A data breach involves unauthorized access to confidential information, often resulting from hackers exploiting security vulnerabilities, whereas a data leak occurs when sensitive data is exposed unintentionally due to misconfigurations or human error. Data breaches typically indicate active malicious attacks aiming to steal or manipulate data, while data leaks reflect passive exposure without necessarily involving external intrusions. Both scenarios compromise data integrity and privacy, demanding rigorous cybersecurity measures to prevent unauthorized disclosure and mitigate potential damages.
Table of Comparison
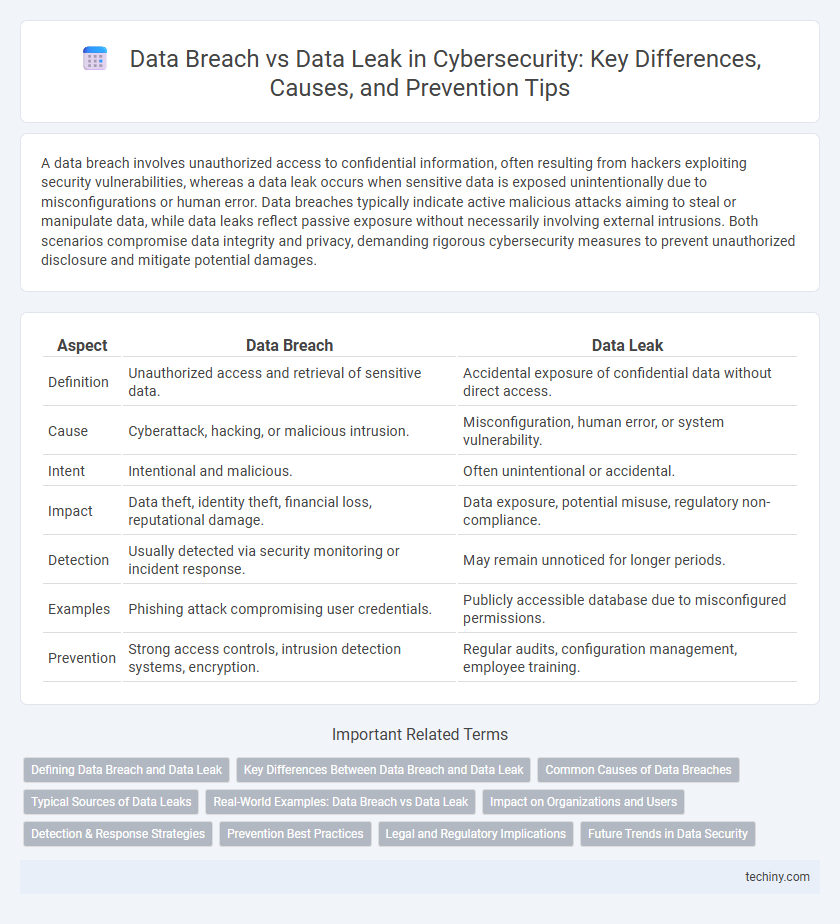
| Aspect | Data Breach | Data Leak |
|---|---|---|
| Definition | Unauthorized access and retrieval of sensitive data. | Accidental exposure of confidential data without direct access. |
| Cause | Cyberattack, hacking, or malicious intrusion. | Misconfiguration, human error, or system vulnerability. |
| Intent | Intentional and malicious. | Often unintentional or accidental. |
| Impact | Data theft, identity theft, financial loss, reputational damage. | Data exposure, potential misuse, regulatory non-compliance. |
| Detection | Usually detected via security monitoring or incident response. | May remain unnoticed for longer periods. |
| Examples | Phishing attack compromising user credentials. | Publicly accessible database due to misconfigured permissions. |
| Prevention | Strong access controls, intrusion detection systems, encryption. | Regular audits, configuration management, employee training. |
Defining Data Breach and Data Leak
Data breach refers to an incident where unauthorized individuals gain access to confidential, sensitive, or protected information, often resulting from cyberattacks or system vulnerabilities. Data leak involves the unintentional exposure or release of private data to an unsecured environment, without necessarily involving malicious hacking. Understanding these distinctions is essential for implementing effective cybersecurity measures and protecting organizational assets.
