Access tokens grant temporary access to protected resources, enabling users to interact with web applications without repeatedly logging in. Refresh tokens are used to obtain new access tokens after the original expires, enhancing security by limiting the lifespan of access tokens and reducing the risk of unauthorized access. Proper implementation of both tokens ensures seamless user authentication while maintaining robust security in web development.
Table of Comparison
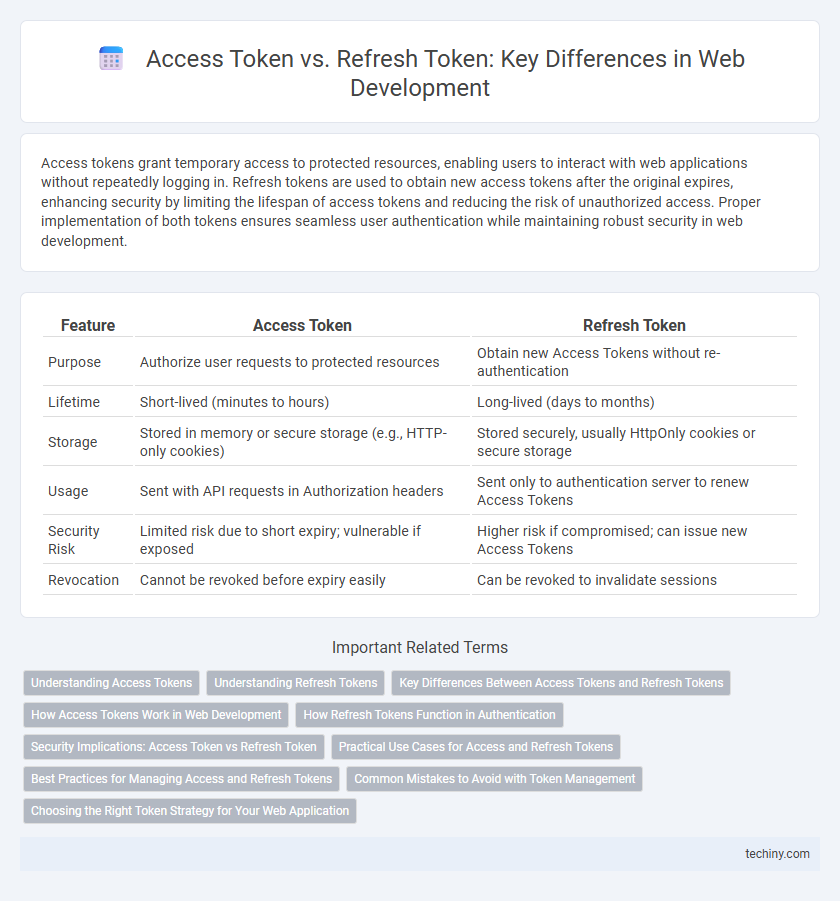
| Feature | Access Token | Refresh Token |
|---|---|---|
| Purpose | Authorize user requests to protected resources | Obtain new Access Tokens without re-authentication |
| Lifetime | Short-lived (minutes to hours) | Long-lived (days to months) |
| Storage | Stored in memory or secure storage (e.g., HTTP-only cookies) | Stored securely, usually HttpOnly cookies or secure storage |
| Usage | Sent with API requests in Authorization headers | Sent only to authentication server to renew Access Tokens |
| Security Risk | Limited risk due to short expiry; vulnerable if exposed | Higher risk if compromised; can issue new Access Tokens |
| Revocation | Cannot be revoked before expiry easily | Can be revoked to invalidate sessions |
Understanding Access Tokens
Access tokens are short-lived credentials used in web development to authenticate client requests securely and grant access to protected resources. These tokens contain encoded user information and permissions, enabling stateless authentication without repeatedly querying the database. Understanding access tokens is crucial for managing session security, as they limit the exposure time of authentication credentials and reduce the risk of unauthorized access.
