Fail-safe systems prioritize safety by defaulting to a secure state that prevents harm or damage in case of failure, often by shutting down or entering a safe mode. Fail-secure designs focus on maintaining security measures even during faults, ensuring that access or control mechanisms remain protected against unauthorized use. Choosing between fail-safe and fail-secure depends on whether the primary concern is safety or security in the hardware engineering application.
Table of Comparison
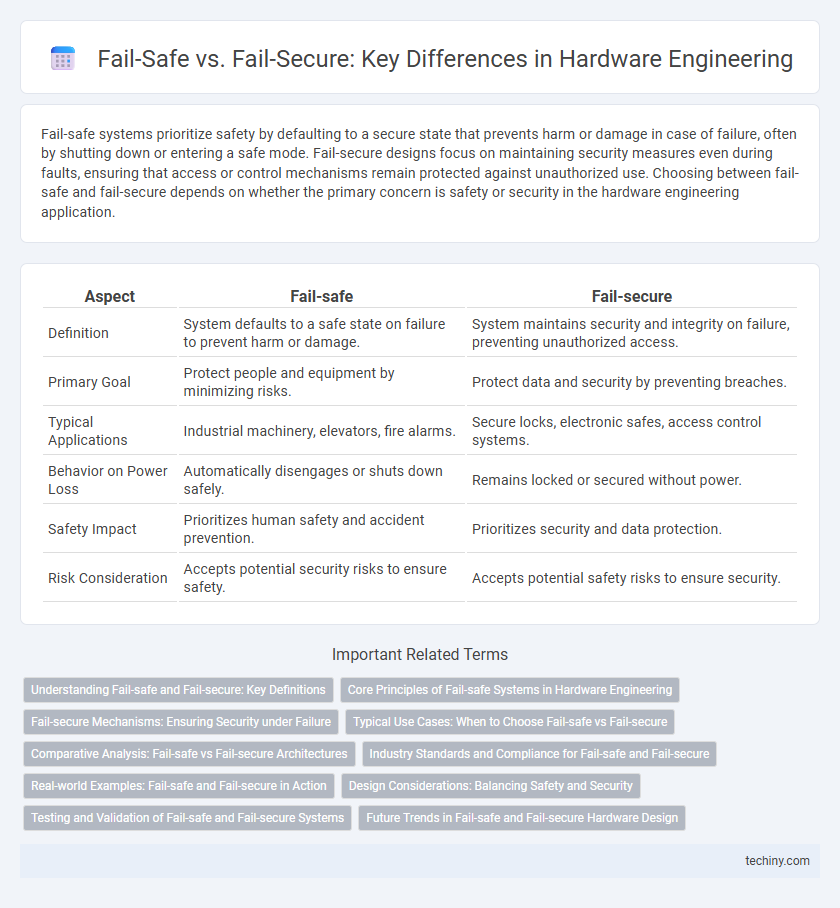
| Aspect | Fail-safe | Fail-secure |
|---|---|---|
| Definition | System defaults to a safe state on failure to prevent harm or damage. | System maintains security and integrity on failure, preventing unauthorized access. |
| Primary Goal | Protect people and equipment by minimizing risks. | Protect data and security by preventing breaches. |
| Typical Applications | Industrial machinery, elevators, fire alarms. | Secure locks, electronic safes, access control systems. |
| Behavior on Power Loss | Automatically disengages or shuts down safely. | Remains locked or secured without power. |
| Safety Impact | Prioritizes human safety and accident prevention. | Prioritizes security and data protection. |
| Risk Consideration | Accepts potential security risks to ensure safety. | Accepts potential safety risks to ensure security. |
Understanding Fail-safe and Fail-secure: Key Definitions
Fail-safe systems are designed to default to a safe state in the event of a failure, preventing harm or damage by prioritizing safety above all else. Fail-secure systems maintain security during failure, ensuring that unauthorized access or data breaches are prevented even if the system stops functioning properly. Understanding these key definitions is crucial in hardware engineering for designing systems that balance safety and security based on specific application requirements.
