Shor's Algorithm exploits quantum computing to efficiently factor large integers, threatening the security foundation of RSA encryption, which relies on the difficulty of this problem. Unlike classical algorithms, Shor's Algorithm can break RSA by solving prime factorization exponentially faster, rendering traditional encryption vulnerable. This quantum advantage compels the development of quantum-resistant cryptographic methods to safeguard data security in the future.
Table of Comparison
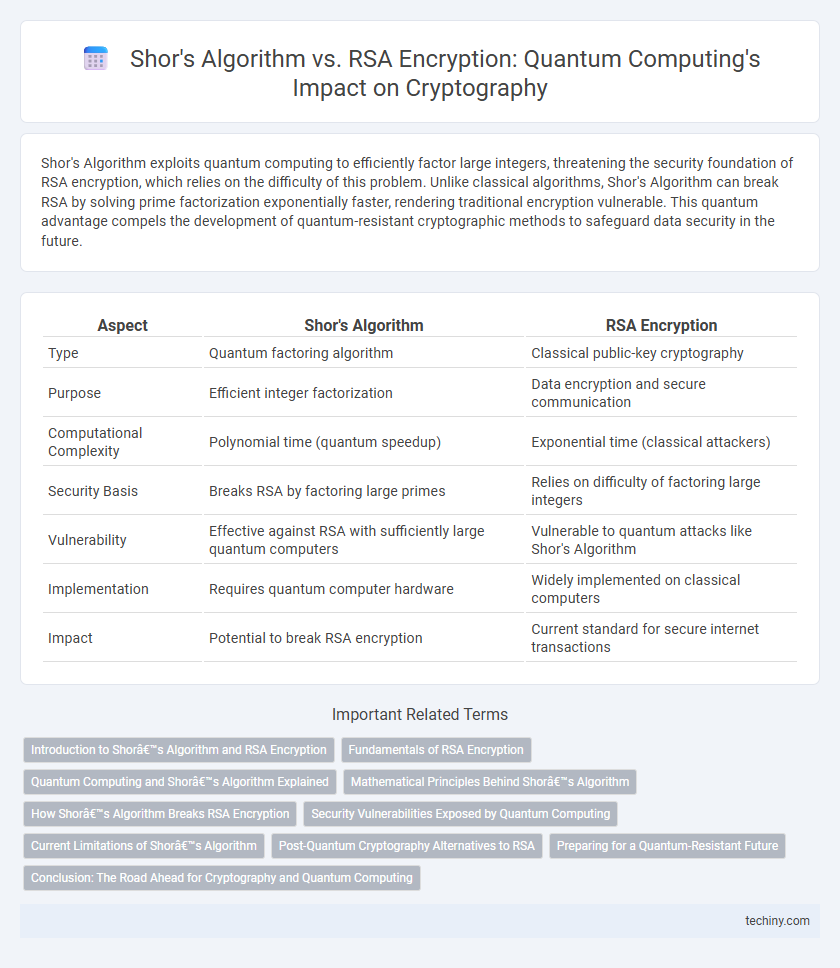
| Aspect | Shor's Algorithm | RSA Encryption |
|---|---|---|
| Type | Quantum factoring algorithm | Classical public-key cryptography |
| Purpose | Efficient integer factorization | Data encryption and secure communication |
| Computational Complexity | Polynomial time (quantum speedup) | Exponential time (classical attackers) |
| Security Basis | Breaks RSA by factoring large primes | Relies on difficulty of factoring large integers |
| Vulnerability | Effective against RSA with sufficiently large quantum computers | Vulnerable to quantum attacks like Shor's Algorithm |
| Implementation | Requires quantum computer hardware | Widely implemented on classical computers |
| Impact | Potential to break RSA encryption | Current standard for secure internet transactions |
Introduction to Shor’s Algorithm and RSA Encryption
Shor's Algorithm is a quantum computing breakthrough designed to efficiently factor large integers, which underpins its potential to compromise RSA encryption by solving problems that classical computers find infeasible. RSA encryption, a widely used public-key cryptosystem, relies on the computational difficulty of factoring the product of two large prime numbers, providing secure data transmission. The development of Shor's Algorithm highlights a critical challenge to RSA's security assumptions, forecasting a significant impact on cryptographic protocols in a post-quantum computing era.
