cloud-native applications.
DMZ vs LAN Infographic
 techiny.com
techiny.com