Understanding the difference between cross-origin and same-origin policies is crucial for secure web development. Same-origin refers to resources sharing the same protocol, domain, and port, allowing seamless interaction without security restrictions. Cross-origin requests occur when resources come from different origins, often requiring mechanisms like CORS (Cross-Origin Resource Sharing) to safely enable resource sharing while preventing unauthorized access.
Table of Comparison
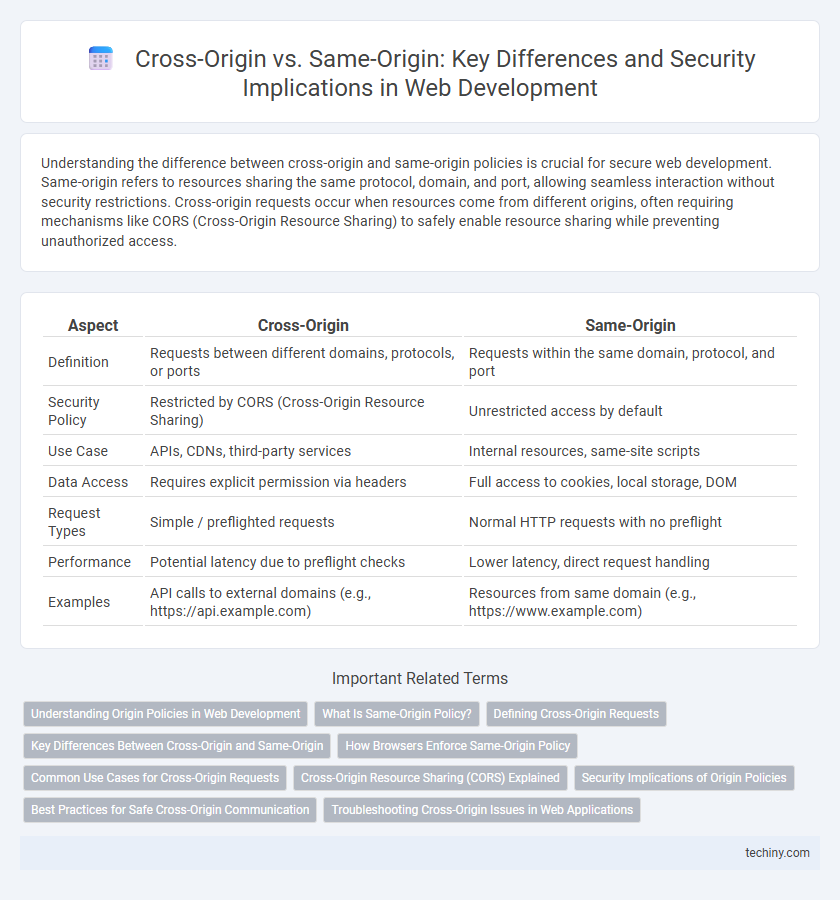
| Aspect | Cross-Origin | Same-Origin |
|---|---|---|
| Definition | Requests between different domains, protocols, or ports | Requests within the same domain, protocol, and port |
| Security Policy | Restricted by CORS (Cross-Origin Resource Sharing) | Unrestricted access by default |
| Use Case | APIs, CDNs, third-party services | Internal resources, same-site scripts |
| Data Access | Requires explicit permission via headers | Full access to cookies, local storage, DOM |
| Request Types | Simple / preflighted requests | Normal HTTP requests with no preflight |
| Performance | Potential latency due to preflight checks | Lower latency, direct request handling |
| Examples | API calls to external domains (e.g., https://api.example.com) | Resources from same domain (e.g., https://www.example.com) |
Understanding Origin Policies in Web Development
Cross-origin and same-origin policies are fundamental security measures that govern how web browsers handle requests between different domains. The same-origin policy restricts web pages from making requests to a different domain than the one that served the original web page, preventing unauthorized data access and ensuring user privacy. Cross-origin resource sharing (CORS) enables controlled access to resources on a different origin by explicitly allowing specific domains, methods, and headers through server-side configuration.
What Is Same-Origin Policy?
