Quantum Key Distribution (QKD) leverages the principles of quantum mechanics to enable secure communication by generating shared secret keys that are immune to eavesdropping. Unlike traditional public-key encryption, which relies on mathematical complexity and is vulnerable to future quantum attacks, QKD offers provable security based on quantum physics. The integration of QKD enhances cryptographic protocols by ensuring confidentiality even against adversaries equipped with quantum computers.
Table of Comparison
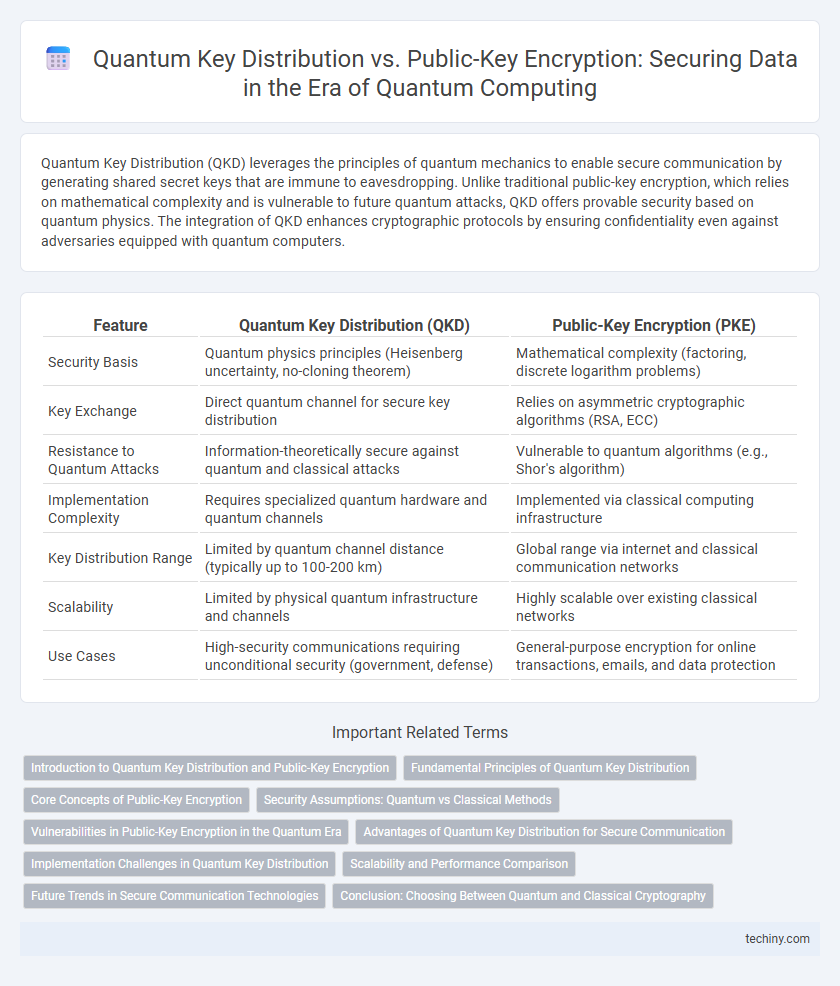
| Feature | Quantum Key Distribution (QKD) | Public-Key Encryption (PKE) |
|---|---|---|
| Security Basis | Quantum physics principles (Heisenberg uncertainty, no-cloning theorem) | Mathematical complexity (factoring, discrete logarithm problems) |
| Key Exchange | Direct quantum channel for secure key distribution | Relies on asymmetric cryptographic algorithms (RSA, ECC) |
| Resistance to Quantum Attacks | Information-theoretically secure against quantum and classical attacks | Vulnerable to quantum algorithms (e.g., Shor's algorithm) |
| Implementation Complexity | Requires specialized quantum hardware and quantum channels | Implemented via classical computing infrastructure |
| Key Distribution Range | Limited by quantum channel distance (typically up to 100-200 km) | Global range via internet and classical communication networks |
| Scalability | Limited by physical quantum infrastructure and channels | Highly scalable over existing classical networks |
| Use Cases | High-security communications requiring unconditional security (government, defense) | General-purpose encryption for online transactions, emails, and data protection |
Introduction to Quantum Key Distribution and Public-Key Encryption
Quantum Key Distribution (QKD) utilizes the principles of quantum mechanics to securely share encryption keys, ensuring unconditional security through phenomena like quantum entanglement and no-cloning theorem. Public-Key Encryption relies on mathematical algorithms such as RSA or ECC to generate paired keys for encryption and decryption, with security based on computational hardness assumptions. While QKD offers provably secure key exchange immune to future quantum attacks, Public-Key Encryption remains widely deployed due to established infrastructure despite vulnerabilities to quantum computing advancements.
