Quantum Key Distribution (QKD) leverages the principles of quantum mechanics to enable secure communication by detecting any eavesdropping attempts, thus providing theoretically unbreakable encryption keys. In contrast, Classical Key Distribution relies on computational hardness assumptions, making its security vulnerable to advances in algorithms and computing power, especially from emerging quantum computers. QKD ensures future-proof security by using quantum entanglement and photon polarization, whereas classical methods depend on mathematical complexity that could be compromised.
Table of Comparison
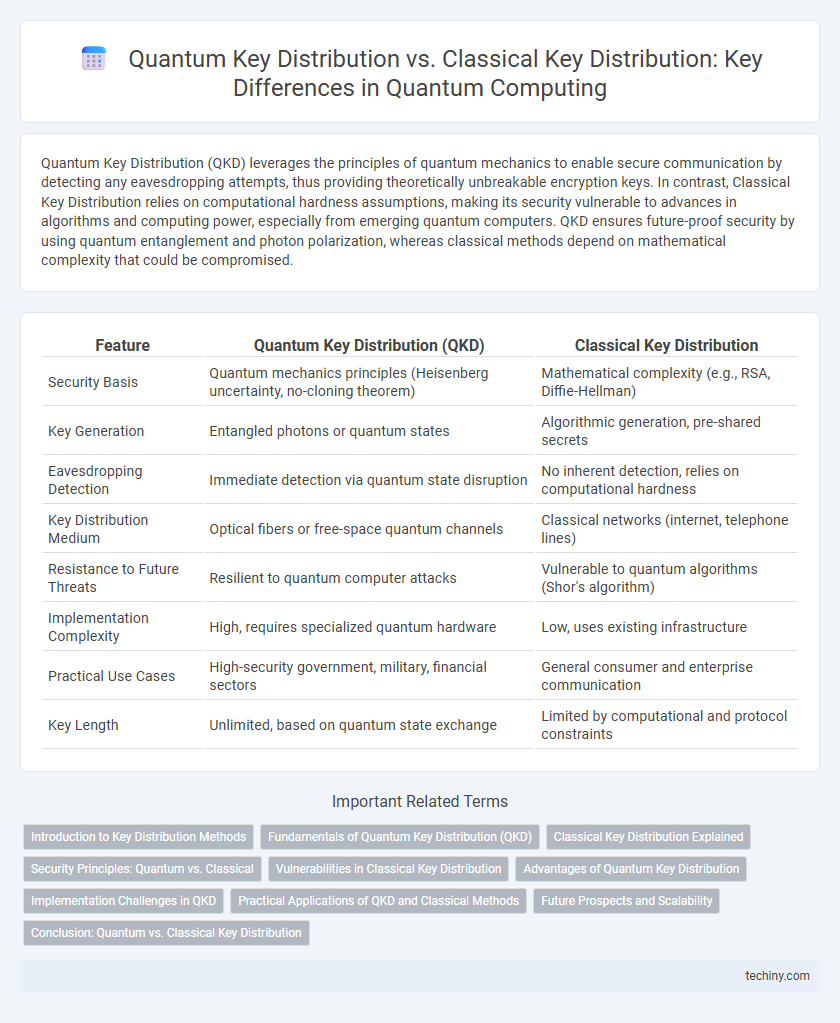
| Feature | Quantum Key Distribution (QKD) | Classical Key Distribution |
|---|---|---|
| Security Basis | Quantum mechanics principles (Heisenberg uncertainty, no-cloning theorem) | Mathematical complexity (e.g., RSA, Diffie-Hellman) |
| Key Generation | Entangled photons or quantum states | Algorithmic generation, pre-shared secrets |
| Eavesdropping Detection | Immediate detection via quantum state disruption | No inherent detection, relies on computational hardness |
| Key Distribution Medium | Optical fibers or free-space quantum channels | Classical networks (internet, telephone lines) |
| Resistance to Future Threats | Resilient to quantum computer attacks | Vulnerable to quantum algorithms (Shor's algorithm) |
| Implementation Complexity | High, requires specialized quantum hardware | Low, uses existing infrastructure |
| Practical Use Cases | High-security government, military, financial sectors | General consumer and enterprise communication |
| Key Length | Unlimited, based on quantum state exchange | Limited by computational and protocol constraints |
Introduction to Key Distribution Methods
Quantum Key Distribution (QKD) leverages quantum mechanics principles such as superposition and entanglement to enable secure communication by detecting eavesdropping attempts, unlike classical key distribution that relies on computational hardness assumptions vulnerable to advances in algorithms and computing power. Classical methods, including symmetric key exchange via pre-shared keys and asymmetric cryptography like RSA and Diffie-Hellman, depend on mathematical problems whose complexity can be compromised over time. QKD protocols like BB84 and E91 provide theoretically unbreakable encryption by using quantum states to generate and share cryptographic keys securely.
