OAuth2 is an authorization framework that enables third-party applications to obtain limited access to user accounts, while JWT (JSON Web Token) is a compact token format often used within OAuth2 to securely transmit user information between parties. OAuth2 handles permission scopes and token issuance, whereas JWT ensures the integrity and authenticity of those tokens through digital signatures. Combining OAuth2 with JWT enhances web development security by streamlining user authentication and authorization processes.
Table of Comparison
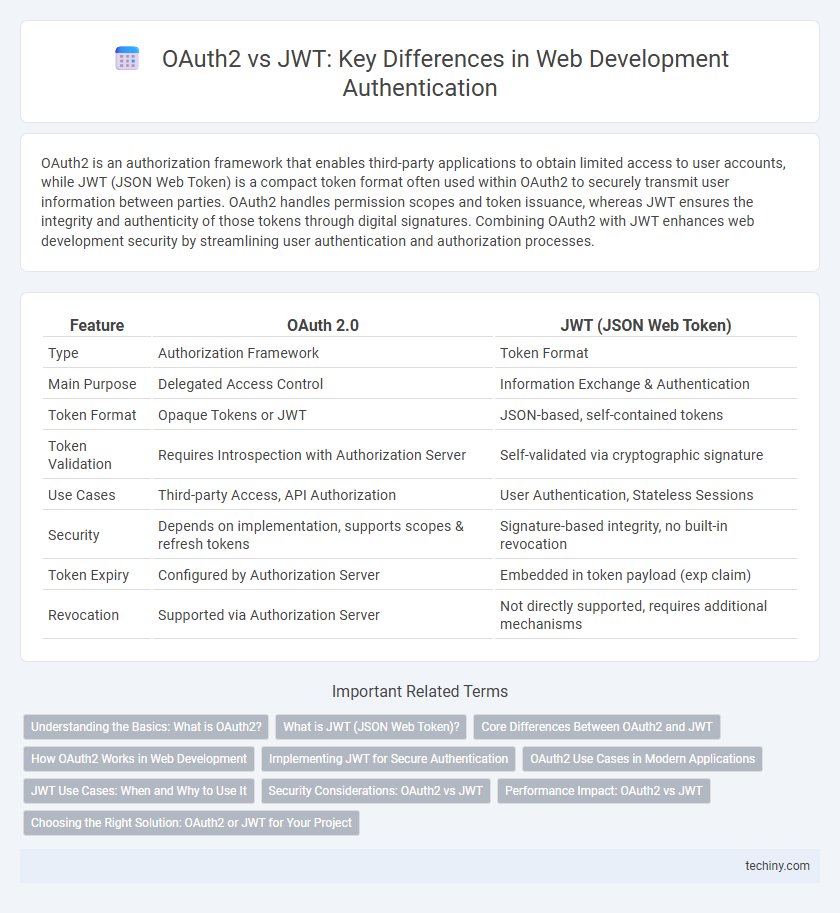
| Feature | OAuth 2.0 | JWT (JSON Web Token) |
|---|---|---|
| Type | Authorization Framework | Token Format |
| Main Purpose | Delegated Access Control | Information Exchange & Authentication |
| Token Format | Opaque Tokens or JWT | JSON-based, self-contained tokens |
| Token Validation | Requires Introspection with Authorization Server | Self-validated via cryptographic signature |
| Use Cases | Third-party Access, API Authorization | User Authentication, Stateless Sessions |
| Security | Depends on implementation, supports scopes & refresh tokens | Signature-based integrity, no built-in revocation |
| Token Expiry | Configured by Authorization Server | Embedded in token payload (exp claim) |
| Revocation | Supported via Authorization Server | Not directly supported, requires additional mechanisms |
Understanding the Basics: What is OAuth2?
OAuth2 is an authorization framework that allows third-party applications to obtain limited access to user resources without exposing credentials. It uses access tokens to grant permissions, enabling secure delegated access across different services and APIs. OAuth2's flexible flows accommodate various client types, making it a cornerstone of modern web authentication and authorization systems.