Fundamental Principles of Quantum Key Distribution
Quantum Key Distribution (QKD) leverages the principles of quantum mechanics, such as superposition and entanglement, to enable secure communication by detecting eavesdropping through quantum state disturbances. Unlike Public-Key Encryption, which relies on computational hardness assumptions, QKD ensures unconditional security guaranteed by the laws of physics, making it resilient against attacks by quantum computers. Fundamental mechanisms like the no-cloning theorem and measurement-induced state collapse underpin QKD protocols such as BB84, establishing a secure shared secret key between parties without reliance on mathematical complexities.
Core Concepts of Public-Key Encryption
Public-key encryption relies on asymmetric cryptographic algorithms that use a pair of mathematically linked keys: a public key for encryption and a private key for decryption. This system enables secure communication over insecure channels by allowing anyone to encrypt messages with the recipient's public key, while only the holder of the private key can decrypt them. The security of public-key encryption is based on hard mathematical problems like integer factorization or discrete logarithms, which quantum computing threatens to solve efficiently.
Security Assumptions: Quantum vs Classical Methods
Quantum Key Distribution (QKD) leverages the principles of quantum mechanics, such as quantum entanglement and no-cloning theorem, to ensure unconditional security, making it resilient against any computational attack, including those by quantum computers. Public-key encryption relies on mathematical problems like integer factorization or discrete logarithms whose security depends on computational complexity assumptions vulnerable to quantum algorithms like Shor's algorithm. While classical public-key cryptosystems face potential decryption threats from scalable quantum computers, QKD guarantees key secrecy based on the fundamental laws of physics rather than relying on unproven computational assumptions.
Vulnerabilities in Public-Key Encryption in the Quantum Era
Quantum Key Distribution (QKD) offers provable security based on the principles of quantum mechanics, effectively eliminating vulnerabilities posed by quantum computers that threaten public-key encryption algorithms like RSA and ECC. Public-key encryption relies on mathematical problems such as integer factorization and discrete logarithms, which quantum algorithms like Shor's algorithm can solve exponentially faster, rendering traditional cryptographic schemes insecure. While public-key encryption faces significant risks in the quantum era, QKD provides a robust alternative by enabling secure key exchange immune to computational attacks from quantum adversaries.
Advantages of Quantum Key Distribution for Secure Communication
Quantum Key Distribution (QKD) offers unparalleled security by leveraging the principles of quantum mechanics, enabling the detection of any eavesdropping during key exchange. Unlike traditional Public-Key Encryption, which relies on computational hardness assumptions vulnerable to advances in quantum algorithms, QKD provides unconditional security through physics-based protocols such as BB84. This ensures secure communication even against future threats posed by quantum computers, making QKD a robust solution for protecting sensitive data.
Implementation Challenges in Quantum Key Distribution
Quantum Key Distribution (QKD) faces significant implementation challenges such as the need for specialized quantum hardware and sensitivity to environmental noise, which limits its scalability and widespread adoption. Maintaining quantum coherence over long distances requires advanced error correction and quantum repeaters, technologies still in early development stages. In contrast, public-key encryption relies on classical infrastructure, offering easier deployment but is vulnerable to future quantum attacks.
Scalability and Performance Comparison
Quantum Key Distribution (QKD) offers unparalleled security based on quantum mechanics but faces significant scalability challenges due to the need for specialized quantum channels and limited transmission distances. Public-key encryption, leveraging classical computational frameworks, provides high scalability and fast performance across global networks, though it remains vulnerable to advances in quantum computing attacks. Current research aims to enhance QKD's practicality, focusing on integrating quantum repeaters and hybrid protocols to improve its scalability and throughput for future secure communications.
Future Trends in Secure Communication Technologies
Quantum Key Distribution (QKD) leverages quantum mechanics to enable theoretically unbreakable encryption by detecting eavesdropping on key exchanges, contrasting with traditional public-key encryption that relies on computational complexity vulnerable to quantum attacks. Future trends highlight integrating QKD with classical networks to enhance security while addressing scalability and infrastructure challenges. Emerging hybrid cryptographic protocols aim to combine quantum-resistant algorithms with QKD to ensure secure communication in the post-quantum era.
Conclusion: Choosing Between Quantum and Classical Cryptography
Quantum Key Distribution (QKD) offers unprecedented security by leveraging quantum mechanics to detect eavesdropping, making it theoretically unbreakable, whereas classical public-key encryption relies on computational hardness assumptions vulnerable to future quantum attacks. Organizations must evaluate their security needs, technological maturity, and threat models; QKD is ideal for high-security environments requiring long-term confidentiality, while classical methods remain practical for widespread use due to established infrastructure. Balancing the integration of quantum and classical cryptography ensures robust, future-proof protection against evolving cyber threats.
Quantum Key Distribution vs Public-Key Encryption Infographic
 techiny.com
techiny.com