Key Differences Between Data Breach and Data Leak
A data breach involves unauthorized access to sensitive information, often through hacking or cyberattacks, compromising system security and exposing confidential data. In contrast, a data leak typically occurs due to accidental exposure or misconfiguration, where data becomes publicly accessible without direct hacking. Understanding these distinctions enhances cybersecurity strategies by emphasizing prevention against external attacks and internal data handling errors.
Common Causes of Data Breaches
Common causes of data breaches include phishing attacks, weak or stolen passwords, unpatched software vulnerabilities, and insider threats such as employee negligence or malicious actions. Organizations often experience breaches due to inadequate security measures, including poor access controls and lack of encryption. Understanding these factors helps improve cybersecurity defenses and reduce the risk of unauthorized data exposure.
Typical Sources of Data Leaks
Typical sources of data leaks include unsecured cloud storage, misconfigured databases, and insider threats such as employees inadvertently sharing sensitive information. Vulnerabilities in third-party software and phishing attacks also frequently expose critical data. Identifying and securing these entry points is essential to prevent unauthorized access and protect organizational assets.
Real-World Examples: Data Breach vs Data Leak
The 2017 Equifax data breach exposed sensitive information of over 147 million individuals due to a failure in patching a known vulnerability, demonstrating how attackers exploit system weaknesses to steal data directly. In contrast, a data leak occurred in 2019 when unsecured AWS cloud storage exposed more than 540 million records from various companies without hacking, highlighting misconfigured security controls as a primary cause. These real-world incidents emphasize the critical difference between malicious data breaches and inadvertent data leaks in cybersecurity risk management.
Impact on Organizations and Users
Data breaches often result in unauthorized access to confidential information, causing significant financial losses and reputational damage for organizations. Data leaks typically involve accidental exposure of sensitive data, which can still compromise user privacy and lead to regulatory penalties. Both incidents undermine trust, disrupt operations, and necessitate costly response and remediation efforts.
Detection & Response Strategies
Data breach detection relies heavily on continuous network monitoring, intrusion detection systems (IDS), and anomaly detection algorithms to promptly identify unauthorized access or data exfiltration. Response strategies prioritize incident containment through isolating affected systems, forensic analysis to determine breach scope, and regulatory notification compliance. Data leak detection often utilizes data loss prevention (DLP) tools, user behavior analytics (UBA), and endpoint security solutions to prevent accidental or malicious exposure, while response involves data classification reviews, access control tightening, and employee awareness training to mitigate recurrence.
Prevention Best Practices
Data breach prevention relies on robust encryption, multi-factor authentication, and regular security audits to protect sensitive information from unauthorized access. Data leak prevention focuses on monitoring data movement, enforcing strict access controls, and implementing data loss prevention (DLP) solutions to detect and block accidental or intentional exposure. Combining these best practices minimizes risks by securing data integrity, confidentiality, and availability across the network.
Legal and Regulatory Implications
Data breaches often trigger mandatory reporting requirements under regulations such as GDPR, HIPAA, and CCPA, exposing organizations to significant legal penalties and compliance audits. Data leaks, while sometimes inadvertent and less malicious, can still result in regulatory scrutiny and litigation due to inadequate data protection measures. Understanding the distinction is crucial for implementing appropriate incident response and fulfilling legal obligations to protect sensitive information and maintain organizational compliance.
Future Trends in Data Security
Emerging trends in data security emphasize advanced threat detection technologies such as AI-driven anomaly detection to differentiate between intentional data breaches and accidental data leaks. Encryption methods and zero-trust architectures are increasingly adopted to mitigate risks associated with both breaches and leaks, ensuring robust protection of sensitive information. Future strategies also prioritize real-time monitoring and automated response systems to minimize exposure time and potential damage from unauthorized data access.
Data Breach vs Data Leak Infographic
 techiny.com
techiny.com