Understanding Refresh Tokens
Refresh tokens serve as long-lived credentials used to obtain new access tokens without requiring users to reauthenticate, enhancing security and user experience in web development. They typically have extended expiration periods compared to access tokens, allowing continuous access while minimizing exposure to token theft. Proper implementation involves secure storage, rotating refresh tokens, and revocation mechanisms to prevent unauthorized access.
Key Differences Between Access Tokens and Refresh Tokens
Access tokens are short-lived credentials used to authorize user access to protected resources, typically expiring within minutes to hours, while refresh tokens have longer lifespans and are used to obtain new access tokens without requiring user re-authentication. Access tokens contain user permissions and scope information, enabling immediate resource access, whereas refresh tokens primarily serve to maintain sessions and reduce authentication frequency. The security risk of access token exposure is mitigated by their brief validity, but refresh tokens require stronger protection due to their ability to generate new access tokens.
How Access Tokens Work in Web Development
Access tokens in web development act as short-lived credentials that grant clients access to protected resources by validating user permissions within a specific scope. These tokens are typically JSON Web Tokens (JWT) containing encoded user information and expiration timestamps, enabling stateless authentication between clients and servers. By securely transmitting access tokens in HTTP headers, web applications maintain session integrity while reducing the need for frequent authentication requests.
How Refresh Tokens Function in Authentication
Refresh tokens maintain user authentication by securely storing long-lived credentials that request new access tokens once the initial access token expires. They work by being sent to the authorization server, which verifies the refresh token's validity before issuing a fresh access token without requiring the user to re-authenticate. This mechanism enhances session longevity and security by minimizing the exposure time of access tokens and reducing the need for users to frequently log in.
Security Implications: Access Token vs Refresh Token
Access tokens and refresh tokens play distinct roles in web security, with access tokens granting short-lived access to protected resources while refresh tokens enable obtaining new access tokens without re-authenticating. Access tokens are vulnerable to interception and replay attacks if not securely stored and transmitted, necessitating strict expiration and scope limitations. Refresh tokens, typically stored securely on the client side, reduce risk by limiting the exposure of access privileges, but their compromise can allow prolonged unauthorized access, making secure storage and revocation mechanisms critical.
Practical Use Cases for Access and Refresh Tokens
Access tokens grant temporary access to protected resources and APIs, typically with a short expiration time to minimize security risks. Refresh tokens enable users to obtain new access tokens without re-authenticating, supporting seamless session continuity in applications such as single-page apps and mobile clients. Practical use involves using access tokens for frequent API calls while storing refresh tokens securely to renew sessions without compromising user experience.
Best Practices for Managing Access and Refresh Tokens
Store access tokens securely in memory or secure HTTP-only cookies to prevent cross-site scripting (XSS) attacks, while refresh tokens require even stricter safeguards, such as secure storage on the server side or encrypted storage in mobile apps. Implement short-lived access tokens paired with longer-lived refresh tokens to minimize risk exposure, and enforce token rotation on use to reduce the impact of token theft. Always validate tokens on the server, revoke refresh tokens immediately upon suspicious activity, and use scopes and permissions to limit token capabilities.
Common Mistakes to Avoid with Token Management
Common mistakes in token management include storing access and refresh tokens insecurely in local storage or cookies without proper encryption, leading to vulnerability to XSS attacks. Developers often misuse refresh tokens by neglecting to implement expiration and rotation policies, increasing the risk of token theft and unauthorized access. Failing to validate token scopes and audiences during authentication can result in privilege escalation and security breaches.
Choosing the Right Token Strategy for Your Web Application
Choosing the right token strategy for your web application hinges on balancing security and user experience by utilizing access tokens for short-lived, immediate authentication and refresh tokens for obtaining new access tokens without re-authentication. Access tokens are typically stored in memory or secure HTTP-only cookies to minimize exposure, while refresh tokens require stricter storage policies given their longer lifespan and higher risk if compromised. Implementing robust token expiration, rotation, and revocation mechanisms enhances security, ensuring that compromised tokens do not jeopardize user sessions or sensitive data.
Access Token vs Refresh Token Infographic
 techiny.com
techiny.com