Fundamentals of RSA Encryption
RSA encryption relies on the computational difficulty of factoring large composite numbers, which is the product of two large prime numbers. Its security is based on the practical infeasibility of integer factorization within a reasonable time using classical algorithms. Shor's algorithm, running on a quantum computer, can efficiently factor these large numbers, threatening the foundational security assumption of RSA encryption.
Quantum Computing and Shor’s Algorithm Explained
Shor's Algorithm leverages quantum computing principles to factor large integers exponentially faster than classical methods, directly threatening RSA encryption's security. This algorithm utilizes quantum parallelism and entanglement, enabling efficient prime factorization that classical computers cannot achieve within a practical timeframe. As RSA encryption relies on the difficulty of factorizing large numbers, Shor's Algorithm poses a fundamental challenge to its cryptographic integrity.
Mathematical Principles Behind Shor’s Algorithm
Shor's Algorithm leverages quantum Fourier transform and number theory to factor large integers exponentially faster than classical algorithms, undermining the core mathematical difficulty that secures RSA encryption. By exploiting quantum parallelism and entanglement, it efficiently finds the period of a function related to integer factorization, which classical algorithms struggle to compute within feasible timeframes. This mathematical breakthrough threatens RSA's reliance on the difficulty of prime factorization, prompting urgent advancements in quantum-resistant cryptographic methods.
How Shor’s Algorithm Breaks RSA Encryption
Shor's algorithm exploits the principles of quantum computing to efficiently factor large composite numbers, a task that underpins the security of RSA encryption. By utilizing quantum parallelism and the quantum Fourier transform, Shor's algorithm can determine the prime factors of RSA's large semiprime modulus exponentially faster than classical algorithms. This capability threatens RSA encryption by potentially enabling the extraction of private keys, rendering traditional cryptographic security vulnerable to quantum attacks.
Security Vulnerabilities Exposed by Quantum Computing
Shor's Algorithm leverages quantum computing to efficiently factor large integers, directly threatening the security of RSA encryption, which relies on the difficulty of prime factorization for its cryptographic strength. Quantum computers running Shor's Algorithm can break RSA keys exponentially faster than classical algorithms, rendering traditional public-key infrastructure vulnerable to cryptographic attacks. This exposure highlights the urgent need for quantum-resistant encryption methods to safeguard sensitive data against future quantum threats.
Current Limitations of Shor’s Algorithm
Shor's Algorithm theoretically breaks RSA encryption by efficiently factoring large integers, but its practical implementation faces significant obstacles, primarily the requirement for fault-tolerant quantum computers with thousands of qubits. Current quantum hardware suffers from limited coherence times, high error rates, and insufficient qubit counts, preventing Shor's Algorithm from outperforming classical factoring methods on cryptographically relevant key sizes. Advances in quantum error correction and scalable quantum architectures are needed before Shor's Algorithm can pose a feasible threat to RSA encryption in real-world applications.
Post-Quantum Cryptography Alternatives to RSA
Shor's Algorithm poses a significant threat to RSA encryption by efficiently factoring large integers, rendering classical cryptographic methods vulnerable. Post-quantum cryptography alternatives such as lattice-based schemes, code-based cryptography, and hash-based signatures provide robust security against quantum attacks. Implementations like CRYSTALS-Kyber and CRYSTALS-Dilithium are leading candidates in the NIST PQC standardization process, offering resistance to Shor's Algorithm and ensuring long-term data protection.
Preparing for a Quantum-Resistant Future
Shor's Algorithm poses a significant threat to RSA encryption by efficiently factoring large integers, which underpins RSA's security. As quantum computers advance, cryptographers are developing quantum-resistant algorithms like lattice-based, hash-based, and code-based cryptography to safeguard sensitive data. Preparing for a quantum-resistant future involves transitioning critical systems to post-quantum cryptographic standards mandated by organizations such as NIST.
Conclusion: The Road Ahead for Cryptography and Quantum Computing
Shor's Algorithm poses a significant threat to RSA encryption by efficiently factoring large integers, undermining the security of current cryptographic systems. As quantum computing progresses, conventional encryption methods face increasing vulnerability, prompting urgent development of quantum-resistant algorithms and post-quantum cryptography standards. The future of secure communication depends on the integration of quantum computing advancements with robust, quantum-secure cryptographic solutions.
Shor’s Algorithm vs RSA Encryption Infographic
 techiny.com
techiny.com