Active Directory (AD) is a comprehensive directory service developed by Microsoft that manages users, devices, and applications within a Windows domain network, providing authentication, authorization, and policy enforcement. LDAP (Lightweight Directory Access Protocol) serves as a protocol used for querying and modifying directory services, including Active Directory, enabling cross-platform compatibility for directory access. While AD integrates LDAP for directory access, AD extends functionality with additional features like Group Policy and Kerberos authentication, making it a broader identity management solution.
Table of Comparison
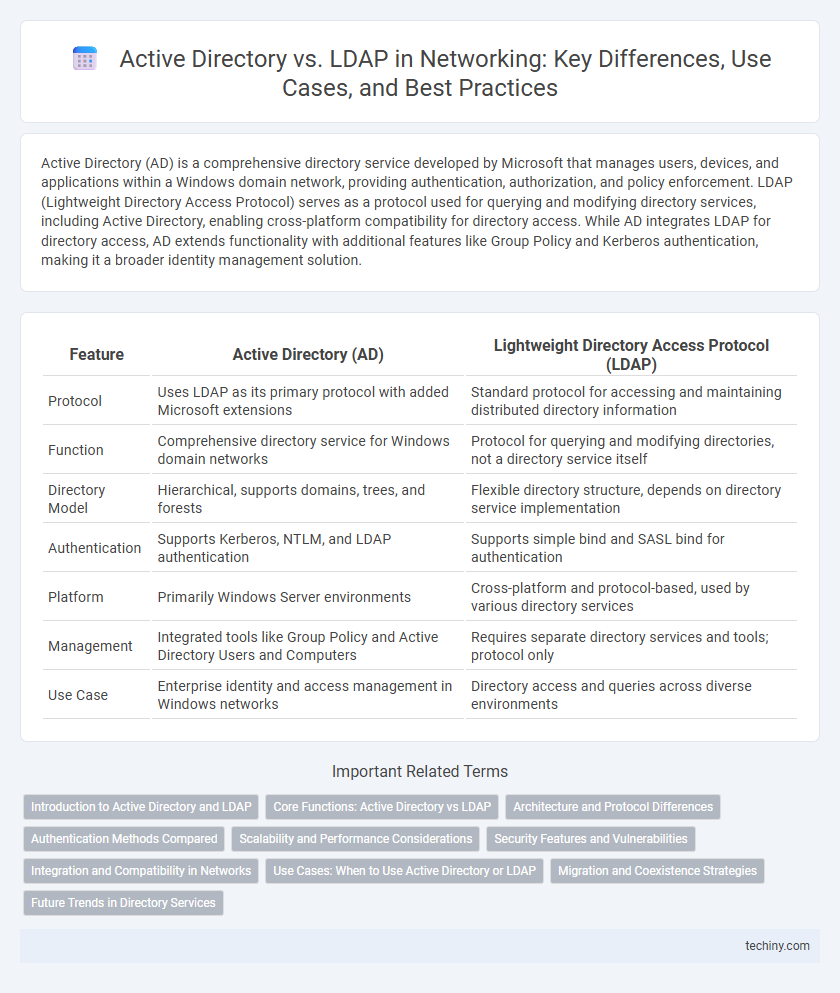
| Feature | Active Directory (AD) | Lightweight Directory Access Protocol (LDAP) |
|---|---|---|
| Protocol | Uses LDAP as its primary protocol with added Microsoft extensions | Standard protocol for accessing and maintaining distributed directory information |
| Function | Comprehensive directory service for Windows domain networks | Protocol for querying and modifying directories, not a directory service itself |
| Directory Model | Hierarchical, supports domains, trees, and forests | Flexible directory structure, depends on directory service implementation |
| Authentication | Supports Kerberos, NTLM, and LDAP authentication | Supports simple bind and SASL bind for authentication |
| Platform | Primarily Windows Server environments | Cross-platform and protocol-based, used by various directory services |
| Management | Integrated tools like Group Policy and Active Directory Users and Computers | Requires separate directory services and tools; protocol only |
| Use Case | Enterprise identity and access management in Windows networks | Directory access and queries across diverse environments |
Introduction to Active Directory and LDAP
Active Directory is a directory service developed by Microsoft that provides centralized management of network resources, user authentication, and policy enforcement within Windows domain networks. LDAP (Lightweight Directory Access Protocol) is an open, vendor-neutral protocol used to access and maintain distributed directory information services across IP networks, including querying user credentials and organizational data. While Active Directory uses LDAP as one of its core protocols, LDAP itself serves as a flexible method to interact with various directory services regardless of the platform.
