Trunk ports carry multiple VLANs simultaneously, allowing devices on different VLANs to communicate across switches. Access ports are assigned to a single VLAN and connect end devices like computers or printers directly to the network. Understanding the distinction between trunk and access ports is crucial for efficient VLAN management and network segmentation.
Table of Comparison
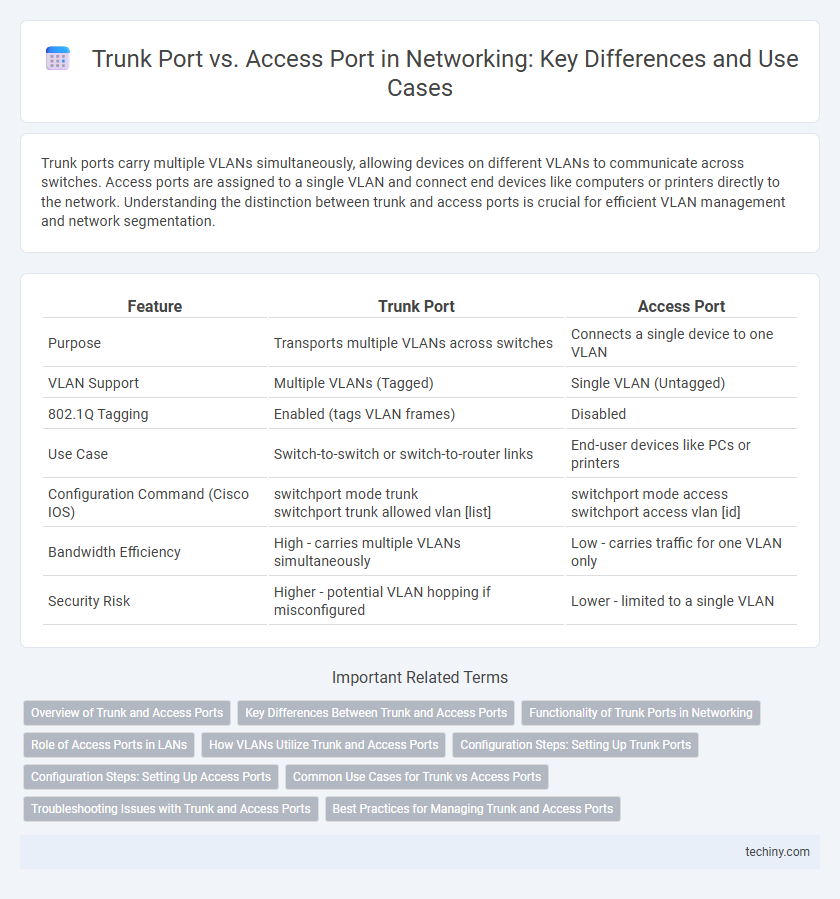
| Feature | Trunk Port | Access Port |
|---|---|---|
| Purpose | Transports multiple VLANs across switches | Connects a single device to one VLAN |
| VLAN Support | Multiple VLANs (Tagged) | Single VLAN (Untagged) |
| 802.1Q Tagging | Enabled (tags VLAN frames) | Disabled |
| Use Case | Switch-to-switch or switch-to-router links | End-user devices like PCs or printers |
| Configuration Command (Cisco IOS) |
switchport mode trunk switchport trunk allowed vlan [list] |
switchport mode access switchport access vlan [id] |
| Bandwidth Efficiency | High - carries multiple VLANs simultaneously | Low - carries traffic for one VLAN only |
| Security Risk | Higher - potential VLAN hopping if misconfigured | Lower - limited to a single VLAN |
Overview of Trunk and Access Ports
Trunk ports carry multiple VLANs simultaneously, enabling communication across different VLANs on switches by tagging Ethernet frames with VLAN IDs using protocols like IEEE 802.1Q. Access ports connect end devices to the network and carry traffic for a single VLAN without VLAN tagging, ensuring devices like computers and printers are assigned to specific VLANs. Trunk ports are essential for inter-switch links while access ports serve as the endpoint connection in a LAN environment.
Key Differences Between Trunk and Access Ports
Trunk ports carry multiple VLAN traffic simultaneously, tagging frames to identify VLAN membership, while access ports handle traffic for a single VLAN without tagging. Trunk ports are primarily used to connect switches and carry VLAN data across network segments, whereas access ports connect end devices like computers or printers to a specific VLAN. The key difference lies in VLAN handling: trunks enable inter-VLAN communication through tagged frames, and access ports restrict traffic to one untagged VLAN.
Functionality of Trunk Ports in Networking
Trunk ports in networking facilitate the transmission of multiple VLANs across a single physical link by tagging Ethernet frames with VLAN identifiers, enabling efficient inter-switch communication and VLAN management. They play a critical role in maintaining VLAN segregation and ensuring data traffic from different VLANs is correctly routed across switches in a network. This functionality optimizes network bandwidth and supports scalable, segmented network architectures essential for large enterprise environments.
Role of Access Ports in LANs
Access ports in LANs serve as the primary connection points for end devices, such as computers and printers, ensuring they are assigned to a specific VLAN. These ports carry traffic for a single VLAN, facilitating efficient and secure communication within that VLAN. By segregating network traffic, access ports help maintain network organization and reduce broadcast domains.
How VLANs Utilize Trunk and Access Ports
VLANs utilize access ports to carry traffic for a single VLAN, typically connecting end devices like PCs or printers, ensuring segregated broadcast domains within the network. Trunk ports, configured between switches, carry traffic for multiple VLANs simultaneously by tagging Ethernet frames with VLAN identifiers using protocols such as IEEE 802.1Q. This segmentation enables efficient VLAN traffic management and inter-VLAN communication through Layer 3 routing.
Configuration Steps: Setting Up Trunk Ports
Configure trunk ports by entering interface configuration mode using the command `interface
Configuration Steps: Setting Up Access Ports
To configure access ports, begin by entering interface configuration mode with the command `interface [interface-id]`, then set the port to access mode using `switchport mode access`. Assign the port to a specific VLAN by applying the `switchport access vlan [vlan-id]` command. Finally, verify the configuration with `show interfaces [interface-id] switchport` to ensure the port is correctly set as an access port for the designated VLAN.
Common Use Cases for Trunk vs Access Ports
Access ports are primarily used to connect end devices such as computers, printers, and IP phones to the network, carrying traffic for a single VLAN. Trunk ports are designed to carry multiple VLANs' traffic between switches or between switches and routers, enabling VLAN tagging through protocols like IEEE 802.1Q. In enterprise networks, access ports facilitate device-level connections, while trunk ports support inter-switch communication and VLAN segmentation across the infrastructure.
Troubleshooting Issues with Trunk and Access Ports
Troubleshooting trunk ports often involves verifying VLAN tagging configurations and ensuring compatible encapsulation protocols like IEEE 802.1Q are enabled on both ends to prevent VLAN mismatches. Access port issues commonly stem from incorrect VLAN assignments or port security violations, which can be resolved by confirming proper VLAN membership and resetting port security settings. Monitoring switch logs and using commands like "show interfaces trunk" and "show vlan" assist in identifying port status and traffic flow anomalies.
Best Practices for Managing Trunk and Access Ports
Best practices for managing trunk and access ports emphasize configuring access ports with appropriate VLAN assignments to ensure secure and efficient traffic segmentation. Trunk ports should be explicitly configured with allowed VLANs and use native VLANs cautiously to prevent VLAN hopping attacks. Regular monitoring and applying port security measures help maintain network integrity and minimize unauthorized access on both trunk and access ports.
Trunk vs Access Port Infographic
 techiny.com
techiny.com