Packet filtering examines data packets at the network layer to allow or block traffic based on IP addresses, ports, and protocols, offering fast and efficient filtering but limited in content inspection. Proxy filtering operates at the application layer, intercepting user requests to analyze and control content more thoroughly, enhancing security by hiding client IPs and blocking harmful content. While packet filtering is suitable for basic access control, proxy filtering provides deeper inspection and improved threat prevention for complex network environments.
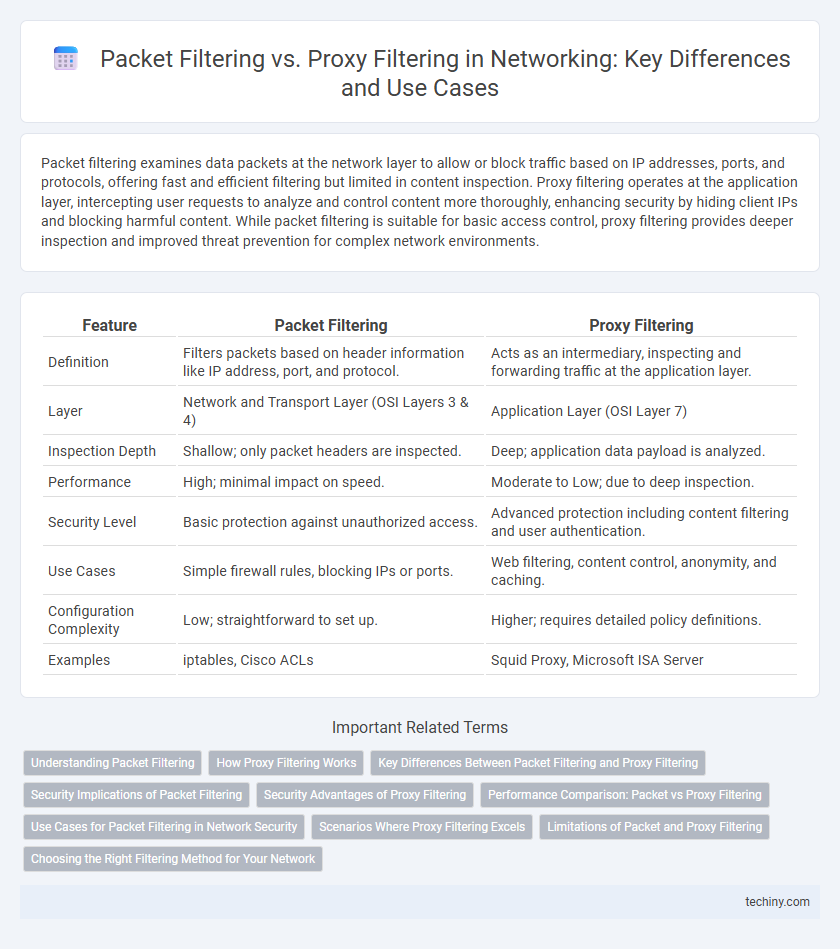
Table of Comparison
| Feature | Packet Filtering | Proxy Filtering |
|---|---|---|
| Definition | Filters packets based on header information like IP address, port, and protocol. | Acts as an intermediary, inspecting and forwarding traffic at the application layer. |
| Layer | Network and Transport Layer (OSI Layers 3 & 4) | Application Layer (OSI Layer 7) |
| Inspection Depth | Shallow; only packet headers are inspected. | Deep; application data payload is analyzed. |
| Performance | High; minimal impact on speed. | Moderate to Low; due to deep inspection. |
| Security Level | Basic protection against unauthorized access. | Advanced protection including content filtering and user authentication. |
| Use Cases | Simple firewall rules, blocking IPs or ports. | Web filtering, content control, anonymity, and caching. |
| Configuration Complexity | Low; straightforward to set up. | Higher; requires detailed policy definitions. |
| Examples | iptables, Cisco ACLs | Squid Proxy, Microsoft ISA Server |
Understanding Packet Filtering
Packet filtering is a network security technique that examines each packet's header information, such as source IP address, destination IP address, protocol, and port number, to determine whether to allow or block it based on predefined rules. It operates at the network layer (Layer 3) and transport layer (Layer 4) of the OSI model, enabling fast and efficient filtering without inspecting packet content. Packet filtering provides a basic level of security by controlling traffic flow but lacks the ability to understand application-level data, which is where proxy filtering offers more granular control.