Same-Origin Policy is a critical security mechanism implemented in web browsers to restrict scripts on a web page from accessing data on another web page unless both pages share the same origin. The origin is defined by the scheme (protocol), host (domain), and port, ensuring that only resources from identical origins can interact. This policy prevents malicious websites from executing unauthorized actions or stealing sensitive information across different origins, thereby maintaining web security and user privacy.
Defining Cross-Origin Requests
Cross-origin requests occur when a web application requests resources from a different domain, protocol, or port than the one from which it originated, violating the same-origin policy implemented by browsers for security. This policy restricts scripts on a web page from making requests to a different origin, preventing malicious attacks like Cross-Site Request Forgery (CSRF) and data theft. Cross-Origin Resource Sharing (CORS) is a mechanism that allows controlled access to resources on a server from a different origin by using specific HTTP headers to relax the same-origin policy.
Key Differences Between Cross-Origin and Same-Origin
Cross-Origin requests occur when a web application makes a request to a domain different from the one that served the web page, triggering browser security policies like CORS (Cross-Origin Resource Sharing) to control access. Same-Origin policy restricts scripts from accessing data across different origins to prevent malicious behavior, allowing interactions only if protocol, domain, and port are identical. Understanding these differences is crucial for secure API integration and data sharing in web development.
How Browsers Enforce Same-Origin Policy
Browsers enforce the Same-Origin Policy (SOP) by restricting web pages from making requests to a different origin than the one that served the web page, thus isolating potentially malicious content. This policy compares the protocol, domain, and port to determine if two URLs share the same origin, blocking cross-origin interactions unless explicitly permitted by mechanisms like CORS (Cross-Origin Resource Sharing). Enforcement of SOP prevents unauthorized access to sensitive data and protects user sessions by limiting how scripts from distinct origins can interact with each other.
Common Use Cases for Cross-Origin Requests
Cross-origin requests are essential for accessing APIs, loading resources from different domains, and enabling third-party integrations like social media widgets or payment gateways. These requests bypass the Same-Origin Policy by using mechanisms such as CORS headers to securely share data between web applications hosted on different origins. Common use cases include fetching data from cloud services, embedding external content, and enabling microservices architecture in modern web development.
Cross-Origin Resource Sharing (CORS) Explained
Cross-Origin Resource Sharing (CORS) is a security feature implemented by web browsers to control how resources on a web page can be requested from another domain outside the domain from which the resource originated. It allows servers to specify who can access their assets by setting HTTP headers like Access-Control-Allow-Origin, enabling safe and controlled cross-origin requests. Proper CORS configuration is essential for web developers to enable API calls and resource sharing across different domains while maintaining security constraints associated with the same-origin policy.
Security Implications of Origin Policies
Same-Origin Policy enforces strict access controls by allowing scripts on a web page to interact only with resources from the same origin, preventing unauthorized data access and reducing cross-site scripting (XSS) attacks. Cross-Origin Resource Sharing (CORS) provides a controlled relaxation of this policy by enabling secure sharing of resources across different origins through server-defined HTTP headers, minimizing risks like cross-site request forgery (CSRF). Proper configuration of these origin policies is critical for safeguarding user data and maintaining secure communication between web applications and external APIs.
Best Practices for Safe Cross-Origin Communication
Implementing secure cross-origin communication in web development involves strict adherence to the Same-Origin Policy (SOP) to prevent unauthorized data access between different domains. Utilizing Cross-Origin Resource Sharing (CORS) with carefully configured headers like Access-Control-Allow-Origin and Access-Control-Allow-Methods ensures controlled access while minimizing security risks. Employing techniques such as JSONP sparingly and leveraging secure tokens for authentication further reinforces safe data exchange across origins.
Troubleshooting Cross-Origin Issues in Web Applications
Cross-origin issues in web applications often stem from the same-origin policy, which restricts scripts from accessing resources on different domains to enhance security. Troubleshooting these problems involves configuring Cross-Origin Resource Sharing (CORS) headers on the server to allow specific origins or methods. Debugging tools like browser developer consoles can identify blocked requests, while proper setup of Access-Control-Allow-Origin and handling preflight OPTIONS requests ensures smooth cross-origin communication.
Cross-Origin vs Same-Origin Infographic
 techiny.com
techiny.com