Core Functions: Active Directory vs LDAP
Active Directory (AD) serves as a comprehensive directory service primarily used for managing Windows domain networks, providing authentication, authorization, and policy enforcement through protocols like Kerberos and LDAP. LDAP (Lightweight Directory Access Protocol) is a protocol designed for querying and modifying directory services, serving as a flexible way to access different directory services including Active Directory. While AD integrates multiple services such as DNS and Group Policy, LDAP focuses solely on directory access and can be used independently or as part of other directory services.
Architecture and Protocol Differences
Active Directory (AD) integrates a range of services including LDAP, Kerberos, and DNS into a cohesive directory service architecture designed primarily for Windows environments. LDAP (Lightweight Directory Access Protocol) is a protocol standard that enables querying and modifying directory services independent of the underlying architecture. AD's architecture extends LDAP by adding features such as replication, Group Policy, and schema enforcement, whereas LDAP serves as a flexible protocol for directory access across diverse systems.
Authentication Methods Compared
Active Directory employs Kerberos and NTLM protocols for secure authentication, offering enhanced encryption and mutual authentication features crucial for Windows environments. LDAP primarily provides a protocol for directory access without built-in authentication but often relies on simple bind or SASL mechanisms, which can vary in security strength. Comparing the two, Active Directory integrates authentication tightly within its ecosystem while LDAP serves as a flexible directory access protocol, often supplemented by external authentication methods.
Scalability and Performance Considerations
Active Directory uses LDAP as its core protocol but offers enhanced scalability through multimaster replication and integrated DNS support, allowing efficient management of large networks. LDAP directories focus on high-speed read operations and simple hierarchical data storage, which improves performance in read-heavy environments but can face challenges scaling write operations. Active Directory's optimization for iterative queries and its caching mechanisms contribute to superior performance in complex enterprise environments compared to basic LDAP implementations.
Security Features and Vulnerabilities
Active Directory (AD) incorporates integrated Kerberos authentication, offering strong encryption and mutual authentication to enhance network security, whereas LDAP primarily relies on simple bind and SASL mechanisms, which can be vulnerable if not properly secured with TLS/SSL. AD enforces fine-grained access control through Group Policy Objects (GPOs) and supports centralized auditing and monitoring, reducing the risk of unauthorized access and facilitating compliance. Conversely, LDAP servers can be susceptible to injection attacks and lack comprehensive built-in security policies, requiring additional configuration and external tools to ensure comparable protection levels.
Integration and Compatibility in Networks
Active Directory seamlessly integrates with Windows-based networks, providing a comprehensive directory service that supports user authentication, authorization, and policy enforcement. LDAP, as an open-standard protocol, offers broad compatibility across various platforms and applications, enabling network devices and services to query and modify directory information regardless of vendor. Organizations leveraging hybrid environments benefit from using Active Directory alongside LDAP to enhance interoperability and centralized identity management.
Use Cases: When to Use Active Directory or LDAP
Active Directory is ideal for managing comprehensive enterprise identity and access management within Windows environments, supporting features like group policies and single sign-on. LDAP is best suited for directory lookup and authentication across heterogeneous systems due to its lightweight protocol and platform independence. Use Active Directory when centralized, scalable user management is required, and LDAP when flexible, cross-platform directory services or custom authentication solutions are needed.
Migration and Coexistence Strategies
Active Directory (AD) and LDAP integration requires strategic planning to ensure seamless migration and coexistence, emphasizing schema compatibility and authentication protocol alignment. Hybrid environments often implement synchronization tools like Microsoft Identity Manager or Azure AD Connect to maintain consistent user attributes and credentials across systems. Careful mapping of LDAP directories to AD objects facilitates phased migration, minimizing downtime and preserving access control integrity.
Future Trends in Directory Services
The future of directory services is shaped by the integration of Active Directory and LDAP with cloud-native technologies, enhancing scalability and hybrid identity management. Emerging trends emphasize decentralized identity frameworks and increased automation through AI-driven policy enforcement, improving security and user experience. Directory services will increasingly support multi-protocol interoperability, enabling seamless access across diverse platforms and accelerating digital transformation initiatives.
Active Directory vs LDAP Infographic
 techiny.com
techiny.com