What is JWT (JSON Web Token)?
JWT (JSON Web Token) is a compact, URL-safe token format used for securely transmitting information between parties as a JSON object. It consists of three parts: a header, payload, and signature, enabling verification of the token's authenticity and integrity. Widely used in authentication and authorization, JWT facilitates stateless, scalable session management in web development environments.
Core Differences Between OAuth2 and JWT
OAuth2 is an authorization framework designed to grant access tokens to third-party applications without exposing user credentials, whereas JWT (JSON Web Token) is a compact token format often used to securely transmit information between parties. OAuth2 defines the process of obtaining and validating tokens, while JWT specifies the structure and encoding of the tokens themselves, facilitating stateless authentication. The core difference lies in OAuth2's role as an authorization protocol versus JWT's function as a lightweight data format for token representation.
How OAuth2 Works in Web Development
OAuth2 operates as an authorization framework that enables third-party applications to obtain limited access to user resources without exposing credentials. It uses access tokens issued by an authorization server after user consent, which the client application uses to access protected resources on a resource server. This separation of roles--client, authorization server, and resource server--enhances security and scalability in web development authentication workflows.
Implementing JWT for Secure Authentication
Implementing JWT for secure authentication enhances web development by providing a compact, URL-safe token format that carries user identity and authorization claims. Unlike OAuth2, which is an authorization framework, JWT enables stateless, self-contained tokens that reduce server load and simplify session management. JWT tokens are signed using algorithms such as HMAC SHA-256 or RSA, ensuring data integrity and protection against tampering during client-server communication.
OAuth2 Use Cases in Modern Applications
OAuth2 is widely used in modern applications to delegate access securely without sharing user credentials, enabling third-party services to access user resources on platforms like social media, cloud storage, and payment gateways. It supports granular permission scopes and token expiration, enhancing security and user control in web and mobile app integrations. Developers leverage OAuth2 for single sign-on (SSO), API authorization, and secure resource sharing across distributed systems.
JWT Use Cases: When and Why to Use It
JWT is ideal for stateless authentication in web applications because it securely transmits user information between parties as a compact, URL-safe token. It is commonly used for single sign-on (SSO), API authentication, and information exchange scenarios where scalability and reduced server overhead are crucial. The token's self-contained nature allows servers to verify requests without database lookups, enhancing performance in distributed systems.
Security Considerations: OAuth2 vs JWT
OAuth2 provides a robust framework for authentication and authorization by delegating user credentials to trusted providers, reducing risks associated with direct credential handling. JWT, as a token format often used within OAuth2, offers stateless and compact token transmission but requires careful implementation to prevent vulnerabilities such as token leakage and replay attacks. Security considerations in OAuth2 vs JWT include token expiration strategies, signature validation, secure storage, and the use of HTTPS to safeguard token integrity and confidentiality.
Performance Impact: OAuth2 vs JWT
OAuth2, primarily an authorization framework, relies on token exchange often involving external validation servers, which can introduce latency and increased server load. JWT (JSON Web Token) enables stateless, self-contained tokens that reduce server requests by embedding user claims, improving performance through faster verification without needing constant database lookups. Consequently, JWT's design often results in lower latency and better scalability compared to OAuth2's traditional token validation processes in web development environments.
Choosing the Right Solution: OAuth2 or JWT for Your Project
OAuth2 provides a robust authorization framework suited for scalable applications requiring delegated access across multiple services, while JWT offers a compact, self-contained token ideal for stateless authentication and information exchange within single applications. Selecting between OAuth2 and JWT depends on project requirements such as the need for centralized access control, token revocation capabilities, and interoperability with third-party APIs. Enterprises prioritizing fine-grained access management typically choose OAuth2, whereas projects demanding efficient, scalable token verification often implement JWT.
Oauth2 vs JWT Infographic
 techiny.com
techiny.com