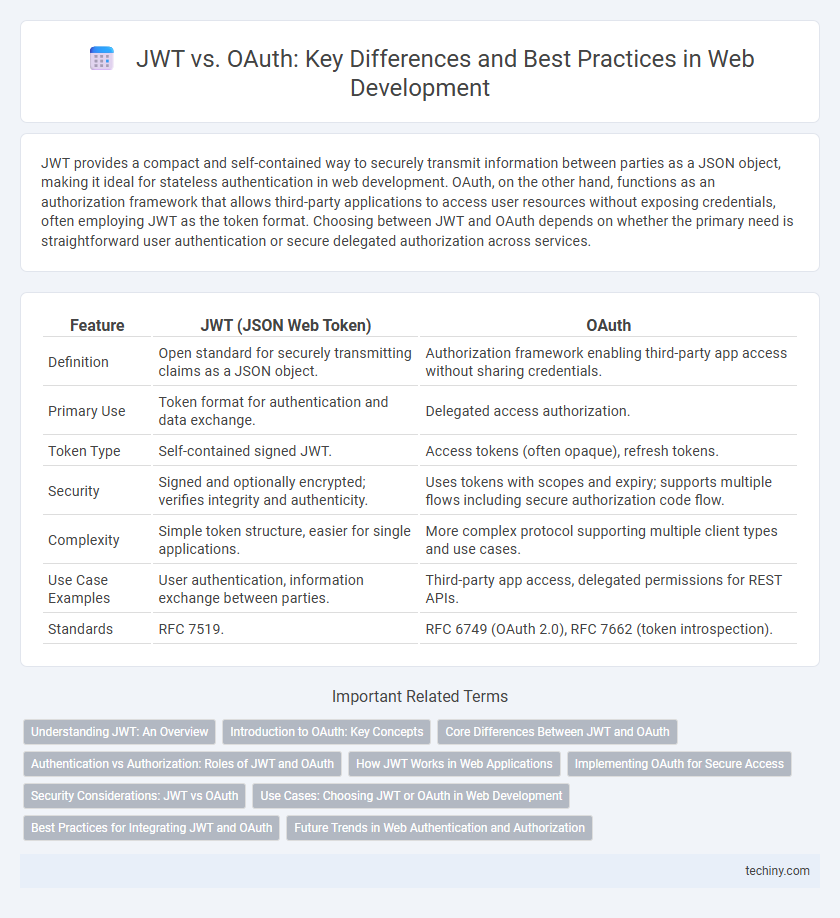
JWT provides a compact and self-contained way to securely transmit information between parties as a JSON object, making it ideal for stateless authentication in web development. OAuth, on the other hand, functions as an authorization framework that allows third-party applications to access user resources without exposing credentials, often employing JWT as the token format. Choosing between JWT and OAuth depends on whether the primary need is straightforward user authentication or secure delegated authorization across services.
Table of Comparison
| Feature | JWT (JSON Web Token) | OAuth |
|---|---|---|
| Definition | Open standard for securely transmitting claims as a JSON object. | Authorization framework enabling third-party app access without sharing credentials. |
| Primary Use | Token format for authentication and data exchange. | Delegated access authorization. |
| Token Type | Self-contained signed JWT. | Access tokens (often opaque), refresh tokens. |
| Security | Signed and optionally encrypted; verifies integrity and authenticity. | Uses tokens with scopes and expiry; supports multiple flows including secure authorization code flow. |
| Complexity | Simple token structure, easier for single applications. | More complex protocol supporting multiple client types and use cases. |
| Use Case Examples | User authentication, information exchange between parties. | Third-party app access, delegated permissions for REST APIs. |
| Standards | RFC 7519. | RFC 6749 (OAuth 2.0), RFC 7662 (token introspection). |
Understanding JWT: An Overview
JSON Web Token (JWT) is a compact, URL-safe means of representing claims to be transferred between two parties, often used for authentication and information exchange in web development. JWT consists of three parts: a header, payload, and signature, enabling secure transmission of data through digitally signed tokens. Its stateless nature allows servers to verify user identity without maintaining session information, enhancing scalability in distributed systems.