How Proxy Filtering Works
Proxy filtering functions by intercepting network requests and acting as an intermediary between the client and the destination server, examining the content of the packets before forwarding them. It operates at the application layer, enabling detailed inspection of data such as URLs, headers, and payloads to enforce security policies and block malicious or unwanted traffic. This method provides enhanced control over user access and data privacy compared to basic packet filtering, which only inspects headers at the network or transport layers.
Key Differences Between Packet Filtering and Proxy Filtering
Packet filtering operates at the network layer by inspecting packet headers such as IP addresses and port numbers to determine whether to allow or block traffic, offering faster processing but limited context awareness. Proxy filtering functions at the application layer, acting as an intermediary that evaluates entire data streams and content, thereby providing granular control and enhanced security through deep packet inspection. Packet filtering is suitable for high-speed traffic with basic filtering needs, while proxy filtering supports advanced policies including content filtering, user authentication, and protocol-specific controls.
Security Implications of Packet Filtering
Packet filtering operates at the network layer by inspecting IP headers and blocking or allowing packets based on predefined rules, offering minimal protection against sophisticated attacks such as IP spoofing or packet fragmentation. This approach lacks deep inspection capabilities, which means threats like application-layer attacks or malware embedded within allowed packets can bypass security measures. Consequently, relying solely on packet filtering may expose networks to vulnerabilities that require more advanced filtering techniques like proxy filtering for enhanced security.
Security Advantages of Proxy Filtering
Proxy filtering enhances security by acting as an intermediary between users and the internet, effectively masking internal IP addresses to prevent direct external attacks. Unlike packet filtering, proxy filtering inspects entire application-layer requests, enabling deep content analysis and blocking of malicious web traffic. This granular control reduces the risk of unauthorized access and prevents data leakage by enforcing strict security policies on inbound and outbound communications.
Performance Comparison: Packet vs Proxy Filtering
Packet filtering offers higher performance through direct inspection and decision-making on network packets without altering the data flow, resulting in lower latency and minimal resource consumption. Proxy filtering operates by intercepting and analyzing entire protocol sessions, which introduces additional processing overhead and potential bottlenecks, impacting throughput and response times. Network environments prioritizing speed and minimal delay benefit more from packet filtering, while proxy filtering provides enhanced security at the cost of reduced performance.
Use Cases for Packet Filtering in Network Security
Packet filtering is essential in network security for controlling data flow by examining packet headers and enforcing rules based on IP addresses, ports, and protocols. It is widely used in firewalls to block unauthorized access and prevent attacks like IP spoofing and Denial of Service (DoS). Packet filtering excels in scenarios requiring high-speed, low-latency filtering with minimal resource consumption, such as protecting edge routers and segmenting internal networks.
Scenarios Where Proxy Filtering Excels
Proxy filtering excels in scenarios requiring enhanced security and content control by acting as an intermediary between users and external networks, effectively masking internal IP addresses. It is ideal for enforcing granular access policies, supporting authentication, and inspecting encrypted traffic, which packet filtering alone cannot manage efficiently. Organizations leveraging proxy filtering benefit from improved threat detection, detailed logging, and content caching, optimizing both security and network performance.
Limitations of Packet and Proxy Filtering
Packet filtering faces limitations with inadequate inspection depth, as it only examines header information, making it vulnerable to IP spoofing and unable to detect application-layer attacks. Proxy filtering overcomes some of these issues by analyzing application-level data but suffers from latency and performance bottlenecks due to processing overhead. Both approaches struggle with encrypted traffic, where packet filtering lacks visibility and proxy filtering requires complex decryption mechanisms.
Choosing the Right Filtering Method for Your Network
Packet filtering offers low-latency performance by inspecting packet headers against predefined rules, making it ideal for high-speed networks requiring basic access control. Proxy filtering provides deeper security by intermediating client-server connections, enabling content inspection, user authentication, and granular control suited for sensitive or regulated environments. Evaluating network size, security requirements, and resource availability is essential when choosing between packet filtering and proxy filtering to optimize protection and performance.
Packet Filtering vs Proxy Filtering Infographic
 techiny.com
techiny.com