Fundamentals of Quantum Key Distribution (QKD)
Quantum Key Distribution (QKD) leverages the principles of quantum mechanics, such as superposition and entanglement, to enable secure communication by detecting eavesdropping through quantum state disturbances. Unlike classical key distribution, which relies on computational hardness assumptions, QKD guarantees unconditional security based on the laws of physics, ensuring that any interception attempt alters the quantum states and is immediately detectable. The BB84 protocol, one of the foundational QKD methods, encodes key bits into non-orthogonal quantum states transmitted between parties, enabling the establishment of secret keys with provable security against any computational attack.
Classical Key Distribution Explained
Classical key distribution relies on mathematical algorithms and computational complexity to secure encryption keys, typically using public-key cryptography methods such as RSA or Diffie-Hellman. These techniques depend on the difficulty of factoring large integers or computing discrete logarithms, which can be vulnerable to advances in computational power and algorithmic breakthroughs. Classical key distribution requires trusted channels and can be susceptible to interception or man-in-the-middle attacks without additional safeguards like digital signatures or certificates.
Security Principles: Quantum vs. Classical
Quantum Key Distribution (QKD) leverages the principles of quantum mechanics, such as superposition and entanglement, to enable theoretically unbreakable encryption by detecting any eavesdropping attempts through quantum state alterations. Classical key distribution relies on computational complexity and mathematical algorithms, making it vulnerable to future advances in computing power, such as quantum attacks. The security strength of QKD fundamentally stems from the laws of physics, whereas classical methods depend on the presumed difficulty of solving specific mathematical problems.
Vulnerabilities in Classical Key Distribution
Classical key distribution relies on mathematical algorithms vulnerable to computational advances, especially from quantum computers capable of breaking widely used cryptographic protocols like RSA and ECC. These methods are susceptible to interception and decryption if an attacker gains sufficient computing power or exploits weaknesses in key exchange schemes such as Diffie-Hellman. In contrast, Quantum Key Distribution leverages quantum mechanics principles to detect eavesdropping and ensure unconditional security, addressing the fundamental vulnerabilities present in classical key distribution systems.
Advantages of Quantum Key Distribution
Quantum Key Distribution (QKD) offers unparalleled security by leveraging the principles of quantum mechanics, such as quantum entanglement and superposition, to detect any eavesdropping attempts instantly. Unlike Classical Key Distribution methods, which rely on mathematical complexity vulnerable to advances in computational power, QKD ensures unconditional security based on the laws of physics. This makes QKD particularly advantageous for securing sensitive information against future quantum computing attacks.
Implementation Challenges in QKD
Quantum Key Distribution (QKD) faces significant implementation challenges compared to classical key distribution methods due to its reliance on quantum properties such as superposition and entanglement, which require highly sensitive and error-prone hardware like single-photon sources and detectors. Maintaining quantum coherence over long distances is difficult because of photon loss and environmental noise, limiting the operational range of QKD systems and necessitating complex error correction protocols. Furthermore, integrating QKD into existing communication infrastructures requires overcoming compatibility issues between quantum and classical networks, as well as addressing scalability and cost concerns inherent to quantum technologies.
Practical Applications of QKD and Classical Methods
Quantum Key Distribution (QKD) enables secure communication by leveraging quantum mechanics properties, offering theoretically unbreakable encryption resistant to quantum computer attacks, unlike classical key distribution methods that rely on mathematical complexity and are vulnerable to evolving computational power. Practical applications of QKD are emerging in highly sensitive sectors such as government communications, financial transactions, and critical infrastructure protection, where enhanced security is paramount. Classical key distribution remains widely used in everyday internet security and enterprise networks due to its compatibility and cost-effectiveness despite its susceptibility to quantum threats.
Future Prospects and Scalability
Quantum Key Distribution (QKD) offers unparalleled security based on quantum mechanics principles, ensuring future-proof cryptographic communication resistant to quantum attacks. Scalability challenges persist in QKD networks due to photon loss and the need for quantum repeaters, but advancements in satellite-based QKD and integrated photonics aim to extend practical deployment beyond metropolitan areas. Classical key distribution methods benefit from established infrastructure and ease of scalability but lack the inherent security guarantees against evolving quantum threats, highlighting QKD's critical role in next-generation secure communication systems.
Conclusion: Quantum vs. Classical Key Distribution
Quantum Key Distribution (QKD) offers unparalleled security by leveraging the principles of quantum mechanics, making eavesdropping theoretically detectable and preventing key interception, unlike classical key distribution methods that rely on computational complexity and remain vulnerable to advances in computing power. Classical key distribution, while currently widespread and practical, faces increasing risks from quantum computing capabilities that can break traditional encryption algorithms. The adoption of QKD represents a critical advancement in secure communication, ensuring future-proof protection against both present and emerging cyber threats.
Quantum Key Distribution vs Classical Key Distribution Infographic
 techiny.com
techiny.com