Introduction to OAuth: Key Concepts
OAuth is an open-standard authorization protocol enabling third-party applications to access user resources without exposing credentials. It uses access tokens to grant limited permissions, improving security in web development. OAuth's key concepts include resource owner, client, authorization server, and resource server, forming the foundation for delegated authorization.
Core Differences Between JWT and OAuth
JWT (JSON Web Token) is a compact, URL-safe token format used primarily for securely transmitting information between parties as a JSON object, often employed for authentication and information exchange. OAuth is an authorization framework that enables third-party applications to obtain limited access to user resources without exposing credentials, using tokens like JWT as a format within its flows. The core difference lies in JWT being a token standard, while OAuth is a protocol that can use JWTs to grant delegated access securely.
Authentication vs Authorization: Roles of JWT and OAuth
JWT (JSON Web Token) primarily functions as a compact, self-contained token used for authentication by securely transmitting user identity information between parties. OAuth serves as an authorization framework that grants limited access permissions to third-party applications without sharing user credentials. While JWT can be used within OAuth flows to represent authorization scopes, OAuth defines how and when access is granted, distinguishing its core role in authorization from JWT's focus on authentication.
How JWT Works in Web Applications
JWT (JSON Web Token) securely transmits information between parties as a compact, URL-safe token containing a JSON payload digitally signed using algorithms like HMAC SHA-256 or RSA. In web applications, upon user authentication, the server generates a JWT containing claims about the user's identity and privileges, which the client stores (often in localStorage or cookies) and includes in subsequent HTTP headers for stateless authorization. This mechanism allows servers to verify token integrity and user authenticity without maintaining session state, enhancing scalability and performance in distributed web environments.
Implementing OAuth for Secure Access
Implementing OAuth for secure access in web development involves delegating user authentication to a trusted authorization server, which issues access tokens to client applications. OAuth enhances security by enabling scoped and time-limited access tokens, reducing the risk of exposing user credentials compared to JWT alone. Integrating OAuth with JSON Web Tokens (JWT) allows developers to create robust authorization flows that protect APIs from unauthorized access.
Security Considerations: JWT vs OAuth
JWT (JSON Web Token) provides a compact and self-contained way for secure information exchange but is vulnerable to token theft and replay attacks if not properly secured with HTTPS and short expiration times. OAuth, as an authorization framework, enhances security by delegating access via access tokens with limited scope and lifespan, reducing risks associated with credential exposure. Implementing OAuth with JWT tokens can combine benefits, leveraging JWT's statelessness while maintaining OAuth's robust access control and revocation capabilities.
Use Cases: Choosing JWT or OAuth in Web Development
JWT (JSON Web Token) is ideal for stateless authentication in single-page applications and microservices, providing secure token-based user verification without server-side session storage. OAuth excels in delegated authorization, enabling third-party access to user resources across platforms without sharing credentials, commonly used in social login integrations and API permissions. Selecting between JWT and OAuth hinges on whether the application requires simple authentication or complex authorization workflows involving multiple services or external systems.
Best Practices for Integrating JWT and OAuth
Integrating JWT and OAuth effectively requires using JWT as the token format within the OAuth 2.0 authorization framework to enhance security and scalability. Best practices include implementing short-lived JWT access tokens with refresh tokens to minimize exposure risk and using robust signature algorithms like RS256 to ensure token integrity. Proper token validation, secure storage, and adherence to scopes and claims in OAuth policies optimize authorization flows and protect APIs from unauthorized access.
Future Trends in Web Authentication and Authorization
JWT and OAuth continue to evolve as foundational protocols for web authentication and authorization, with emerging trends emphasizing decentralized identity and enhanced security through token encryption. The adoption of machine learning algorithms is improving anomaly detection in authentication flows, reducing fraud and unauthorized access. Future web development frameworks are integrating seamless multi-factor authentication and adaptive authorization, ensuring scalable and user-centric security models.
JWT vs OAuth Infographic
 techiny.com
techiny.com