Core Principles of Fail-safe Systems in Hardware Engineering
Fail-safe systems in hardware engineering prioritize preventing hazardous outcomes by ensuring that any failure leads to a safe state, typically by defaulting to shutdown or deactivation modes. These systems rely on redundancy, continuous monitoring, and control mechanisms that automatically activate safety protocols when faults are detected. The core principle centers on minimizing risk to users and equipment by allowing controlled failure without compromising safety, contrasting with fail-secure designs that prioritize security over safety during faults.
Fail-secure Mechanisms: Ensuring Security under Failure
Fail-secure mechanisms maintain system security by ensuring that, during a failure, access remains restricted and protected data is not compromised. These hardware designs prioritize preserving confidentiality and integrity, often defaulting to locked or inaccessible states to prevent unauthorized entry. Critical applications such as secure access control and banking systems implement fail-secure components to guard against security breaches even when faults occur.
Typical Use Cases: When to Choose Fail-safe vs Fail-secure
Fail-safe systems are typically chosen for applications where human safety is the primary concern, such as in emergency power-off switches and industrial machinery controls, ensuring equipment defaults to a safe state during faults. Fail-secure systems are preferred in security-critical environments, like data centers and electronic locks, where maintaining protection and preventing unauthorized access during failures is essential. Selecting between fail-safe and fail-secure depends on balancing the priorities of safety versus security in hardware engineering design.
Comparative Analysis: Fail-safe vs Fail-secure Architectures
Fail-safe architectures prioritize safety by ensuring a system transitions to a safe state during a failure, minimizing harm but potentially sacrificing functionality. Fail-secure designs maintain security by keeping systems locked or inaccessible during failures, preventing unauthorized access but possibly hindering emergency operations. Comparing these approaches highlights trade-offs between operational safety and security requirements in hardware engineering, influencing design choices based on risk assessment and application context.
Industry Standards and Compliance for Fail-safe and Fail-secure
Industry standards such as IEC 61508 and ISO 13849 define requirements for fail-safe and fail-secure hardware systems to ensure operational safety and security in engineering applications. Fail-safe designs prioritize automatic safe shutdown or neutral state upon failure, adhering to safety compliance regulations critical in industries like automotive and aerospace. Fail-secure implementations focus on maintaining system security during faults, complying with cybersecurity frameworks such as Common Criteria (ISO/IEC 15408) for protecting sensitive hardware components in sectors including defense and data centers.
Real-world Examples: Fail-safe and Fail-secure in Action
Fail-safe systems, such as elevator brakes and railway signaling, prioritize safety by defaulting to a safe state during failure, preventing harm to users. Fail-secure designs, exemplified by electronic door locks and data center access controls, maintain security by restricting access or locking down in the event of a fault. Real-world implementation of fail-safe and fail-secure mechanisms depends on whether safety or security has higher priority in the specific hardware engineering context.
Design Considerations: Balancing Safety and Security
Fail-safe and fail-secure design considerations prioritize different system responses during failures, where fail-safe prioritizes safety by ensuring systems default to a harmless state, whereas fail-secure emphasizes security by maintaining protective measures even under fault conditions. Hardware engineers must balance the risk of potential hazards against unauthorized access by integrating redundancy, fault tolerance, and robust authentication mechanisms tailored to the specific operational environment. Strategic selection between fail-safe and fail-secure designs hinges on application criticality, regulatory compliance, and the likelihood of failure scenarios impacting safety or security.
Testing and Validation of Fail-safe and Fail-secure Systems
Testing and validation of fail-safe systems focus on ensuring that hardware components default to a safe state during failure, emphasizing robust fault detection and controlled shutdown procedures. Fail-secure system validation requires verifying that sensitive data and system integrity remain protected under fault conditions, prioritizing secure state maintenance even at the expense of availability. Both approaches use rigorous fault injection testing and formal verification to guarantee compliance with safety and security standards in hardware engineering.
Future Trends in Fail-safe and Fail-secure Hardware Design
Future trends in fail-safe and fail-secure hardware design emphasize integration of advanced AI-driven diagnostics and adaptive control mechanisms to enhance system resilience and reliability. Emerging technologies like quantum-safe cryptography and machine learning algorithms enable proactive fault detection and security breach prevention in critical hardware components. Enhanced sensor fusion and real-time monitoring platforms are expected to drive the evolution of intelligent fail-safe architectures, minimizing downtime and mitigating risks from cyber-physical attacks.
Fail-safe vs Fail-secure Infographic
 techiny.com
techiny.com